Question # 1
| What action is required to enable forwarder management in Splunk Web? |
| A. Navigate to Settings > Server Settings > General Settings, and set an App server port.
| | B. Navigate to Settings > Forwarding and receiving, and click on Enable Forwarding.
| | C. Create a server class and map it to a client
inSPLUNK_HOME/etc/system/local/serverclass.conf.
| | D. Place an app in theSPLUNK_HOME/etc/deployment-appsdirectory of the deployment
server. |
C. Create a server class and map it to a client
inSPLUNK_HOME/etc/system/local/serverclass.conf.
"To activate deployment server, you must place at least one app into
%SPLUNK_HOME%\etc\deployment-apps on the host you want to act as deployment
server. In this case, the app is the "send to indexer" app you created earlier, and the host is
the indexer you set up initially."
Question # 2
| Which Splunk component requires a Forwarder license? |
| A. Search head
| | B. Heavy forwarder
| | C. Heaviest forwarder
| | D. Universal forwarder |
B. Heavy forwarder
Question # 3
| An admin is running the latest version of Splunk with a 500 GB license. The current daily
volume of new data
is 300 GB per day. To minimize license issues, what is the best way to add 10 TB of
historical data to the
index? |
| A. Buy a bigger Splunk license.
| | B. Add 2.5 TB each day for the next 5 days.
| | C. Add all 10 TB in a single 24 hour period.
| | D. Add 200 GB of historical data each day for 50 days. |
C. Add all 10 TB in a single 24 hour period.
"An Enterprise license stack with a license volume of 100 GB of data per day or more does
not currently violate."
Question # 4
| A security team needs to ingest a static file for a specific incident. The log file has not been
collected previously and future updates to the file must not be indexed.
Which command would meet these needs? |
| A. splunk add one shot / opt/ incident [data .log —index incident
| | B. splunk edit monitor /opt/incident/data.* —index incident
| | C. splunk add monitor /opt/incident/data.log —index incident
| | D. splunk edit oneshot [opt/ incident/data.* —index incident |
A. splunk add one shot / opt/ incident [data .log —index incident
Explanation:
The correct answer is A. splunk add one shot / opt/ incident [data . log —index incident
According to the Splunk documentation1, the splunk add one shot command adds a single
file or directory to the Splunk index and then stops monitoring it. This is useful for ingesting
static files that do not change or update. The command takes the following syntax:
splunk add one shot -index
The file parameter specifies the path to the file or directory to be indexed. The index
parameter specifies the name of the index where the data will be stored. If the index does not exist, Splunk will create it automatically.
Option B is incorrect because the splunk edit monitor command modifies an existing
monitor input, which is used for ingesting files or directories that change or update over
time. This command does not create a new monitor input, nor does it stop monitoring after
indexing.
Option C is incorrect because the splunk add monitor command creates a new monitor
input, which is also used for ingesting files or directories that change or update over time.
This command does not stop monitoring after indexing.
Option D is incorrect because the splunk edit oneshot command does not exist. There is no
such command in the Splunk CLI.
Question # 5
| Which valid bucket types are searchable? (select all that apply) |
| A. Hot buckets
| | B. Cold buckets
| | C. Warm buckets
| | D. Frozen buckets |
A. Hot buckets
B. Cold buckets
C. Warm buckets
Question # 6
| Which pathway represents where a network input in Splunk might be found? |
| A. $SPLUNK HOME/ etc/ apps/ ne two r k/ inputs.conf
| | B. $SPLUNK HOME/ etc/ apps/ $appName/ local / inputs.conf
| | C. $SPLUNK HOME/ system/ local /udp.conf
| | D. $SPLUNK HOME/ var/lib/ splunk/$inputName/homePath/ |
B. $SPLUNK HOME/ etc/ apps/ $appName/ local / inputs.conf
Explanation:
The correct answer is B. The network input in Splunk might be found in the
$SPLUNK_HOME/etc/apps/$appName/local/inputs.conf file.
A network input is a type of input that monitors data from TCP or UDP ports. To configure a
network input, you need to specify the port number, the connection host, the source, and
the sourcetype in the inputs.conf file.You can also set other optional settings, such as
index, queue, and host_regex1.
