
- Email support@dumps4free.com

Topic 1: Exam Pool A
desc about topic
An email user has been lured into clicking a link in an email sent by their company's
security organization. The webpage that opens reports that it was safe but the link could
have contained malicious code. Which type of security program is in place?
A.
Physical access control
B.
Social engineering attack
C.
brute force attack
D.
user awareness
user awareness
Explanation: This is a training program which simulates an attack, not a real attack (as it
says “The webpage that opens reports that it was safe”) so we believed it should be called
a “user awareness” program.Therefore the best answer here should be “user awareness”.
This is the definition of“User awareness” from CCNA 200- 301 Offical Cert Guide
Book:“User awareness: All users should be made aware of the need for data confidentiality
to protect corporate information, as well as their own credentials and personal information.
They should also be made aware of potential threats, schemes to mislead, and proper
procedures to report security incidents. ” Note: Physical access control means
infrastructure locations, such as network closets and data centers, should remain securely
locked.
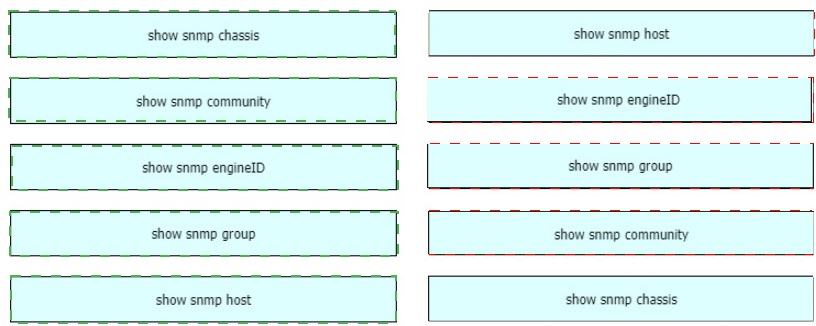
Drag and drop the SNMP manager and agent identifier commands from the left onto the
functions on the right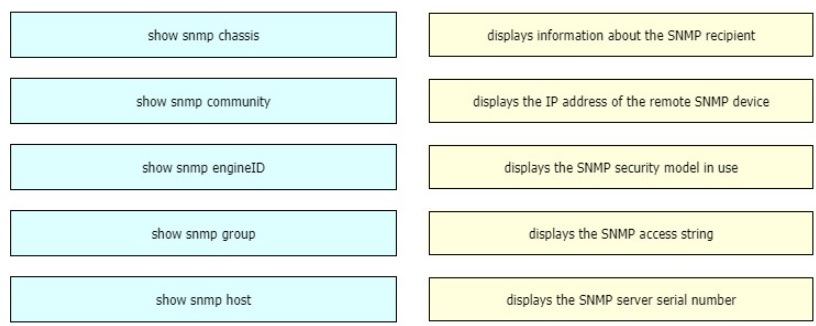
Which protocol does an IPv4 host use to obtain a dynamically assigned IP address?
A.
ARP
B.
DHCP
C.
CDP
D.
DNS
DHCP
Which switch technology establishes a network connection immediately when it is plugged
in?
A.
PortFast
B.
BPDU guard
C.
UplinkFast
D.
BackboneFast
PortFast
Explanation: PortFast is useful to connect hosts and switches to a switch. Access layer
switches are more frequently “plugged in” and “plugged out” than distribution or core layer
switches. Also, this feature’s target is just to minimize STP convergence time.
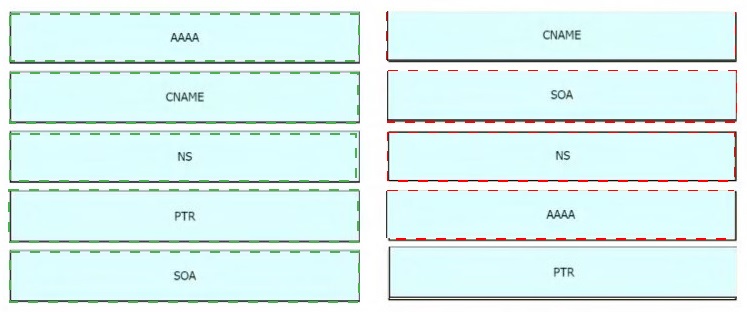
Drag the IPv6 DNS record types from the left onto the description on the right.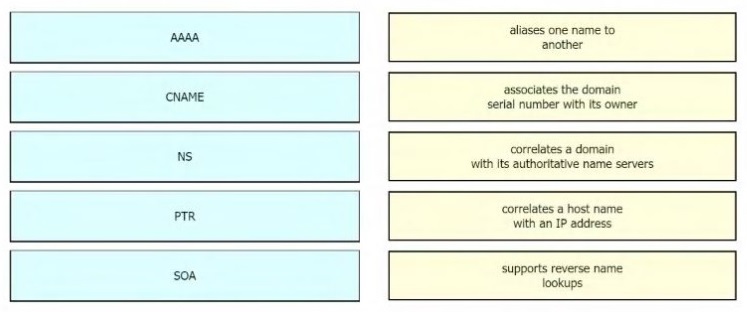
| Page 10 out of 173 Pages |
| Previous |