
- Email support@dumps4free.com

Topic 3: Exam Pool C
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
A.
SDP
B.
AAA
C.
IaaS
D.
MSSP
E.
Microservices
MSSP
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events: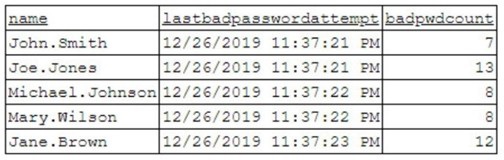
To better understand what is going on, the analyst runs a command and receives the
following output:
Based on the analyst’s findings, which of the following attacks is being executed?
A.
Credential harvesting
B.
Keylogger
C.
Brute-force
D.
Spraying
Spraying
A security engineer is reviewing log files after a third discovered usernames and passwords for the organization’s accounts. The engineer sees there was a change in the IP address for a vendor website one earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
A.
Man-in- the middle
B.
Spear-phishing
C.
Evil twin
D.
DNS poising
DNS poising
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to
any external networks. Which of the following methods would BEST prevent the exfiltration of data? (Select TWO).
A.
VPN
B.
Drive encryption
C.
Network firewall
D.
File level encryption
E.
USB blocker
F.
MFA
Drive encryption
USB blocker
A security administrator suspects an employee has been emailing proprietary information to a competitor. Company policy requires the administrator to capture an exact copy of the employee’s hard disk. Which of the following should the administrator use?
A.
dd
B.
chmod
C.
dnsenum
D.
logger
dd
| Page 11 out of 178 Pages |
| Previous |