
- Email support@dumps4free.com

During the TMS instance activation, a tenant (Customer) provides the following information for the fields in the Activation - Step 2 of 2 window.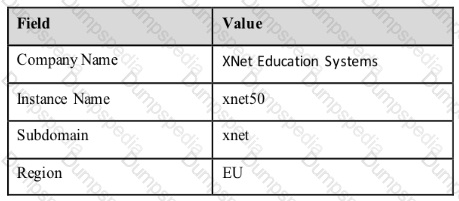
During the service instance provisioning which three DNS host names are created? (Choose three.)
A.
cc-xnet50.traps.paloaltonetworks.com
B.
hc-xnet50.traps.paloaltonetworks.com
C.
cc-xnet.traps.paloaltonetworks.com
D.
cc.xnet50traps.paloaltonetworks.com
E.
xnettraps.paloaltonetworks.com
F.
ch-xnet.traps.paloaltonetworks.com
cc-xnet50.traps.paloaltonetworks.com
cc-xnet.traps.paloaltonetworks.com
ch-xnet.traps.paloaltonetworks.com
What is the retention requirement for Cortex Data Lake sizing?
A.
number of endpoints
B.
number of VM-Series NGFW
C.
number of days
D.
logs per second
number of days
https://docs.paloaltonetworks.com/cortex/cortex-data-lake/cortex-data-lake-getting-started/get-started-with-cortex
How does an "inline" auto-extract task affect playbook execution?
A.
Doesn't wait until the indicators are enriched and continues executing the next step
B.
Doesn't wait until the indicators are enriched but populate context data before executing the next
C.
step. Wait until the indicators are enriched but doesn't populate context data before executing the next
step.
D.
Wait until the indicators are enriched and populate context data before executing the next step.
Wait until the indicators are enriched and populate context data before executing the next step.
An Administrator is alerted to a Suspicious Process Creation security event from multiple users. The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
A.
With the Malware Security profile, disable the "Prevent Malicious Child Process Execution" module
B.
Within the Malware Security profile add the specific parent process, child process, and command line argument to the child process whitelist
C.
In the Cortex XDR security event, review the specific parent process, child process, and command line arguments
D.
Contact support and ask for a security exception
Within the Malware Security profile add the specific parent process, child process, and command line argument to the child process whitelist
In the Cortex XDR security event, review the specific parent process, child process, and command line arguments
When integrating with Splunk, what will allow you to push alerts into Cortex XSOAR via the REST API?
A.
splunk-get-alerts integration command
B.
Cortex XSOAR TA App for Splunk
C.
SplunkSearch automation
D.
SplunkGO integration
Cortex XSOAR TA App for Splunk
| Page 1 out of 12 Pages |