
- Email support@dumps4free.com

A company needs to retain tog data archives for several years to be compliant with regulations. The tog data is no longer used but It must be retained. What Is the MOST secure and cost-effective solution to meet these requirements?
A.
Archive the data to Amazon S3 and apply a restrictive bucket policy to deny the s3 DeleteOotect API
B.
Archive the data to Amazon S3 Glacier and apply a Vault Lock policy
C.
Archive the data to Amazon S3 and replicate it to a second bucket in a second IAM Region Choose the S3 Standard-Infrequent Access (S3 Standard-1A) storage class and apply a restrictive bucket policy to deny the s3 DeleteObject API
D.
Migrate the log data to a 16 T8 Amazon Elastic Block Store (Amazon EBS) volume Create a snapshot of the EBS volume
Archive the data to Amazon S3 Glacier and apply a Vault Lock policy
Explanation: To securely and cost-effectively retain log data archives for several years, the company should do the following:
Archive the data to Amazon S3 Glacier and apply a Vault Lock policy. This allows the company to use a low-cost storage class that is designed for long-term archival of data that is rarely accessed. It also allows the company to enforce compliance controls on their S3 Glacier vault by locking a vault access policy that cannot be changed.
A company's Security Engineer is copying all application logs to centralized Amazon S3 buckets. Currently, each of the company's applications is in its own IAM account, and logs are pushed into S3 buckets associated with each account. The Engineer will deploy an IAM Lambda function into each account that copies the relevant log files to the centralized S3 bucket.
The Security Engineer is unable to access the log files in the centralized S3 bucket. The Engineer's IAM user policy from the centralized account looks like this:
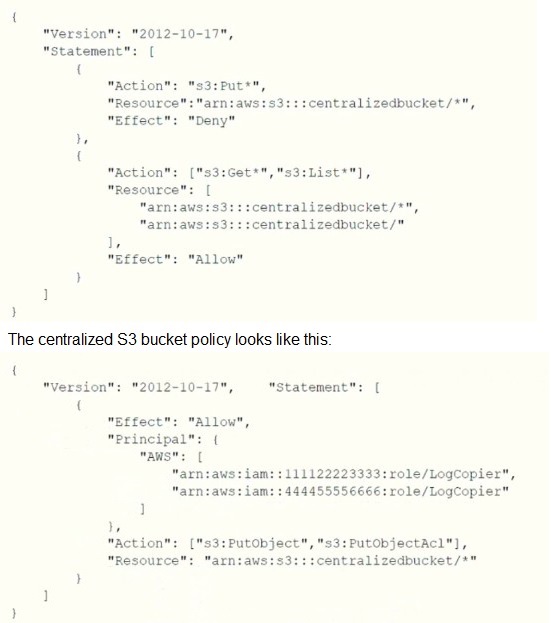
Why is the Security Engineer unable to access the log files?
A.
The S3 bucket policy does not explicitly allow the Security Engineer access to the objects in the bucket.
B.
The object ACLs are not being updated to allow the users within the centralized account to access the objects
C.
The Security Engineers IAM policy does not grant permissions to read objects in the S3 bucket
D.
The s3:PutObject and s3:PutObjectAcl permissions should be applied at the S3 bucket level
The Security Engineers IAM policy does not grant permissions to read objects in the S3 bucket
You need to create a policy and apply it for just an individual user. How could you accomplish this in the right way?
Please select:
A.
Add an IAM managed policy for the user
B.
Add a service policy for the user
C.
Add an IAM role for the user
D.
Add an inline policy for the user
Add an inline policy for the user
Explanation: Options A and B are incorrect since you need to add an inline policy just for the user Option C is invalid because you don't assign an IAM role to a user The IAM Documentation mentions the following:
An inline policy is a policy that's embedded in a principal entity (a user, group, or role)—that is, the policy is an inherent part of the principal entity. You can create a policy and embed it in a principal entity, either when you create the principal entity or later.
For more information on IAM Access and Inline policies, just browse to the below URL:
https://docs.IAM.amazon.com/IAM/latest/UserGuide/access
The correct answer is: Add an inline policy for the user Submit your Feedback/Queries to our Experts
While securing the connection between a company's VPC and its on-premises data center, a Security Engineer sent a ping command from an on-premises host (IP address 203.0.113.12) to an Amazon EC2 instance (IP address 172.31.16.139). The ping command did not return a response. The flow log in the VPC showed the following:
2 123456789010 eni-1235b8ca 203.0.113.12 172.31.16.139 0 0 1 4 336 1432917027 1432917142 ACCEPT OK
2 123456789010 eni-1235b8ca 172.31.16.139 203.0.113.12 0 0 1 4 336 1432917094 1432917142 REJECT OK
What action should be performed to allow the ping to work?
A.
In the security group of the EC2 instance, allow inbound ICMP traffic.
B.
In the security group of the EC2 instance, allow outbound ICMP traffic.
C.
In the VPC's NACL, allow inbound ICMP traffic.
D.
In the VPC's NACL, allow outbound ICMP traffic.
In the VPC's NACL, allow outbound ICMP traffic.
A company's Security Auditor discovers that users are able to assume roles without using multi-factor authentication (MFA). An example of a current policy being applied to these users is as follows:
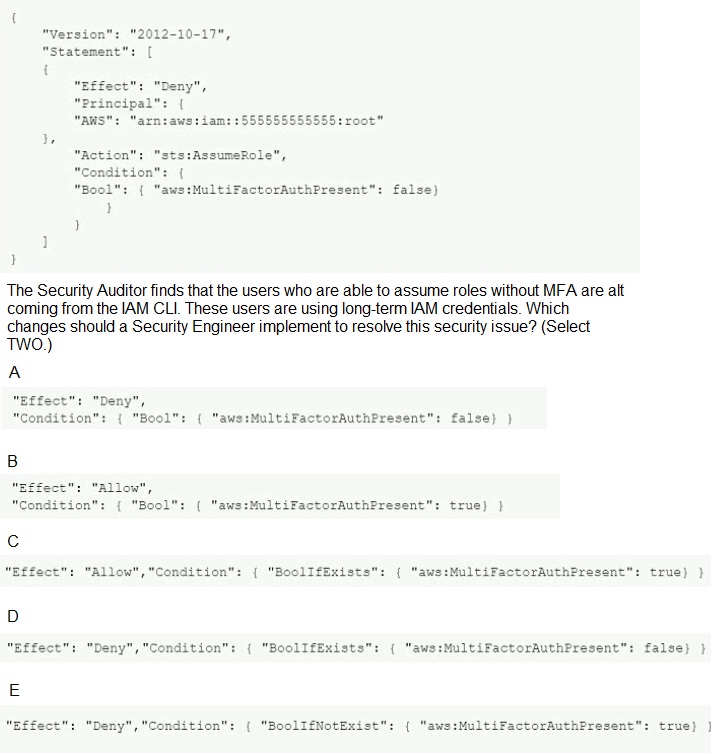
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Option D
| Page 3 out of 58 Pages |
| Previous |