
- Email support@dumps4free.com

An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group. What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
A. A service route to the LDAP server
B. A Master Device
C. Authentication Portal
D. A User-ID agent on the LDAP server
A decryption policy has been created with an action of "No Decryption." The decryption profile is configured in alignment to best practices. What protections does this policy provide to the enterprise?
A. It allows for complete visibility into certificate data, ensuring secure connections to all websites.
B. It ensures that the firewall checks its certificate store, enabling sessions with trusted self-signed certificates even when an alternative trust anchor exists.
C. It encrypts all certificate information to maintain privacy and compliance with local regulations.
D. It enhances security by actively blocking access to potentially insecure sites with expired certificates or untrusted issuers.
Review the screenshots.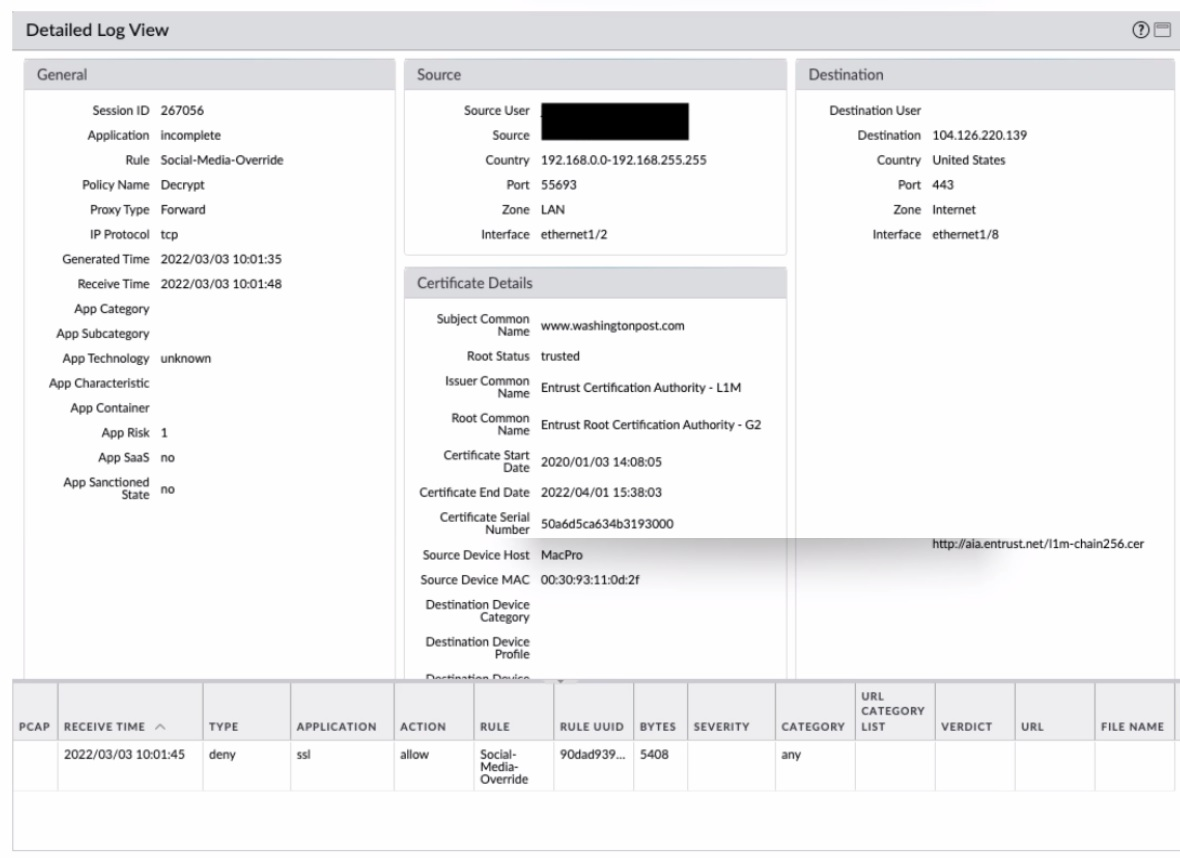
What is the most likely reason for this decryption error log?
A. The Certificate fingerprint could not be found.
B. The client expected a certificate from a different CA than the one provided.
C. The client received a CA certificate that has expired or is not valid.
D. Entrust is not a trusted root certificate authority (CA).
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama?
A. A User-ID Certificate profile must be configured on Panorama.
B. The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
C. User-ID Redistribution must be configured on Panorama to ensure that all firewalls have the same mappings.
D. A master device with Group Mapping configured must be set in the device group where the Security rules are configured.
Explanation: When building Security rules in a Device Group that need to allow traffic to
specific users and groups defined in Active Directory, it's essential to have user and group
information available in Panorama to select these entities for the rules.
D. A master device with Group Mapping configured must be set in the device group
where the Security rules are configured:
The concept of a "master device" in Panorama refers to a specific firewall that is
designated to provide certain settings or information, such as user and group
mappings from Active Directory, to Panorama. This information can then be used
across other firewalls within the same device group.
By configuring Group Mapping on a master device, Panorama can leverage this
information to populate user and group objects. These objects can then be used in
Security rules within the device group, allowing for the creation of policies that are
based on user identity and group membership, as defined in Active Directory.
This setup ensures that Panorama has the necessary context to apply user- and
group-based policies accurately across the managed firewalls, facilitating
centralized management and consistency in policy enforcement.
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment. Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A. Kerberos or SAML authentication need to be configured
B. LDAP or TACACS+ authentication need to be configured
C. RADIUS is only supported for a transparent Web Proxy.
D. RADIUS is not supported for explicit or transparent Web Proxy
Explanation: For explicit Web Proxy deployment on PAN-OS, Palo Alto Networks currently supports Kerberos and SAML as authentication methods. RADIUS is not supported for explicit or transparent Web Proxy authentication on Palo Alto Networks appliances, which means that if the client is currently using RADIUS, they will need to configure an alternate supported authentication method. LDAP or TACACS+ authentication is not directly supported for Web Proxy authentication in PAN-OS.For more information on supported Web Proxy authentication methods, please refer to the latest Palo Alto Networks "PANOS ® Web Interface Reference Guide".
| Page 7 out of 65 Pages |
| Previous |