
- Email support@dumps4free.com

A security engineer is troubleshooting an AWS Lambda function that is named MyLambdaFunction. The function is encountering an error when the function attempts to read the objects in an Amazon S3 bucket that is named DOC-EXAMPLE-BUCKET. The S3 bucket has the following bucket policy:
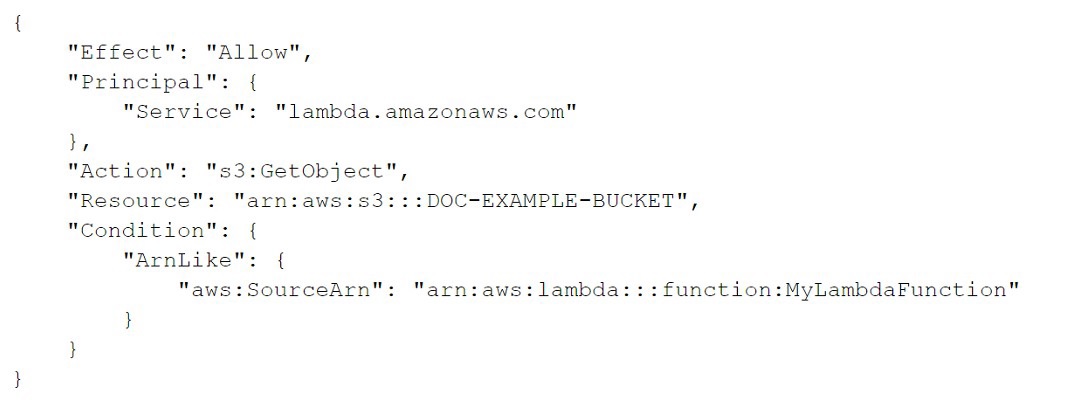
Which change should the security engineer make to the policy to ensure that the Lambda function can read the bucket objects?
A.
Remove the Condition element. Change the Principal element to the following:
{
“AWS”: “arn "aws" ::: lambda ::: function:MyLambdaFunction”
}
B.
Change the Action element to the following:
" s3:GetObject*"
" s3:GetBucket*"
C.
Change the Resource element to "arn:aws:s3:::DOC-EXAMPLE-BUCKET/*".
D.
Change the Resource element to "arn:aws:lambda:::function:MyLambdaFunction".
Change the Principal element to the following:
{
“Service”: “s3.amazonaws.com”
}
An ecommerce website was down for 1 hour following a DDoS attack Users were unable to connect to the website during the attack period. The ecommerce company's security team is worried about future potential attacks and wants to prepare for such events The company needs to minimize downtime in its response to similar attacks in the future. Which steps would help achieve this9 (Select TWO )
A.
Enable Amazon GuardDuty to automatically monitor for malicious activity and block unauthorized access.
B.
Subscribe to IAM Shield Advanced and reach out to IAM Support in the event of an attack.
C.
Use VPC Flow Logs to monitor network: traffic and an IAM Lambda function to automatically block an attacker's IP using security groups.
D.
Set up an Amazon CloudWatch Events rule to monitor the IAM CloudTrail events in real time use IAM Config rules to audit the configuration, and use IAM Systems Manager for remediation.
E.
Use IAM WAF to create rules to respond to such attacks
Company A has an AWS account that is named Account A. Company A recently acquired Company B, which has an AWS account that is named Account B. Company B stores its files in an Amazon S3 bucket. The administrators need to give a user from Account A full access to the S3 bucket in Account B. After the administrators adjust the IAM permissions for the user in AccountA to access the S3 bucket in Account B, the user still cannot access any files in the S3 bucket. Which solution will resolve this issue?
A.
In Account B, create a bucket ACL to allow the user from Account A to access the S3 bucket in Account B.
B.
In Account B, create an object ACL to allow the user from Account A to access all the objects in the S3 bucket in Account B.
C.
In Account B, create a bucket policy to allow the user from Account A to access the S3 bucket in Account B.
D.
In Account B, create a user policy to allow the user from Account A to access the S3 Bucket in Account B.
A security engineer needs to create an IAM Key Management Service <IAM KMS) key that will De used to encrypt all data stored in a company’s Amazon S3 Buckets in the us-west-1 Region. The key will use server-side encryption. Usage of the key must be limited to requests coming from Amazon S3 within the company's account. Which statement in the KMS key policy will meet these requirements?

A.
Option A
B.
Option B
C.
Option C
A company is using Amazon Route 53 Resolver for its hybrid DNS infrastructure. The company has set up Route 53 Resolver forwarding rules for authoritative domains that are hosted on on-premises DNS servers. A new security mandate requires the company to implement a solution to log and query DNS traffic that goes to the on-premises DNS servers. The logs must show details of the source IP address of the instance from which the query originated. The logs also must show the DNS name that was requested in Route 53 Resolver. Which solution will meet these requirements?
A.
Use VPC Traffic Mirroring. Configure all relevant elastic network interfaces as the traffic source, include amazon-dns in the mirror filter, and set Amazon CloudWatch Logs as the mirror target. Use CloudWatch Insights on the mirror session logs to run queries on the source IP address and DNS name.
B.
Configure VPC flow logs on all relevant VPCs. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
C.
Configure Route 53 Resolver query logging on all relevant VPCs. Send the logs to Amazon CloudWatch Logs. Use CloudWatch Insights to run queries on the source IP address and DNS name.
D.
Modify the Route 53 Resolver rules on the authoritative domains that forward to the onpremises DNS servers. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
| Page 13 out of 58 Pages |
| Previous |