The inputs.conf file is a configuration file that contains the settings for different types of inputs, such as files, directories, scripts, network ports, and Windows event logs. The
inputs.conf file can be located in various directories, depending on the scope and priority of
the settings. The most common locations are:
$SPLUNK_HOME/etc/system/default: This directory contains the default settings
for all inputs.You should not modify or copy the files in this directory2.
$SPLUNK_HOME/etc/system/local: This directory contains the custom settings for
all inputs that apply to the entire Splunk instance.The settings in this directory
override the default settings2.
$SPLUNK_HOME/etc/apps/$appName/default: This directory contains the default
settings for all inputs that are specific to an app.You should not modify or copy the
files in this directory2.
$SPLUNK_HOME/etc/apps/$appName/local: This directory contains the custom
settings for all inputs that are specific to an app.The settings in this directory
override the default and system settings2.
Therefore, the best practice is to create or edit the inputs.conf file in the
$SPLUNK_HOME/etc/apps/$appName/local directory, where $appName is the name of
the app that you want to configure the network input for. This way, you can avoid modifying
the default files and ensure that your settings are applied to the specific app.
The other options are incorrect because:
A. There is no network directory under the apps directory. The network input
settings should be in the inputs.conf file, not in a separate directory.
C. There is no udp.conf file in Splunk. The network input settings should be in the
inputs.conf file, not in a separate file. The system directory is not the
recommended location for custom settings, as it affects the entire Splunk instance.
D. The var/lib/splunk directory is where Splunk stores the indexed data, not the
input settings. The homePath setting is used to specify the location of the index
data, not the input data. The inputName is not a valid variable for inputs.conf.
Question # 7
How would you configure your distsearch conf to allow you to run the search below?
sourcetype=access_combined status=200 action=purchase
splunk_setver_group=HOUSTON
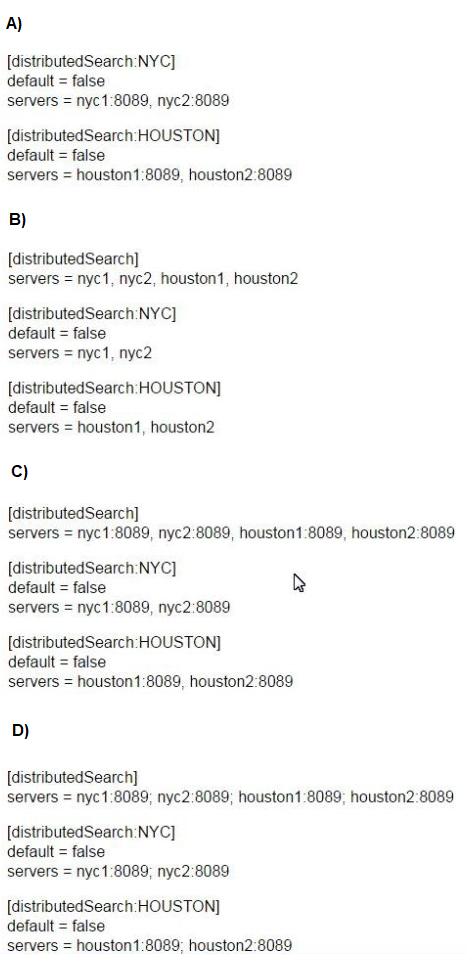 |
| A. Option A | | B. Option B | | C. Option C | | D. Option C |
C. Option C
Question # 8
| What is the correct curl to send multiple events through HTTP Event Collector? |
| A. Option A | | B. Option B | | C. Option C | | D. Option D |
B. Option B
Explanation: curl “https://mysplunkserver.example.com:8088/services/collector” \ -H
“Authorization: Splunk DF4S7ZE4-3GS1-8SFS-E777-0284GG91PF67” \ -d ‘{“event”: “Hello
World”}, {“event”: “Hola Mundo”}, {“event”: “Hallo Welt”}’. This is the correct curl command
to send multiple events through HTTP Event Collector (HEC), which is a token-based API
that allows you to send data to Splunk Enterprise from any application that can make an
HTTP request. The command has the following components:
The URL of the HEC endpoint, which consists of the protocol (https), the hostname
or IP address of the Splunk server (mysplunkserver.example.com), the port
number (8088), and the service name (services/collector).
