
- Email support@dumps4free.com

The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
A. Management plane CPU
B. Dataplane CPU
C. Packet buffers
D. On-chip packet descriptors
A company has configured GlobalProtect to allow their users to work from home. A decrease in performance for remote workers has been reported during peak-use hours. Which two steps are likely to mitigate the issue? (Choose TWO)
A. Exclude video traffic
B. Enable decryption
C. Block traffic that is not work-related
D. Create a Tunnel Inspection policy
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A. DNS Proxy
B. SSL/TLS profiles
C. address groups
D. URL Filtering profiles
An engineer is configuring a Protection profile to defend specific endpoints and resources
against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for
specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
A. Packet Buffer Protection
B. Zone Protection
C. Vulnerability Protection
D. DoS Protection
Explanation: The engineer is configuring a DoS Protection profile to defend specific endpoints and resources against malicious activity. A DoS Protection profile is a feature that enables the firewall to detect and prevent denial-of-service (DoS) attacks that attempt to overwhelm network resources or disrupt services. A DoS Protection profile can provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet, such as web servers, DNS servers, or VPN gateways. A DoS Protection profile can be applied to a security policy rule that matches the traffic to and from the protected systems, and can specify the thresholds and actions for different types of flood attacks, such as SYN, UDP, ICMP, or other IP floods12. References: DoS Protection, PCNSE Study Guide (page 58)
Review the information below. A firewall engineer creates a U-NAT rule to allow users in
the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as
expected?
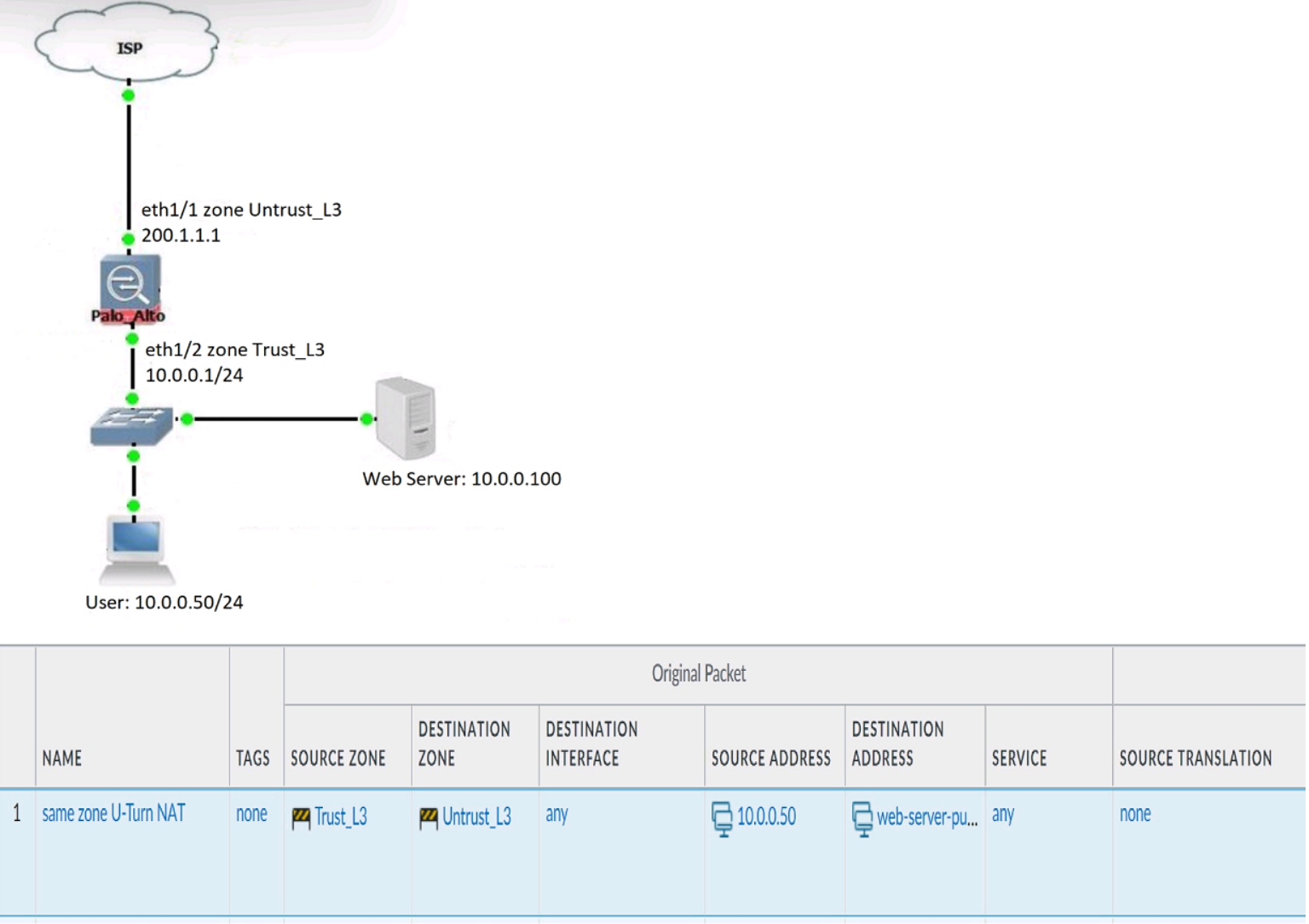
A. Change destination NAT zone to Trust_L3.
B. Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
C. Change Source NAT zone to Untrust_L3.
D. Add source Translation to translate original source IP to the firewall eth1/2 interface translation.
| Page 17 out of 59 Pages |
| Previous |