
- Email support@dumps4free.com

Refer to the exhibit.
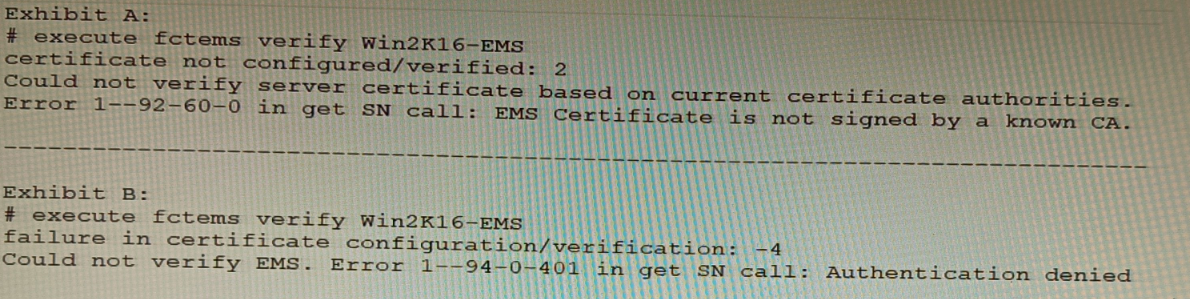
The exhibit shows two error messages from a FortiGate root Security Fabric device when
you try to configure a new connection to a FortiClient EMS Server.
Referring to the exhibit, which two actions will fix these errors? (Choose two.)
A. Verify that the CRL is accessible from the root FortiGate
B. Export and import the FortiClient EMS server certificate to the root FortiGate.
C. Install a new known CA on the Win2K16-EMS server.
D. Authorize the root FortiGate on the FortiClient EMS
Explanation:
A is correct because the error message "The CRL is not accessible" indicates that
the root FortiGate cannot access the CRL for the FortiClient EMS server. Verifying
that the CRL is accessible will fix this error.
D is correct because the error message "The FortiClient EMS server is not
authorized" indicates that the root FortiGate is not authorized to connect to the
FortiClient EMS server. Authorizing the root FortiGate on the FortiClient EMS
server will fix this error.
The other options are incorrect. Option B is incorrect because exporting and importing the
FortiClient EMS server certificate to the root FortiGate will not fix the CRL error. Option C is
incorrect because installing a new known CA on the Win2K16-EMS server will not fix the
authorization error.
Refer to the exhibits.
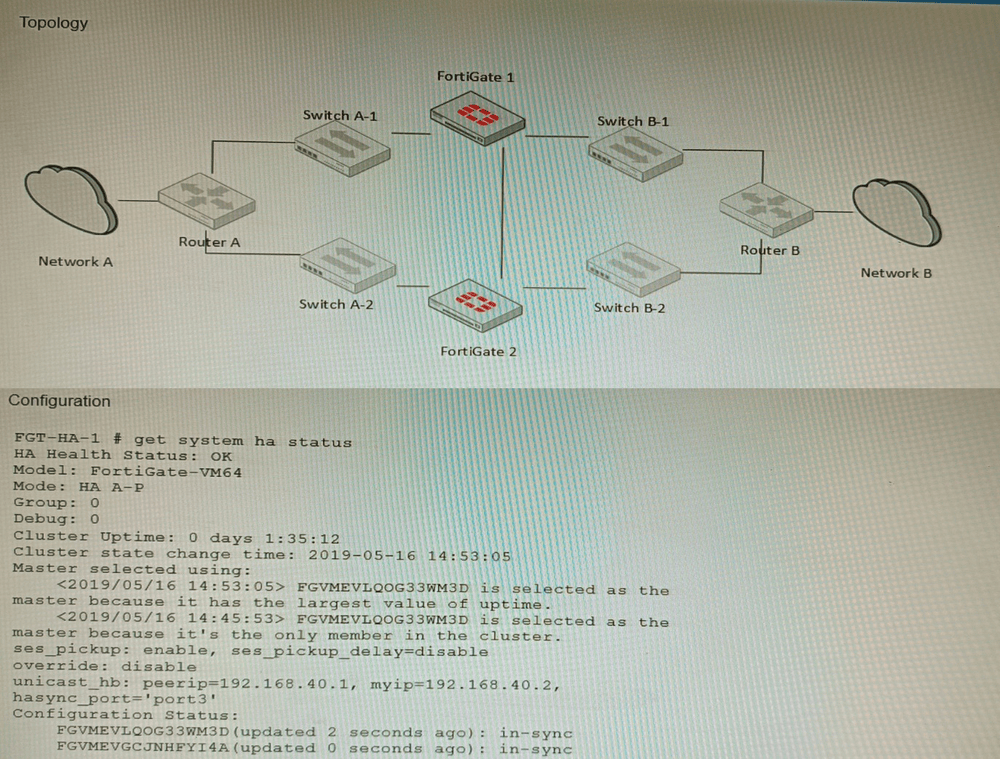
The exhibits show a FortiGate network topology and the output of the status of high
availability on the FortiGate.
