
- Email support@dumps4free.com

Topic 3: Exam Pool C
An organization has hired a security analyst to perform a penetration test. The analyst
captures 1Gb worth of inbound network traffic to the server and transfer the pcap back to
the machine for analysis. Which of the following tools should the analyst use to further
review the pcap?
A.
Nmap
B.
BcURL
C.
Netcat
D.
Wireshark
Wireshark
An attacker was easily able to log in to a company's security camera by performing a basic
online search for a setup guide for that particular camera brand and model Which of the
following BEST describes the configurations the attacker exploited?
A.
Weak encryption
B.
Unsecure protocols
C.
Default settings
D.
Open permissions
Default settings
A Chief Security Officer (CSO) is concerned about the amount of PII that is stored locally on each salesperson’s laptop. The sales department has a higher-than-average rate of lost equipment. Which of the following recommendations would BEST address the CSO’s concern?
A.
Deploy an MDM solution.
B.
Implement managed FDE.
C.
Replace all hard drives with SEDs.
D.
Install DLP agents on each laptop
Implement managed FDE.
A user contacts the help desk to report the following:
Two days ago, a pop-up browser window prompted the user for a name and
password after connecting to the corporate wireless SSID. This had never
happened before, but the user entered the information as requested.
The user was able to access the Internet but had trouble accessing the
department share until the next day. The user is now getting notifications from the bank about unauthorized transactions. Which of the following attack vectors was MOST likely used in this scenario?
A.
Rogue access point
B.
Evil twin
C.
DNS poisoning
D.
ARP poisoning
Rogue access point
A security analyst is investigation an incident that was first reported as an issue connecting
to network shares and the internet, While reviewing logs and tool output, the analyst sees
the following: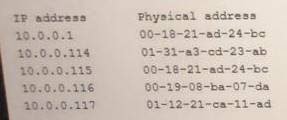
Which of the following attacks has occurred?
A.
IP conflict
B.
Pass-the-hash
C.
MAC flooding
D.
Directory traversal
E.
ARP poisoning
ARP poisoning
| Page 5 out of 178 Pages |
| Previous |