
- Email support@dumps4free.com

Software firewalls work at which layer of the OSI model?
A.
Data Link
B.
Network
C.
Transport
D.
Application
Data Link
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the
service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental
publishing, and more have all been sources of major leaks over the last 15 years.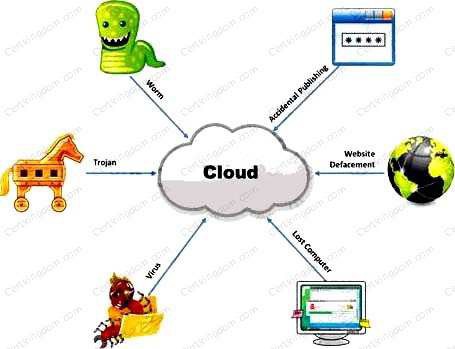
What is the biggest source of data leaks in organizations today?
A.
Weak passwords and lack of identity management
B.
Insufficient IT security budget
C.
Rogue employees and insider attacks
D.
Vulnerabilities, risks, and threats facing Web sites
Rogue employees and insider attacks
Which one of the following log analysis tools is used for analyzing the server’s log files?
A.
Performance Analysis of Logs tool
B.
Network Sniffer Interface Test tool
C.
Ka Log Analyzer tool
D.
Event Log Tracker tool
Ka Log Analyzer tool
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through social engineering
on-site visits, face-to-face interviews, and direct questionnaires?
A.
Active Information Gathering
B.
Pseudonymous Information Gathering
C.
Anonymous Information Gathering
D.
Open Source or Passive Information Gathering
Active Information Gathering
Vulnerability assessment is an examination of the ability of a system or application, including current security
procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a
computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of
additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any
misconfiguration and outdated content?
A.
Passive Assessment
B.
Host-based Assessment
C.
External Assessment
D.
Application Assessment
Application Assessment
| Page 4 out of 41 Pages |
| Previous |