
- Email support@dumps4free.com

Topic 3: Exam Pool C
An information security incident recently occurred at an organization, and the organization
was required to report the incident to authorities and notify the affected parties. When the
organization's customers became of aware of the incident, some reduced their orders or
stopped placing orders entirely. Which of the following is the organization experiencing?
A.
Reputation damage
B.
Identity theft
C.
Anonymlzation
D.
Interrupted supply chain
Reputation damage
A network administrator has been asked to install an IDS to improve the security posture of an organization. Which of the following control types is an IDS?
A.
Corrective
B.
Physical
C.
Detective
D.
Administrative
Detective
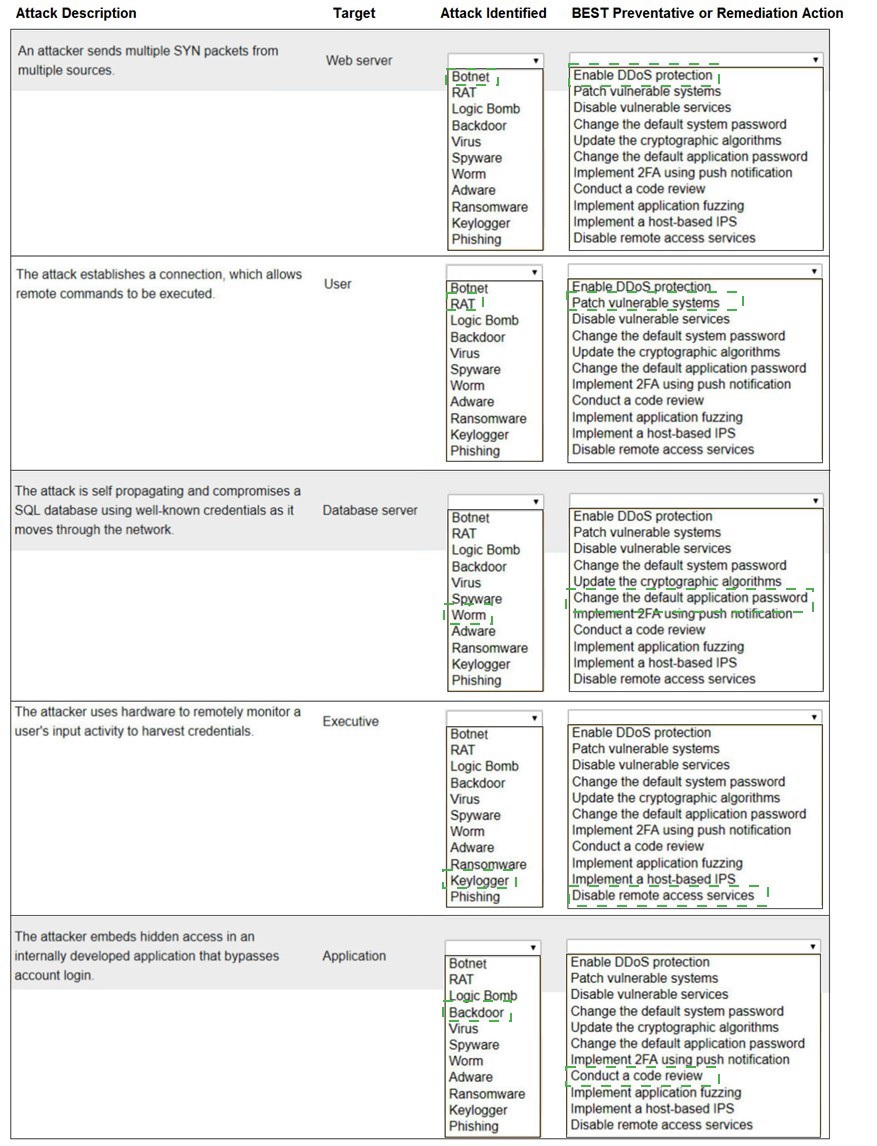
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.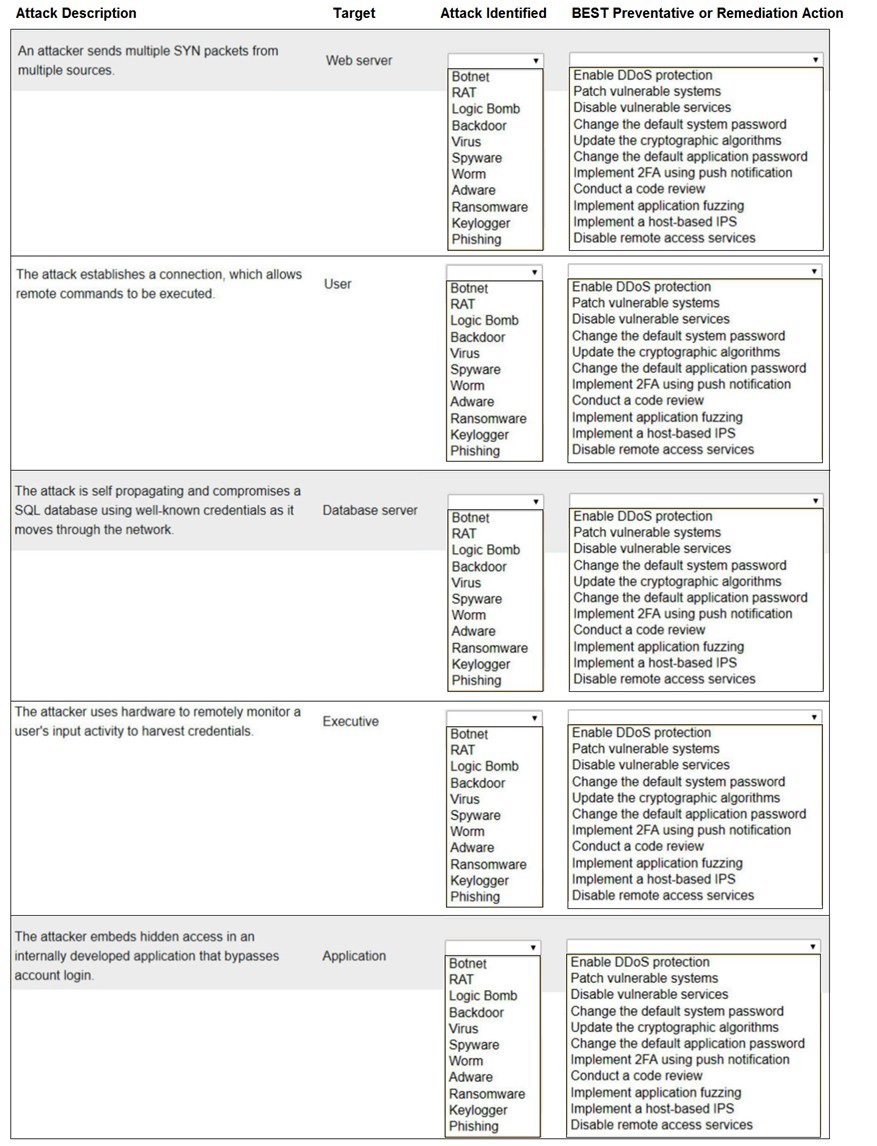
Which of the following control sets should a well-written BCP include? (Select THREE)
A.
Preventive
B.
Detective
C.
Deterrent
D.
Corrective
Preventive
Corrective
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
A.
PCI DSS
B.
ISO 22301
C.
ISO 27001
D.
NIST CSF
PCI DSS
Explanation: Additionally, many organizations should abide by certain standards. For
example, organizations handling credit card information need to comply with the Payment
Card Industry Data Security Standard (PCI DSS). PCI DSS includes six control objectives
and 12 specific requirementsthat help prevent fraud.
| Page 24 out of 178 Pages |
| Previous |