
- Email support@dumps4free.com

Topic 3: Exam Pool C
A security analyst is reviewing logs on a server and observes the following output: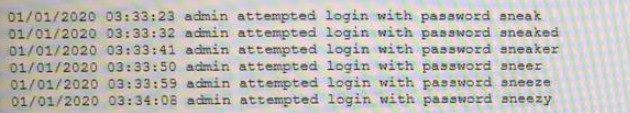
Which of the following is the security analyst observing?
A.
A rainbow table attack
B.
A password-spraying attack
C.
A dictionary attack
D.
A keylogger attack
A dictionary attack
A company’s bank has reported that multiple corporate credit cards have been stolen over the past several weeks. The bank has provided the names of the affected cardholders to the company’s forensics team to assist in the cyber-incident investigation. An incident responder learns the following information:
The timeline of stolen card numbers corresponds closely with affected users
making Internet-based purchases from diverse websites via enterprise desktop
PCs.
All purchase connections were encrypted, and the company uses an SSL
inspection proxy for the inspection of encrypted traffic of the hardwired network.
Purchases made with corporate cards over the corporate guest WiFi network,
where no SSL inspection occurs, were unaffected.
Which of the following is the MOST likely root cause?
A.
HTTPS sessions are being downgraded to insecure cipher suites
B.
The SSL inspection proxy is feeding events to a compromised SIEM
C.
The payment providers are insecurely processing credit card charges
D.
The adversary has not yet established a presence on the guest WiFi network
The payment providers are insecurely processing credit card charges
The facilities supervisor for a government agency is concerned about unauthorized access to environmental systems in the event the staff WiFi network is breached. Which of the blowing would BEST address this security concern?
A.
install a smart meter on the staff WiFi.
B.
Place the environmental systems in the same DHCP scope as the staff WiFi.
C.
Implement Zigbee on the staff WiFi access points.
D.
Segment the staff WiFi network from the environmental systems network.
Place the environmental systems in the same DHCP scope as the staff WiFi.
A user reports constant lag and performance issues with the wireless network whenworking at a local coffee shop. A security analyst walks the user through an installation ofWireshark and get a five-minute pcap to analyze. The analyst observes the following output: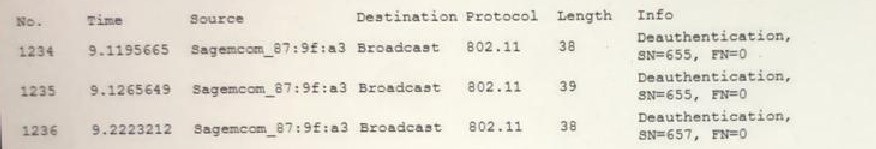
Which of the following attacks does the analyst MOST likely see in this packet capture?
A.
Session replay
B.
Evil twin
C.
Bluejacking
D.
ARP poisoning
Evil twin
A university with remote campuses, which all use different service providers, loses Internet connectivity across all locations. After a few minutes, Internet and VoIP services are restored, only to go offline again at random intervals, typically within four minutes of services being restored. Outages continue throughout the day, impacting all inbound and outbound connections and services. Services that are limited to the local LAN or WiFi network are not impacted, but all WAN and VoIP services are affected. Later that day, the edge-router manufacturer releases a CVE outlining the ability of an attacker to exploit the SIP protocol handling on devices, leading to resource exhaustion and system reloads. Which of the following BEST describe this type of attack? (Choose
A.
DoS
B.
SSL stripping
C.
Memory leak
D.
Race condition
E.
Shimming
F.
Refactoring
DoS
Race condition
| Page 21 out of 178 Pages |
| Previous |