
- Email support@dumps4free.com

Topic 3: Exam Pool C
A security analyst needs to determine how an attacker was able to use User3 to gain a
foothold within a company's network. The company's lockout policy requires that an
account be locked out for a minimum of 15 minutes after three unsuccessful attempts.
While reviewing the log files, the analyst discovers the following:
Which of the following attacks MOST likely occurred?
A. Dictionary
B. Credential-stuffing
C. Password-spraying
D. Brute-force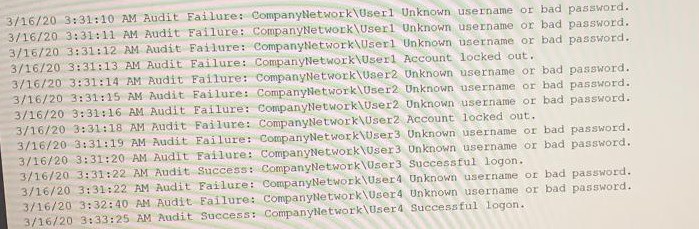
Which of the following attacks MOST likely occurred?
A.
Dictionary
B.
Credential-stuffing
C.
Password-spraying
D.
Brute-force
Brute-force
Which of the following relets to applications and systems that are used within an
organization without consent or approval?
A.
Shadow IT
B.
ONT
C.
Dark web
D.
Insider threats
Shadow IT
A Chief Executive Officer's (CEO) personal information was stolen in a social engineering attack. Which of the following sources would reveal if the CEO's personal information is for sale?
A.
Automated information sharing
B.
Open-source intelligence
C.
The dark web
D.
Vulnerability databases
The dark web
A security administrator currently spends a large amount of time on common security tasks, such aa report generation, phishing investigations, and user provisioning and
deprovisioning This prevents the administrator from spending time on other security
projects. The business does not have the budget to add more staff members. Which of the
following should the administrator implement?
A.
A. DAC
B.
B. ABAC
C.
C. SCAP
D.
SOAR
SOAR
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site Upon investigation, a security analyst the identifies the following:
• The legitimate websites IP address is 10.1.1.20 and eRecruit local resolves to the IP
• The forged website's IP address appears to be 10.2.12.99. based on NetFtow records
• AH three at the organization's DNS servers show the website correctly resolves to the
legitimate IP
• DNS query logs show one of the three DNS servers returned a result of 10.2.12.99
(cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
A.
A reverse proxy was used to redirect network traffic
B.
An SSL strip MITM attack was performed
C.
An attacker temporarily pawned a name server
D.
An ARP poisoning attack was successfully executed
An SSL strip MITM attack was performed
| Page 9 out of 178 Pages |
| Previous |