The header that contains the authorization token, which is a unique identifier that
grants access to the HEC endpoint. The token is prefixed with Splunk and
enclosed in quotation marks. The token value (DF4S7ZE4-3GS1-8SFS-E777-
0284GG91PF67) is an example and should be replaced with your own token
value.
The data payload that contains the events to be sent, which are JSON objects
enclosed in curly braces and separated by commas. Each event object has a
mandatory field called event, which contains the raw data to be indexed. The event
value can be a string, a number, a boolean, an array, or another JSON object. In
this case, the event values are strings that say hello in different languages.
Get 189 Splunk Enterprise Certified Admin Exam questions Access in less then $0.12 per day.
Splunk Bundle 1:
1 Month PDF Access For All Splunk Exams with Updates
$200
$800
Buy Bundle 1
Splunk Bundle 2:
3 Months PDF Access For All Splunk Exams with Updates
$300
$1200
Buy Bundle 2
Splunk Bundle 3:
6 Months PDF Access For All Splunk Exams with Updates
$450
$1800
Buy Bundle 3
Splunk Bundle 4:
12 Months PDF Access For All Splunk Exams with Updates
$600
$2400
Buy Bundle 4
Disclaimer: Fair Usage Policy - Daily 5 Downloads
Splunk Enterprise Certified Admin Exam Test Dumps
Exam Code: SPLK-1003
Exam Name: Splunk Enterprise Certified Admin Exam
- 90 Days Free Updates
- Splunk Experts Verified Answers
- Printable PDF File Format
- SPLK-1003 Exam Passing Assurance
Get 100% Real SPLK-1003 Exam Dumps With Verified Answers As Seen in the Real Exam. Splunk Enterprise Certified Admin Exam Exam Questions are Updated Frequently and Reviewed by Industry TOP Experts for Passing Splunk Enterprise Certified Admin Exam Quickly and Hassle Free.
Splunk SPLK-1003 Test Dumps
Struggling with Splunk Enterprise Certified Admin Exam preparation? Get the edge you need! Our carefully created SPLK-1003 test dumps give you the confidence to pass the exam. We offer:
1. Up-to-date Splunk Enterprise Certified Admin practice questions: Stay current with the latest exam content.
2. PDF and test engine formats: Choose the study tools that work best for you.
3. Realistic Splunk SPLK-1003 practice exam: Simulate the real exam experience and boost your readiness.
Pass your Splunk Enterprise Certified Admin exam with ease. Try our study materials today!
Official Splunk Enterprise Certified Admin exam info is available on Splunk website at https://www.splunk.com/en_us/training/certification-track/splunk-enterprise-certified-admin.html
Prepare your Splunk Enterprise Certified Admin exam with confidence!We provide top-quality SPLK-1003 exam dumps materials that are:
1. Accurate and up-to-date: Reflect the latest Splunk exam changes and ensure you are studying the right content.
2. Comprehensive Cover all exam topics so you do not need to rely on multiple sources.
3. Convenient formats: Choose between PDF files and online Splunk Enterprise Certified Admin Exam practice questions for easy studying on any device.
Do not waste time on unreliable SPLK-1003 practice test. Choose our proven Splunk Enterprise Certified Admin study materials and pass with flying colors. Try Dumps4free Splunk Enterprise Certified Admin Exam 2024 material today!
Splunk Enterprise Certified Admin Exams
-
Assurance
Splunk Enterprise Certified Admin Exam practice exam has been updated to reflect the most recent questions from the Splunk SPLK-1003 Exam.
-
Demo
Try before you buy! Get a free demo of our Splunk Enterprise Certified Admin exam dumps and see the quality for yourself. Need help? Chat with our support team.
-
Validity
Our Splunk SPLK-1003 PDF contains expert-verified questions and answers, ensuring you're studying the most accurate and relevant material.
-
Success
Achieve SPLK-1003 success! Our Splunk Enterprise Certified Admin Exam exam questions give you the preparation edge.
If you have any question then contact our customer support at live chat or email us at support@dumps4free.com.
|

