
- Email support@dumps4free.com

A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3. Which command should they use?
A. test routing route ip 10.2.5.3 *
B. test routing route ip 10.2.5.3 virtual-router default
C. test routing fib-lookup ip 10.2.5.0/24 virtual-router default
D. test routing fib-lookup ip 10.2.5.3 virtual-router default
Explanation: To determine the egress interface a Palo Alto Networks firewall will use to route a specific IP address, the appropriate command is test routing fib-lookup ip 10.2.5.3 virtual-router default. This command performs a Forwarding Information Base (FIB) lookup for the specified IP address within the context of the specified virtual router, which in this case is the default virtual router. The FIB lookup process checks the routing table and the associated forwarding information to determine the next-hop and the egress interface for the given IP address. This command is instrumental for troubleshooting and verifying routing decisions made by the firewall to ensure that traffic is routed as expected through the network infrastructure.
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
A. Configure the decryption profile
B. Define a Forward Trust Certificate
C. Configure SSL decryption rules
D. Configure a SSL/TLS service profile
Explanation: To configure SSL Forward Proxy decryption on a Palo Alto Networks firewall,
certain key components must be set up to ensure secure and effective decryption and
inspection of SSL/TLS encrypted traffic:
B. Define a Forward Trust Certificate:
A Forward Trust Certificate is essential for SSL Forward Proxy decryption. This
certificate is used by the firewall to dynamically generate certificates for SSL sites
that are trusted. When the firewall decrypts and inspects the traffic and then re-encrypts
it, the new certificate presented to the client comes from the Forward
Trust Certificate authority. This certificate must be trusted by client devices, often
requiring the Forward Trust CA certificate to be distributed and installed on client
devices.
C. Configure SSL decryption rules:
SSL decryption rules are the policies that determine which traffic is to be
decrypted. These rules specify the source, destination, service, and URL category,
among other criteria. The rules define what traffic the SSL Forward Proxy will
apply to, enabling selective decryption based on security and privacy
requirements.
Together, these components form the basis of the SSL Forward Proxy decryption setup,
allowing for the decryption, inspection, and re-encryption of SSL/TLS encrypted traffic to
identify and prevent threats hidden within encrypted sessions.
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
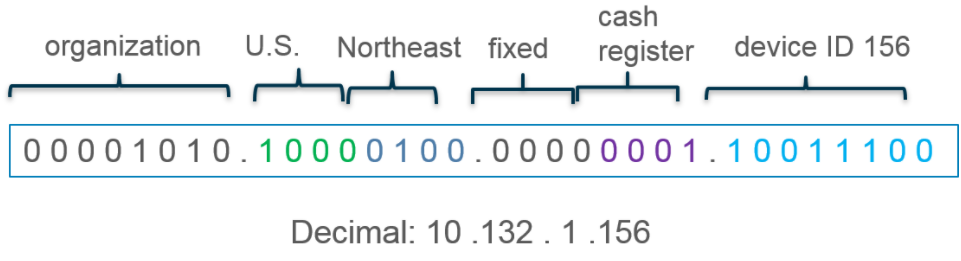
A. IP Netmask
B. IP Wildcard Mask
C. IP Address
D. IP Range
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
A. certificates
B. profiles
C. link state
D. stateful firewall connection
Which log type would provide information about traffic blocked by a Zone Protection profile?
A. Data Filtering
B. IP-Tag
C. Traffic
D. Threat
Explanation: D is the correct answer because the threat log type would provide information about traffic blocked by a Zone Protection profile. This is because Zone Protection profiles are used to protect the network from attacks, including common flood, reconnaissance attacks, and other packet-based attacks1. These attacks are classified as threats by the firewall and are logged in the threat log2. The threat log displays information such as the source and destination IP addresses, ports, zones, applications, threat types, actions, and severity of the threats2.
| Page 13 out of 59 Pages |
| Previous |