
- Email support@dumps4free.com

Topic 3: Exam Pool C
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
A.
Something you know
B.
Something you have
C.
Somewhere you are
D.
Someone you are
E.
Something you are
F.
Something you can do
Something you know
Something you have
Which of the following is MOST likely to contain ranked and ordered information on the
likelihood and potential impact of catastrophic events that may affect business processes
and systems, while also highlighting the residual risks that need to be managed after
mitigating controls have been implemented?
A.
An RTO report
B.
A risk register
C.
business impact analysis
D.
An asset value register
E.
A disaster recovery plan
A risk register
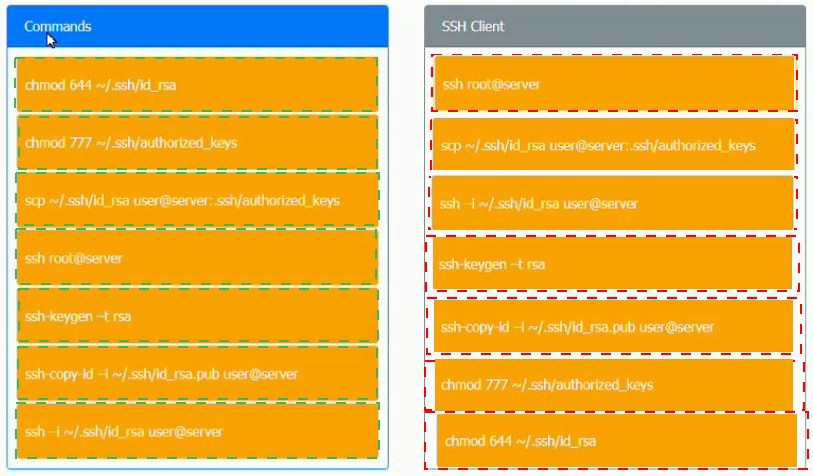
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.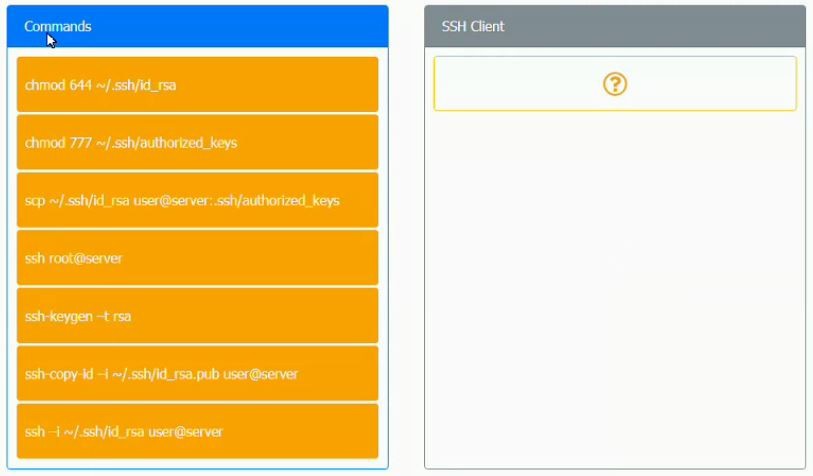
Joe, an employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm Joe’s identity before sending him the prize. Which of the following BEST describes this type of email?
A.
Spear phishing
B.
Whaling
C.
Phishing
D.
Vishing
Phishing
A security analyst is performing a forensic investigation compromised account credentials. Using the Event Viewer, the analyst able to detect the following message, ‘’Special privileges assigned to new login.’’ Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
A.
Pass-the-hash
B.
Buffer overflow
C.
Cross-site scripting
D.
Session replay
Pass-the-hash
| Page 13 out of 178 Pages |
| Previous |