
- Email support@dumps4free.com

A company provides guest WiFi access to the internet and physically separates the guest
network from the company’s internal WIFI. Due to a recent incident in which an attacker
gained access to the compay’s intend WIFI, the company plans to configure WPA2
Enterprise in an EAP- TLS configuration. Which of the following must be installed on
authorized hosts for this new configuration to work properly?
A.
Active Directory OPOs
B.
PKI certificates
C.
Host-based firewall
D.
NAC persistent agent
PKI certificates
Due to locality and budget constraints, an organization’s satellite office has a lower
bandwidth allocation than other offices in the organization. As a result, the local security
infrastructure staff is assessing architectural options that will help preserve network
bandwidth and increase speed to both internal and external resources while not sacrificing
threat visibility.
Which of the following would be the BEST option to implement?
A.
Distributed connection allocation
B.
Local caching
C.
Content delivery network
D.
SD-WAN vertical heterogeneity
Content delivery network
Which of the following technologies allows CSPs to add encryption across multiple data storages?
A.
Symmetric encryption
B.
Homomorphic encryption
C.
Data dispersion
D.
Bit splitting
Symmetric encryption
Reference: https://www.hhs.gov/sites/default/files/nist800111.pdf
A company undergoing digital transformation is reviewing the resiliency of a CSP and is
concerned about meeting SLA requirements in the event of a CSP incident.
Which of the following would be BEST to proceed with the transformation?
A.
An on-premises solution as a backup
B.
A load balancer with a round-robin configuration
C.
A multicloud provider solution
D.
An active-active solution within the same tenant
An active-active solution within the same tenant
A security architect is reviewing the following proposed corporate firewall architecture and configuration: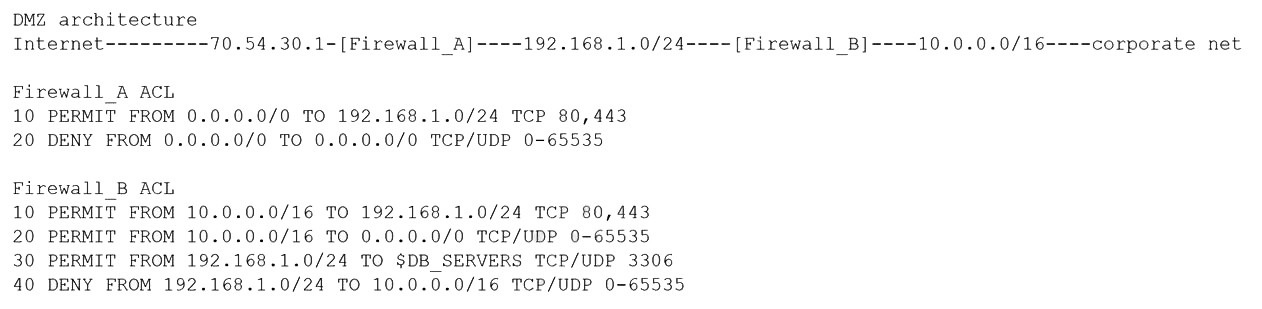
Both firewalls are stateful and provide Layer 7 filtering and routing. The company has the
following requirements:
Web servers must receive all updates via HTTP/S from the corporate network.
Web servers should not initiate communication with the Internet.
Web servers should only connect to preapproved corporate database servers.
Employees’ computing devices should only connect to web services over ports 80 and 443.
Which of the following should the architect recommend to ensure all requirements are met
in the MOST secure manner? (Choose two.)
A.
Add the following to Firewall_A: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0/0 TCP
80,443
B.
Add the following to Firewall_A: 15 PERMIT FROM 192.168.1.0/24 TO 0.0.0.0 TCP
80,443
C.
Add the following to Firewall_A: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0/0 TCP/UDP
0-65535
D.
Add the following to Firewall_B: 15 PERMIT FROM 0.0.0.0/0 TO 10.0.0.0/16 TCP/UDP
0-65535
E.
Add the following to Firewall_B: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0 TCP/UDP 0-
65535
F.
Add the following to Firewall_B: 15 PERMIT FROM 192.168.1.0/24 TO 10.0.2.10/32
TCP 80,443
Add the following to Firewall_A: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0/0 TCP
80,443
Add the following to Firewall_B: 15 PERMIT FROM 0.0.0.0/0 TO 10.0.0.0/16 TCP/UDP
0-65535
| Page 2 out of 40 Pages |
| Previous |