
- Email support@dumps4free.com

Topic 3: Exam Pool C
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly. Which of the following technologies should the IT manager use when implementing MFA?
A.
One-time passwords
B.
Email tokens
C.
CPush notifications
D.
Hardware authentication
CPush notifications
An attacker has successfully exfiltrated several non-salted password hashes from an online
system. Given the logs below:
Which of the following BEST describes the type of password attack the attacker is performing?
A.
Dictionary
B.
Pass-the-hash
C.
Brute-force
D.
Password spraying
Dictionary
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: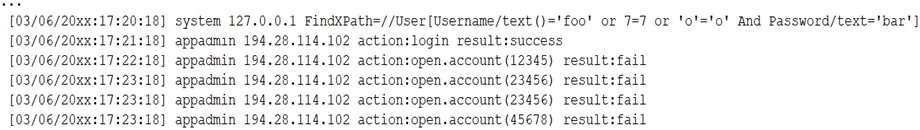
Which of the following can the security analyst conclude?
A.
A replay attack is being conducted against the application.
B.
An injection attack is being conducted against a user authentication system.
C.
A service account password may have been changed, resulting in continuous failed logins within the application.
D.
A credentialed vulnerability scanner attack is testing several CVEs against the
application
A service account password may have been changed, resulting in continuous failed logins within the application.
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
A.
Nmap
B.
Wireshark
C.
Autopsy
D.
DNSEnum
DNSEnum
Which of the following describes the ability of code to target a hypervisor from inside
A.
Fog computing
B.
VM escape
C.
Software-defined networking
D.
Image forgery
E.
Container breakout
VM escape
| Page 2 out of 178 Pages |
| Previous |