
- Email support@dumps4free.com

Topic 3: Exam Pool C
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?
A.
Watering-hole attack
B.
Credential harvesting
C.
Hybrid warfare
D.
Pharming
Watering-hole attack
A security modern may have occurred on the desktop PC of an organization's Chief
Executive Officer (CEO) A duplicate copy of the CEO's hard drive must be stored securely
to ensure appropriate forensic processes and the chain of custody are followed. Which of
the following should be performed to accomplish this task?
A.
Install a new hard drive in the CEO's PC, and then remove the old hard drive and place it in a tamper-evident bag
B.
Connect a write blocker to the hard drive Then leveraging a forensic workstation, utilize
the dd command m a live Linux environment to create a duplicate copy
C.
Rmove the CEO's hard drive from the PC, connect to the forensic workstation, and
copy all the contents onto a remote fileshare while the CEO watches
D.
Refrain from completing a forensic analysts of the CEO's hard drive until after the
incident is confirmed, duplicating the hard drive at this stage could destroy evidence
Connect a write blocker to the hard drive Then leveraging a forensic workstation, utilize
the dd command m a live Linux environment to create a duplicate copy
Explanation: “To obtain a forensically sound image from nonvolatile storage, you need to
ensure that nothing you do alters data or metadata (properties) on the source disk or file
system. A write blocker assures this process by preventing any data on the disk or volume
from being changed by filtering write commands at the driver and OS level. Data
acquisition would normally proceed by attaching the target device to a forensics
workstation or field capture device equipped with a write blocker.”
For purposes of knowing, https://security.opentext.com/tableau/hardware/details/t8u write
blockers like this are the most popular hardware blockers
A researcher has been analyzing large data sets for the last ten months. The researcherworks with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message: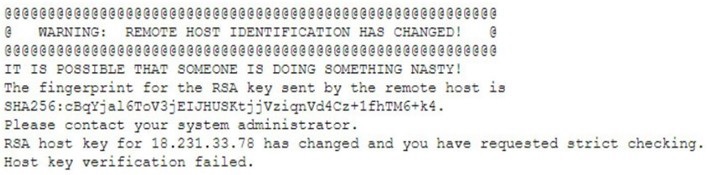
Which of the following network attacks is the researcher MOST likely experiencing?
A.
MAC cloning
B.
Evil twin
C.
Man-in-the-middle
D.
ARP poisoning
Man-in-the-middle
A user recent an SMS on a mobile phone that asked for bank delays. Which of the
following social-engineering techniques was used in this case?
A.
SPIM
B.
Vishing
C.
Spear phishing
D.
Smishing
Smishing
A network engineer notices the VPN concentrator overloaded and crashes on days when there are a lot of remote workers. Senior management has placed greater importance on the availability of VPN resources for the remote workers than the security of the end users’ traffic. Which of the following would be BEST to solve this issue?
A.
iPSec
B.
Always On
C.
Split tunneling
D.
L2TP
Always On
| Page 18 out of 178 Pages |
| Previous |