
- Email support@dumps4free.com

Topic 1: Exam Pool A
A security analyst is reviewing the following attack log output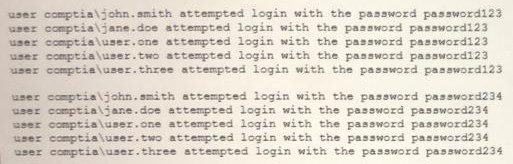
Which of the following types of attacks does this MOST likely represent?
A.
Rainbow table
B.
Brute-force
C.
Password-spraying
D.
Dictionary
Password-spraying
A security analyst discovers that a company username and password database was posted on an internet forum. The username and passwords are stored in plan text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
A.
Create DLP controls that prevent documents from leaving the network
B.
Imment salting and hashing
C.
Configure the web content filter to block access to the forum.
D.
Increase password complexity requirements
Create DLP controls that prevent documents from leaving the network
A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organization’s vulnerabilities. Which of the following would BEST meet this need?
A.
CVE
B.
SIEM
C.
SOAR
D.
CVSS
CVSS
A critical file server is being upgraded and the systems administrator must determine which
RAID level the new server will need to achieve parity and handle two simultaneous disk
failures. Which of the following RAID levels meets this requirements?
A.
RAID 0+1
B.
RAID 2
C.
RAID 5
D.
RAID 6
RAID 5
Under GDPR, which of the following is MOST responsible for the protection of privacy and
website user rights?
A.
The data protection officer
B.
The data processor
C.
The data owner
D.
The data controller
The data owner
| Page 22 out of 178 Pages |
| Previous |