
- Email support@dumps4free.com

Topic 1: Volume A
Drop the appropriate value to complete the formula
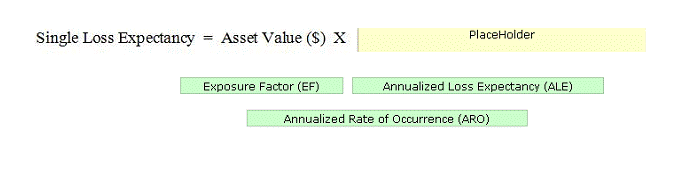
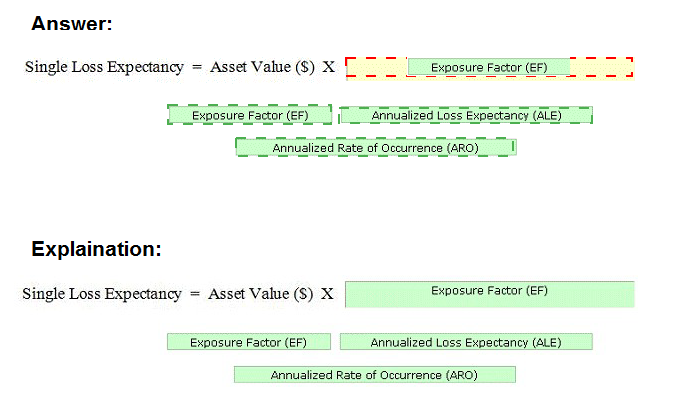
A Single Loss Expectancy (SLE) is the value in dollar ($) that is assigned to a single event. The SLE can be calculated by the following formula: SLE = Asset Value ($) X Exposure Factor (EF) The Exposure Factor (EF) represents the % of assets loss caused by a threat. The EF is required to calculate the Single Loss Expectancy (SLE). The Annualized Loss Expectancy (ALE) can be calculated by multiplying the Single Loss Expectancy (SLE) with the Annualized Rate of Occurrence (ARO). Annualized Loss Expectancy (ALE) = Single Loss Expectancy (SLE) X Annualized Rate of Occurrence (ARO) Annualized Rate of Occurrence (ARO) is a number that represents the estimated frequency in which a threat is expected to occur. It is calculated based upon the probability of the event occurring and the number of employees that could make that event occur.
What component of the change management system is responsible for evaluating, testing, and documenting changes created to the project scope?
A.
Project Management Information System
B.
Integrated Change Control
C.
Configuration Management System
D.
Scope Verification
Configuration Management System
Explanation: The change management system is comprised of several components that guide the change request through the process. When a change request is made that will affect the project scope. The Configuration Management System evaluates the change request and documents the features and functions of the change on the project scope.
The organization level is the Tier 1 and it addresses risks from an organizational perspective. What are the various Tier 1 activities? Each correct answer represents a complete solution. Choose all that apply
A.
The organization plans to use the degree and type of oversight, to ensure that the risk management strategy is being effectively carried out.
B.
The level of risk tolerance.
C.
The techniques and methodologies an organization plans to employ, to evaluate information system-related security risks.
D.
The RMF primarily operates at Tier 1.
The organization plans to use the degree and type of oversight, to ensure that the risk management strategy is being effectively carried out.
The level of risk tolerance.
The techniques and methodologies an organization plans to employ, to evaluate information system-related security risks.
Explanation: The Organization Level is the Tier 1, and it addresses risks from an organizational perspective. It includes the following points: The techniques and methodologies an organization plans to employ, to evaluate information system-related security risks. During risk assessment, the methods and procedures the organization plans to use, to evaluate the significance of the risks identified. The types and extent of risk mitigation measures the organization plans to employ, to address identified risks. The level of risk tolerance. According to the environment of operation, how the organization plans to monitor risks on an ongoing basis, given the inevitable changes to organizational information system. The organization plans to use the degree and type of oversight, in order to ensure that the risk management strategy is being effectively carried out.Answer: D is incorrect. The RMF primarily operates at Tier 3.
Which of the following types of redundancy prevents attacks in which an attacker can get physical control of a machine, insert unauthorized software, and alter data?
A.
Data redundancy
B.
Hardware redundancy
C.
Process redundancy
D.
Application redundancy
Process redundancy
Explanation: Process redundancy permits software to run simultaneously on multiple geographically distributed locations, with voting on results. It prevents attacks in which an attacker can get physical control of a machine, insert unauthorized software, and alter data.
You are the project manager of the CUL project in your organization. You and the project team are assessing the risk events and creating a probability and impact matrix for the identified risks. Which one of the following statements best describes the requirements for the data type used in qualitative risk analysis?
A.
A qualitative risk analysis encourages biased data to reveal risk tolerances.
B.
A qualitative risk analysis required unbiased stakeholders with biased risk tolerances.
C.
A qualitative risk analysis requires accurate and unbiased data if it is to be credible.
D.
A qualitative risk analysis requires fast and simple data to complete the analysis.
A qualitative risk analysis requires accurate and unbiased data if it is to be credible.
Explanation: Of all the choices only this answer is accurate. The PMBOK clearly states that the data must be accurate and unbiased to be credible. Answer: D is incorrect. This is not a valid statement about the qualitative risk analysis data. Answer: A is incorrect. This is not a valid statement about the qualitative risk analysis data. Answer: B is incorrect. This is not a valid statement about the qualitative risk analysis data.
| Page 15 out of 70 Pages |
| Previous |