
- Email support@dumps4free.com

Refer to the exhibit, which shows a custom signature.
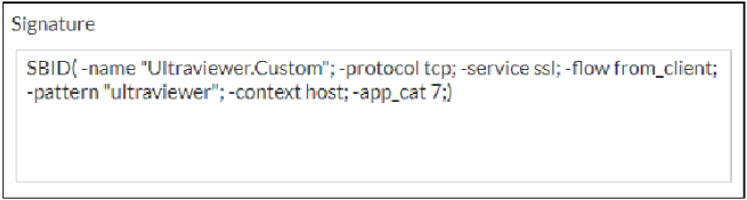
Which two modifications must you apply to the configuration of this custom signature so that you can save it on FortiGate? (Choose two.)
A. Ensure that the header syntax is F-SBID.
B. Add severity.
C. Add attack_id.
D. Start options with --.
You contoured an address object on the tool fortiGate in a Security Fabric. This object is not synchronized with a downstream device. Which two reasons could be the cause? (Choose two)
A. The address object on the tool FortiGate has fabric-object set to disable
B. The root FortiGate has configuration-sync set to enable
C. The downstream TortiGate has fabric-object-unification set to local
D. The downstream FortiGate has configuration-sync set to local
Explanation:
Option A is correct because the address object on the tool FortiGate will not be synchronized with the downstream devices if it has fabric-object set to disable. This option controls whether the address object is shared with other FortiGate devices in the Security Fabric or not1.
Option C is correct because the downstream FortiGate will not receive the address object from the tool FortiGate if it has fabric-object-unification set to local. This option controls whether the downstream FortiGate uses the address objects from the root FortiGate or its own local address objects2.
Option B is incorrect because the root FortiGate has configuration-sync set to enable by default, which means that it will synchronize the address objects with the downstream devices unless they are disabled by the fabric-object option3.
Option D is incorrect because the downstream FortiGate has configuration-sync set to local by default, which means that it will receive the address objects from the root FortiGate unless they are overridden by the fabric-object-unification option4.
References: =
1: Group address objects synchronized from FortiManager5
2: Security Fabric address object unification6
3: Configuration synchronization7
4: Configuration synchronization7
: Security Fabric - Fortinet Documentation
What are two functions of automation stitches? (Choose two.)
A. Automation stitches can be created to run diagnostic commands and email the results when CPU or memory usage exceeds specified thresholds.
B. An automation stitch configured to execute actions in parallel can be set to insert a specific delay between actions.
C. Automation stitches can be configured on any FortiGate device in a Security Fabric environment.
D. An automation stitch configured to execute actions sequentially can take parameters from previous actions as input for the current action.
Which ADVPN configuration must be configured using a script on fortiManager, when using VPN Manager to manage fortiGate VPN tunnels?
A. Enable AD-VPN in IPsec phase 1
B. Disable add-route on hub
C. Configure IP addresses on IPsec virtual interlaces
D. Set protected network to all
Explanation:
To enable AD-VPN, you need to edit an SD-WAN overlay template and enable the Auto-Discovery VPN toggle. This will automatically add the required settings to the IPsec template and the BGP template. You cannot enable AD-VPN directly in the IPsec phase 1 settings using VPN Manager.
References := ADVPN | FortiManager 7.2.0 - Fortinet Documentation
Which two statements about IKE vision 2 are true? (Choose two.)
A. Phase 1 includes main mode
B. It supports the extensible authentication protocol (EAP)
C. It supports the XAuth protocol.
D. It exchanges a minimum of four messages to establish a secure tunnel
Explanation:
IKE version 2 supports the extensible authentication protocol (EAP), which allows for more flexible and secure authentication methods1. IKE version 2 also exchanges a minimum of four messages to establish a secure tunnel, which is more efficient than IKE version 12. References: = IKE settings | FortiClient 7.2.2 - Fortinet Documentation, Technical Tip: How to configure IKE version 1 or 2 … - Fortinet Community
| Page 2 out of 13 Pages |
| Previous |