Given this information, which statement is correct?
A. The ethertype values of the HA packets are 0x8890, 0x8891, and 0x8892
B. The cluster mode can support a maximum of four (4) FortiGate VMs
C. The cluster members are on the same network and the IP addresses were statically assigned.
D. FGVMEVLQOG33WM3D and FGVMEVGCJNHFYI4A share a virtual MAC address.
Explanation: The output of the status of high availability on the FortiGate shows that the cluster mode is active-passive, which means that only one FortiGate unit is active at a time, while the other unit is in standby mode. The active unit handles all traffic and also sends HA heartbeat packets to monitor the standby unit. The standby unit becomes active if it stops receiving heartbeat packets from the active unit, or if it receives a higher priority from another cluster unit. In active-passive mode, all cluster units share a virtual MAC address for each interface, which is used as the source MAC address for all packets forwarded by the cluster.
Refer to the exhibits.
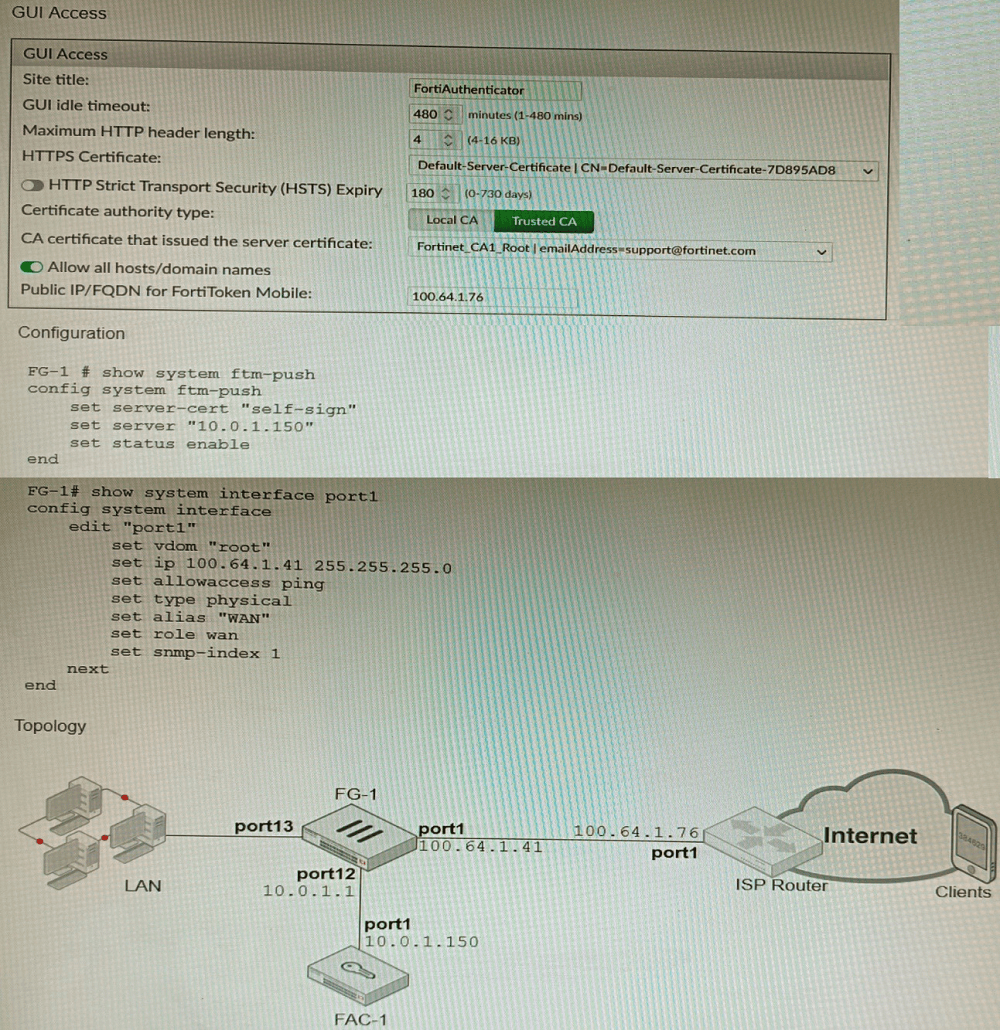
An administrator has configured a FortiGate and Forti Authenticator for two-factor
authentication with FortiToken push notifications for their SSL VPN login. Upon initial
review of the setup, the administrator has discovered that the customers can manually type
in their two-factor code and authenticate but push notifications do not work
Based on the information given in the exhibits, what must be done to fix this?
