
- Email support@dumps4free.com

What is the difference between penetration testing and vulnerability testing?
A.
Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
B.
Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
C.
Vulnerability testing is more expensive than penetration testing
D.
Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael
scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not
give a response. In what state are these ports?
A.
Filtered
B.
Stealth
C.
Closed
D.
Open
Open
Why is a legal agreement important to have before launching a penetration test?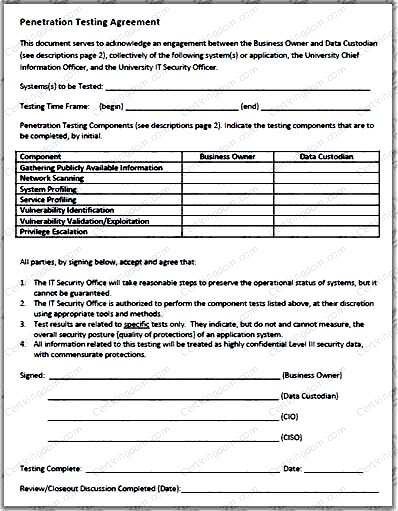
A.
Guarantees your consultant fees
B.
Allows you to perform a penetration test without the knowledge and consent of the organization's upper management
C.
It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
D.
It is important to ensure that the target organization has implemented mandatory security policies
It establishes the legality of the penetration test by documenting the scope of the project and the consent of the company.
Kimberly is studying to be an IT security analyst at a vocational school in her town. The school offers
many different programming as well as networking languages. What networking protocol language should she learn that
routers utilize?
A.
OSPF
B.
BPG
C.
ATM
D.
UDP
OSPF
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
A.
3001-3100
B.
5000-5099
C.
6666-6674
D.
0 – 1023
0 – 1023
| Page 1 out of 41 Pages |