
- Email support@dumps4free.com

Which FortiAnalyzer feature allows you to use a proactive approach when managing your network security?
A. FortiView Monitor
B. Outbreak alert services
C. Incidents dashboard
D. Threat hunting
Explanation: FortiAnalyzer offers several features for monitoring, alerting, and incident
management, each serving different purposes. Let's examine each option to determine
which one best supports a proactive security approach.
Option A - FortiView Monitor:
Option B - Outbreak Alert Services:
Option C - Incidents Dashboard:
Option D - Threat Hunting:
Conclusion:
Correct Answer: D. Threat hunting
Threat hunting is the most proactive feature among the options, as it involves
actively searching for threats within the network rather than reacting to already
detected incidents.
References:
FortiAnalyzer 7.4.1 documentation on Threat Hunting and proactive security
measures.
Exhibit.
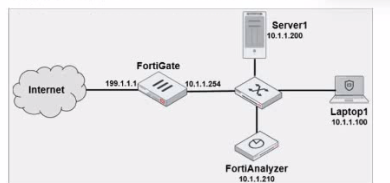
Laptop1 is used by several administrators to manage FotiAnalyzer. You want to configure a
generic text filter that matches all login attempts to the web interface generated by any user
other than admin’’, and coming from Laptop1.
Which filter will achieve the desired result?
A. Operation-login and performed_on==’’GUI(10.1.1.100)’ and user!=admin
B. Operation-login and performed_on==’’GU (10.1.1.120)’ and user!=admin
C. Operation-login and srcip== 10.1.1.100 and dstip==10.1.1.1.210 and user==admin
D. Operation-login and dstip==10.1.1.210 and user!-admin
Explanation: The objective is to create a filter that identifies all login attempts to the
FortiAnalyzer web interface (GUI) coming from Laptop1 (IP 10.1.1.100) and excludes the
admin user. This filter should match any user other than admin.
Filter Components Analysis:
Option Analysis:
Conclusion:
Correct Answer: A. Operation-login and performed_on==’’GUI(10.1.1.100)’ and
user!=admin
This filter precisely captures the required conditions: login attempts from Laptop1
to the GUI interface by any user except admin.
References:
FortiAnalyzer 7.4.1 documentation on log filters, syntax for login operations, and
GUI login tracking.
Which statement describes archive logs on FortiAnalyzer?
A. Logs that are indexed and stored in the SQL database
B. Logs a FortiAnalyzer administrator can access in FortiView
C. Logs compressed and saved in files with the .gz extension
D. Logs previously collected from devices that are offline
Explanation: In FortiAnalyzer, archive logs refer to logs that have been compressed and
stored to save space. This process involves compressing the raw log files into the .gz
format, which is a common compression format used in Fortinet systems for archived data.
Archiving is essential in FortiAnalyzer to optimize storage and manage long-term retention
of logs without impacting performance.
Let’s examine each option for clarity:
Option A: Logs that are indexed and stored in the SQL database
Option B: Logs a FortiAnalyzer administrator can access in FortiView
Option C: Logs compressed and saved in files with the .gz extension
Option D: Logs previously collected from devices that are offline
References: FortiAnalyzer 7.4.1 documentation and configuration guides outline that
archived logs are stored in compressed files with the .gz extension to conserve storage
space, ensuring FortiAnalyzer can handle a larger volume of logs over extended periods.
Exhibit.
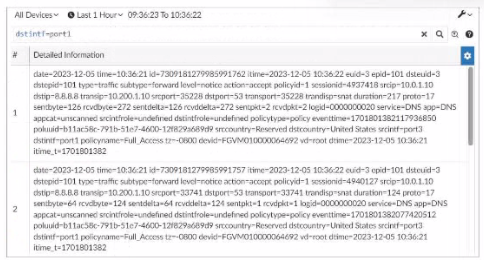
What can you conclude about these search results? (Choose two.)
A. They can be downloaded to a file.
B. They are sortable by columns and customizable.
C. They are not available for analysis in FortiView.
D. They were searched by using text mode.
Explanation: In this exhibit, we observe a search query on the FortiAnalyzer interface
displaying log data with details about the connection events, including fields like date, srcip,
dstip, service, and dstintf. This setup allows for several functionalities within FortiAnalyzer.
Option A - Download Capability:
Option B - Sorting and Customization:
Option C - Availability in FortiView:
Option D - Text Mode Search:
Conclusion:
Correct Answer: A. They can be downloaded to a file. and B. They are sortable by
columns and customizable.
These options are consistent with FortiAnalyzer's capabilities for managing,
exporting, and customizing log data.
References:
FortiAnalyzer 7.4.1 documentation on search, export functionalities, and
customizable views.
Which statement about sending notifications with incident update is true?
A. You can send notifications to multiple external platforms.
B. Notifications can be sent only by email.
C. If you use multiple fabric connectors, all connectors must have the same settings.
D. Notifications can be sent only when an incident is updated or deleted.
Explanation: In FortiOS and FortiAnalyzer, incident notifications can be sent to multiple
external platforms, not limited to a single method such as email. Fortinet's security fabric
and integration capabilities allow notifications to be sent through various fabric connectors
and third-party integrations. This flexibility is designed to ensure that incident updates
reach relevant personnel or systems using preferred communication channels, such as
email, Syslog, SNMP, or integration with SIEM platforms.
Let’s review each answer option for clarity:
Option A: You can send notifications to multiple external platforms
Option B: Notifications can be sent only by email
Option C: If you use multiple fabric connectors, all connectors must have the same
settings
Option D: Notifications can be sent only when an incident is updated or deleted
References: According to FortiOS and FortiAnalyzer 7.4.1 documentation, notifications for
incidents can be configured across various platforms by using multiple connectors, and
they are not limited to email alone. This capability is part of the Fortinet Security Fabric,
allowing for a broad range of integrations with external systems and platforms for effective
incident response.
| Page 2 out of 12 Pages |
| Previous |