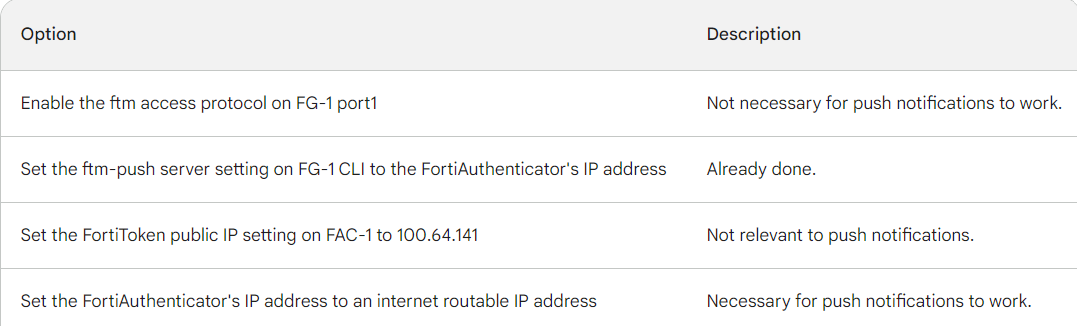
A. On FG-1 port1, the ftm access protocol must be enabled.
B. FAC-1 must have an internet routable IP address for push notifications.
C. On FG-1 CLI, the ftm-push server setting must point to 100.64.141.
D. On FAC-1, the FortiToken public IP setting must point to 100.64.1 41
Explanation: FortiToken push notifications require that the FortiAuthenticator has an
internet routable IP address. This is because the FortiAuthenticator uses this IP address to
send push notifications to the FortiGate.
The other options are not correct. Enabling the ftm access protocol on FG-1 port1 is not
necessary for push notifications to work. The ftm-push server setting on FG-1 CLI should
already point to the FortiAuthenticator's IP address. The FortiToken public IP setting on FAC-1 is not relevant to push notifications.
Here is a table that summarizes the different options:
Refer to the exhibit, which shows a VPN topology.
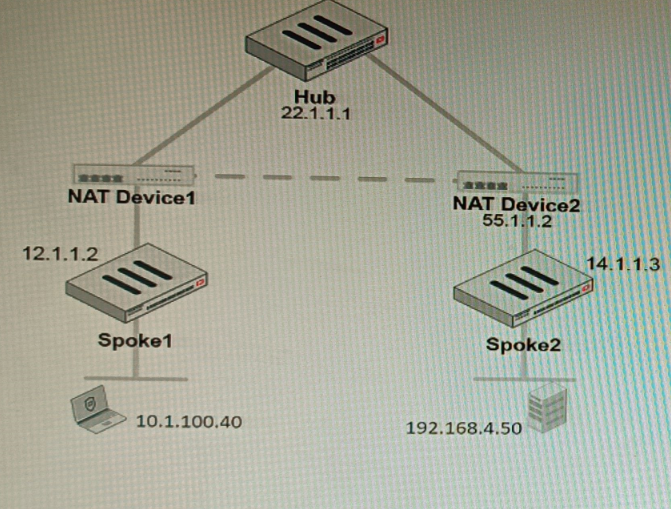
The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50
Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this
environment?
A. All the session traffic will pass through the Hub
B. The TCP port 21 must be allowed on the NAT Device2
C. ADVPN is not supported when spokes are behind NAT
D. Spoke1 will establish an ADVPN shortcut to Spoke2
Explanation: D is correct because Spoke1 will establish an ADVPN shortcut to Spoke2 when it detects that there is a demand for traffic between them. This is explained in the Fortinet Community article on Technical Tip: Fortinet Auto Discovery VPN (ADVPN) under Summary - ADVPN sequence of events.
Refer to the exhibit showing a firewall policy configuration.
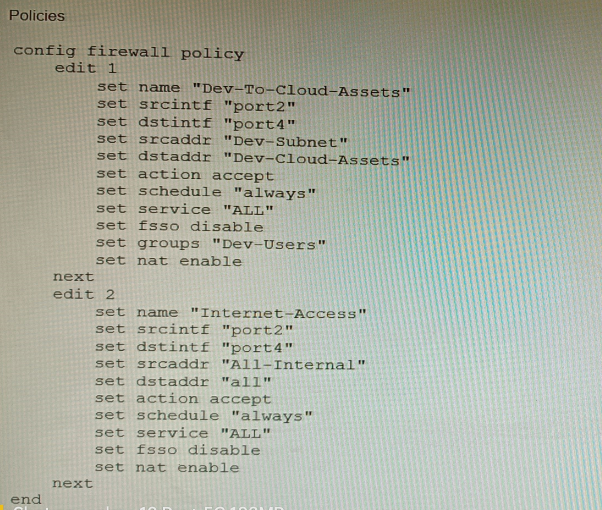
To prevent unauthorized access of their cloud assets, an administrator wants to enforce
authentication on firewall policy ID 1.
What change does the administrator need to make?

A. Option A
B. Option B
C. Option C
D. Option D
Explanation: The firewall policy in the exhibit allows all traffic from the internal network to
the cloud. To enforce authentication on this traffic, the administrator needs to add the authon-
demand option to the policy. This option will force all users to authenticate before they are allowed to access the cloud.
The following is the correct configuration:
config firewall policy
edit 1
set srcintf "internal"
set dstintf "wan1"
set srcaddr "all"
set dstaddr "all"
set service "all"
set action accept
set auth-on-demand enable
| Page 3 out of 12 Pages |
| Previous |