
- Email support@dumps4free.com

Topic 2 : Pool B Jul-Aug-Sep
Which of the following is the BEST evidence that risk management is driving business decisions in an organization?
A.
Compliance breaches are addressed in a timely manner.
B.
Risk ownership is identified and assigned.
C.
Risk treatment options receive adequate funding.
D.
Residual risk is within risk tolerance.
Residual risk is within risk tolerance.
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments: After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments: Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?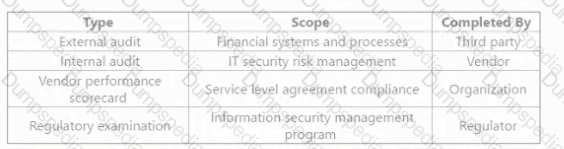
A.
External audit
B.
Internal audit
C.
Vendor performance scorecard
D.
Regulatory examination
Internal audit
Management has required information security awareness training to reduce the risk associated with credential compromise. What is the BEST way to assess the effectiveness of the training?
A.
Conduct social engineering testing.
B.
Audit security awareness training materials.
C.
Administer an end-of-training quiz.
D.
Perform a vulnerability assessment.
Conduct social engineering testing.
An organization has outsourced its IT security operations to a third party. Who is ULTIMATELY accountable for the risk associated with the outsourced operations?
A.
The third party s management
B.
The organization's management
C.
The control operators at the third party
D.
The organization's vendor management office
The organization's management
During an IT risk scenario review session, business executives question why they have been assigned ownership of IT-related risk scenarios. They feel IT risk is technical in nature and therefore should be owned by IT. Which of the following is the BEST way for the risk practitioner to address these concerns?
A.
Describe IT risk scenarios in terms of business risk.
B.
Recommend the formation of an executive risk council to oversee IT risk.
C.
Provide an estimate of IT system downtime if IT risk materializes.
D.
Educate business executives on IT risk concepts
Describe IT risk scenarios in terms of business risk.
| Page 22 out of 193 Pages |
| Previous |