
- Email support@dumps4free.com

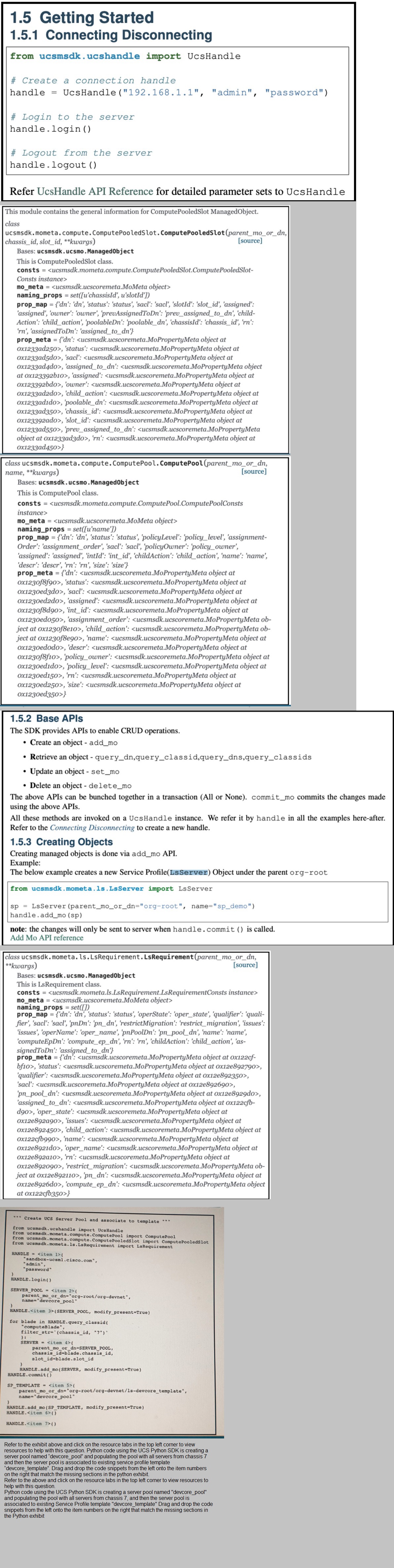

Refer to the exhibit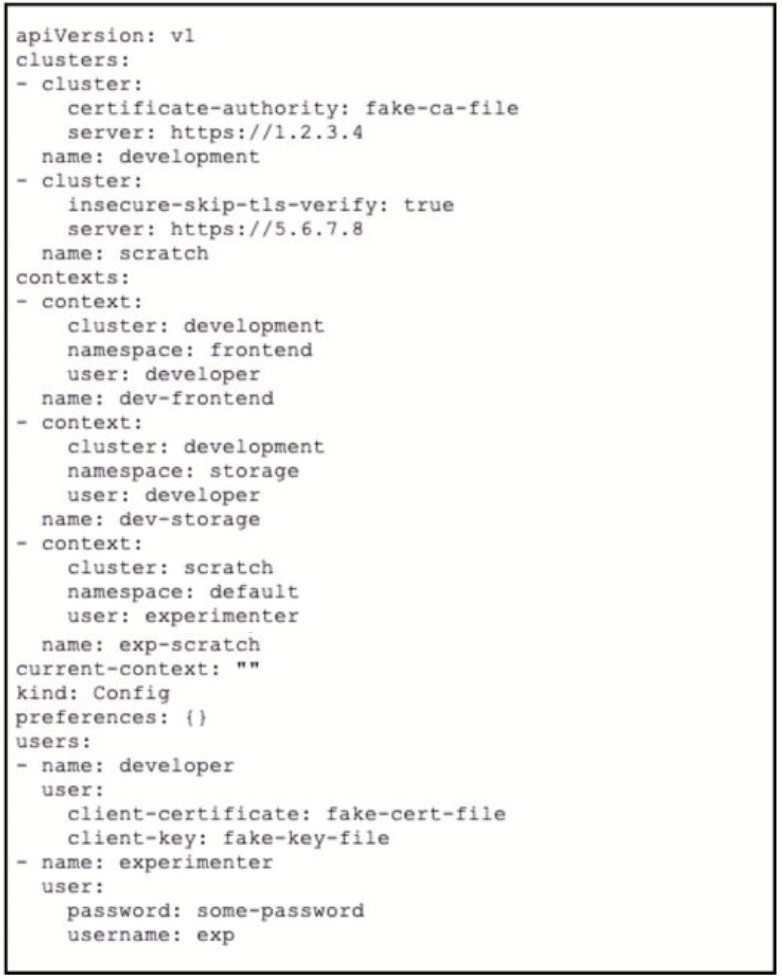
A kubeconfig file to manage access to Kubernetes clusters is shown. How many
Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than
using a certificate?
