
- Email support@dumps4free.com

What is an example of a Layer2 wireless threat that a wireless intrusion detection system
(WIDS) should detect?
A.
802.11 association floods
B.
RF jamming
C.
Bluetooth interference
D.
spyware
802.11 association floods
Refer to the exhibit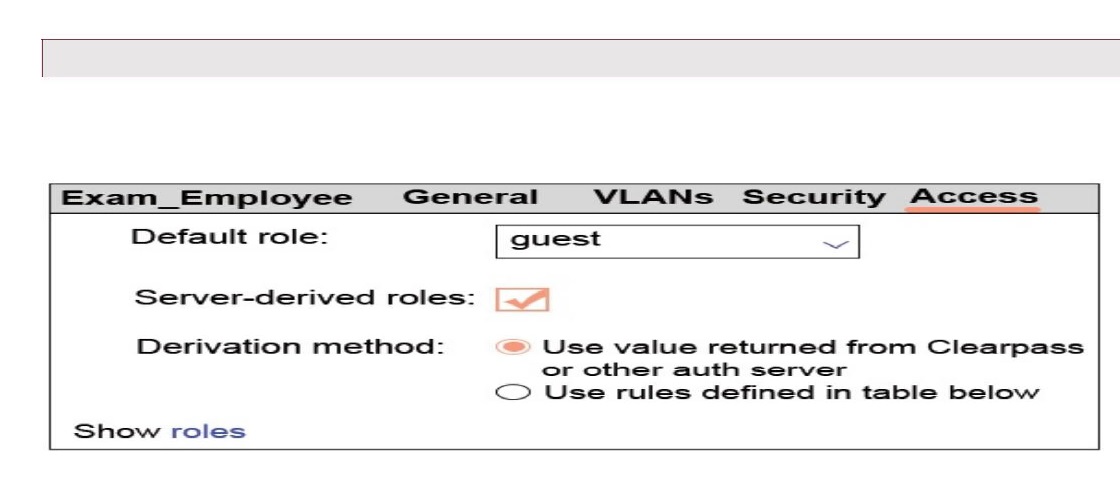
A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?
A.
users who successfully authenticate and are assigned to the default role by the RADIUS server
B.
users who successfully authenticate and are not assigned a different role by
the RADIUS server
C.
users who have connected to the SSID, but have not yet attempted authentication
D.
users who fail authentication
users who successfully authenticate and are not assigned a different role by
the RADIUS server
A network administrator wants to assign an authentication server group to the
WPA2-Enterprise WLAN. Which profile should the administrator modify?
A.
Virtual AP
B.
SSID
C.
AAA
D.
L2 Authentication
AAA
If the decrypt-tunnel forwarding mode is selected in an employee WLAN, where is the user traffic decrypted?
A.
at the switch
B.
at the AP
C.
at the controller
D.
at the RADIUS server
at the AP
An Aruba Mobility Master (MM)-based solution has a WLAN that uses WPA2-
Enterprise security. A test login on a wireless client fails.
How can a network administrator determine whether the RADIUS server rejected the credentials or another issue occurred?
A.
View Technical Support information for the MM.
B.
Ping the IP address configured as the RADIUS server.
C.
Use the MM AAA Server Test Diagnostic tool.
D.
Use the tools in the MM Dashboard > Security window.
Use the MM AAA Server Test Diagnostic tool.
| Page 4 out of 26 Pages |
| Previous |