
- Email support@dumps4free.com

A Linux administrator needs to redirect all HTTP traffic temporarily to the new proxy server 192.0.2.25 on port 3128. Which of the following commands will accomplish this task?
A.
iptables -t nat -D PREROUTING -p tcp --sport 80 -j DNAT - -to-destination 192.0.2.25:3128
B.
iptables -t nat -A PREROUTING -p top --dport 81 -j DNAT –-to-destination
192.0.2.25:3129
C.
iptables -t nat -I PREROUTING -p top --sport 80 -j DNAT –-to-destination
192.0.2.25:3129
D.
iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT –-to-destination
192.0.2.25:3128
iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT –-to-destination
192.0.2.25:3128
A DevOps engineer needs to allow incoming traffic to ports in the range of 4000 to 5000 on a Linux server. Which of the following commands will enforce this rule?
A.
iptables -f filter -I INPUT -p tcp --dport 4000:5000 -A ACCEPT
B.
iptables -t filter -A INPUT -p tcp --dport 4000:5000 -j ACCEPT
C.
iptables filter -A INPUT -p tcp --dport 4000:5000 -D ACCEPT
D.
iptables filter -S INPUT -p tcp --dport 4000:5000 -A ACCEPT
iptables -t filter -A INPUT -p tcp --dport 4000:5000 -j ACCEPT
When trying to log in remotely to a server, a user receives the following message:
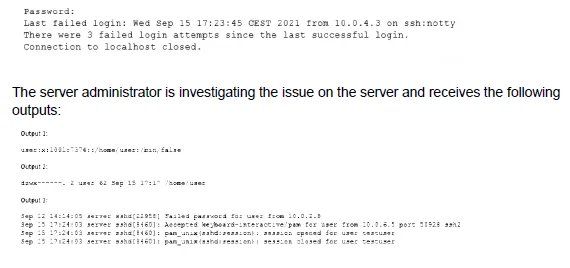
Which of the following is causing the issue?
A.
The wrong permissions are on the user’s home directory.
B.
The account was locked out due to three failed logins.
C.
The user entered the wrong password.
D.
The user has the wrong shell assigned to the account.
The user has the wrong shell assigned to the account.
Which of the following enables administrators to configure and enforce MFA on a Linux system?
A.
Kerberos
B.
SELinux
C.
PAM
D.
PKI
Kerberos
Which of the following technologies provides load balancing, encryption, and observability in containerized environments?
A.
Virtual private network
B.
Sidecar pod
C.
Overlay network
D.
Service mesh
Service mesh
Explanation: "A service mesh controls the delivery of service requests in an application. Common features provided by a service mesh include service discovery, load balancing, encryption and failure recovery."
https://www.techtarget.com/searchitoperations/definition/service-mesh
| Page 8 out of 73 Pages |
| Previous |