
- Email support@dumps4free.com

An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
A. It redirects the client request to the access proxy.
B. It uses the access proxy.
C. It defines ZTNA server.
D. It only uses ZTNA tags to control access for endpoints.
Refer to the exhibit.
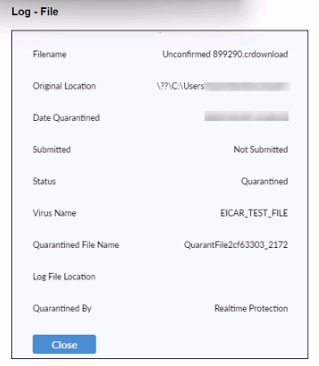
Based on the FortiClient tog details shown in the exhibit, which two statements ace true?
(Choose two.)
A. The filename Is Unconfirmed 899290.crdovnload.
B. The file status is Quarantined
C. The filename is sent to FortiSandbox for further inspection.
D. The file location is \??\D:\Users\.
Refer to the exhibit.
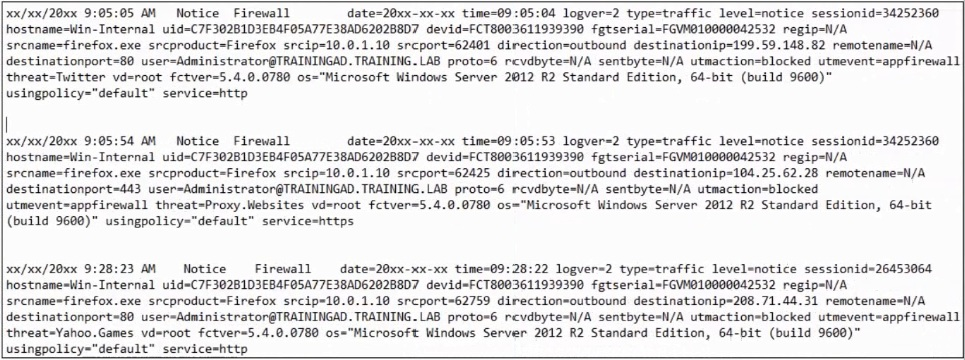
Based on the FortiClient logs shown in the exhibit which application is blocked by the
application firewall?
A. Twitter
B. Facebook
C. Internet Explorer
D. Firefox
Refer to the exhibit, which shows the endpoint summary information on FortiClient EMS.
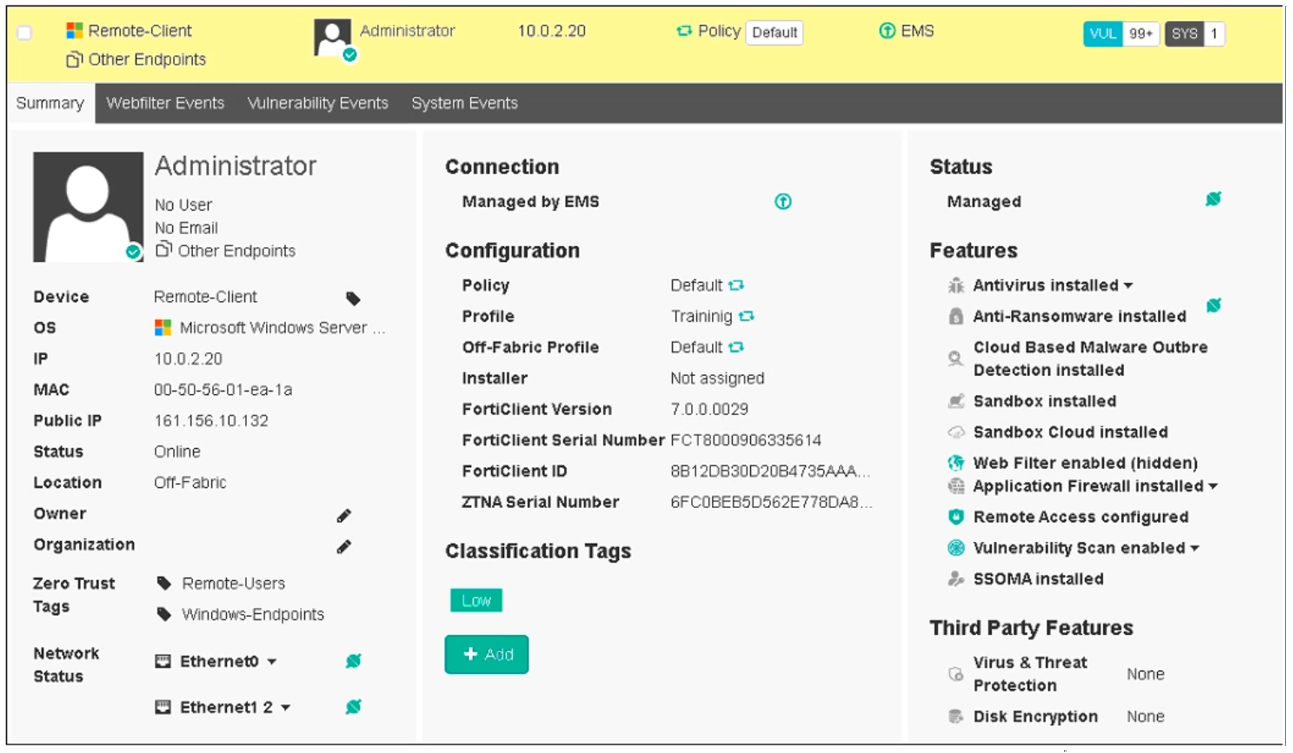
What two conclusions can you make based on the Remote-Client status shown above?
(Choose two.)
A. The endpoint is classified as at risk.
B. The endpoint has been assigned the Default endpoint policy.
C. The endpoint is configured to support FortiSandbox.
D. The endpoint is currently off-net.
Which three features does FortiClient endpoint security include? (Choose three.)
A. DLP
B. Vulnerability management
C. L2TP
D. lPsec
E. Real-lime protection
| Page 3 out of 11 Pages |
| Previous |