A.
three dusters; scratch
B.
three clusters: development
C.
two dusters; development
D.
two clusters: scratch
two clusters: scratch
Refer to the exhibit. 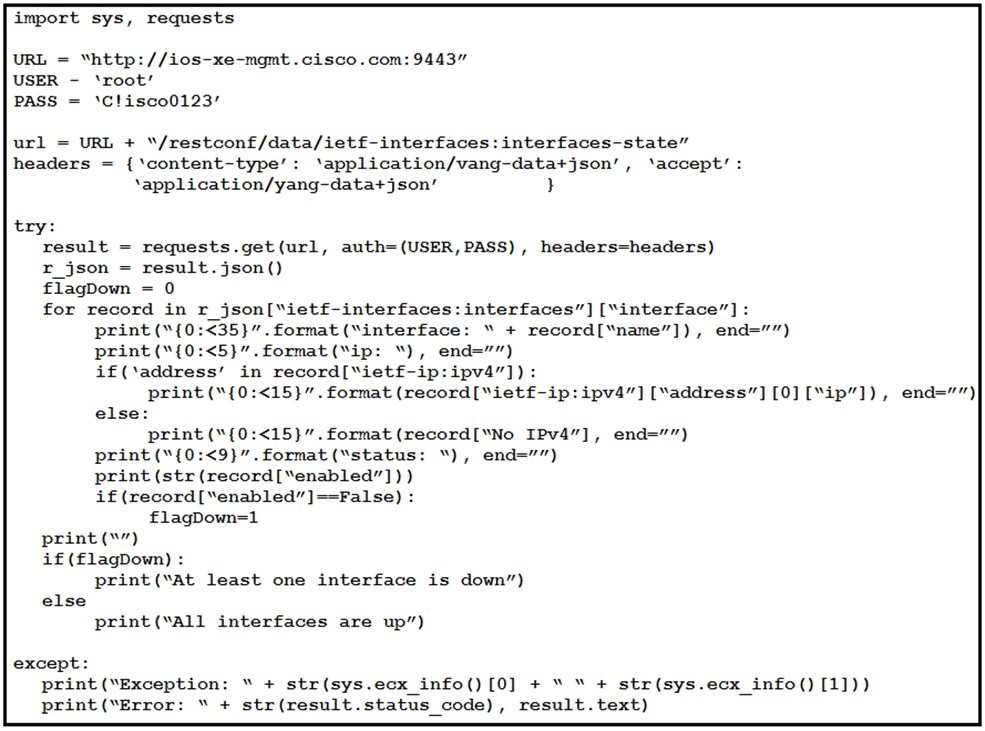
What is the output of this IOS-XE configuration program?
A.
interface operational status in IPv6 addresses
B.
interface administrative status in IPv4 addresses
C.
interface operational status in IPv4 addresses
D.
interface administrative status in IPv6 addresses
interface administrative status in IPv4 addresses
Application sometimes store configuration as constants in the code, which is a violation of
strict separation of configuration from code. Where should application configuration be
stored?
A.
environment variables
B.
YAML files
C.
Python libraries
D.
Dockerfiles
E.
INI files
environment variables
Which two statements about a stateless application are true? (Choose two.)
A.
Different requests can be processed by different servers.
B.
Requests are based only on information relayed with each request.
C.
Information about earlier requests must be kept and must be accessible.
D.
The same server must be used to process all requests that are linked to the same state.
E.
No state information can be shared across servers
Different requests can be processed by different servers.
Requests are based only on information relayed with each request.
| Page 8 out of 34 Pages |
| Previous |