
- Email support@dumps4free.com

The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been
stored in the environment variable meraki_url and the API key has been stored in
meraki_api_key. Which snippet presents the API call to configure, secure and enable an
SSID using the Meraki API?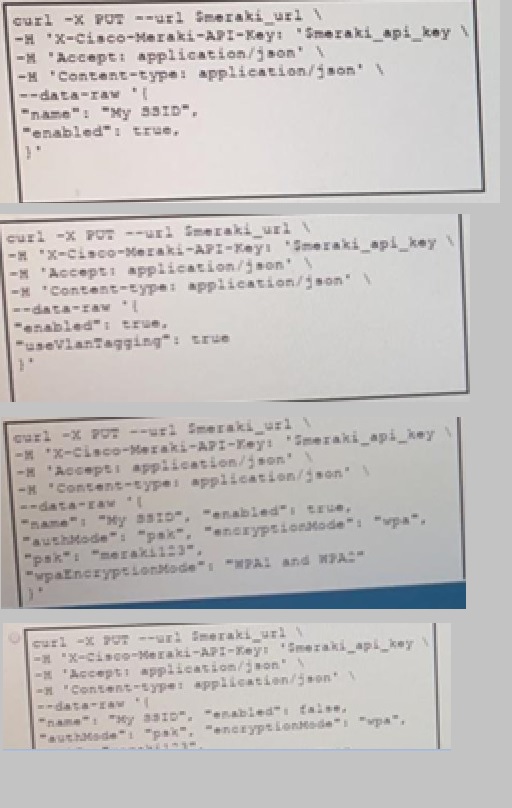
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C

Which two techniques protect against injection attacks? (Choose two.)
A.
input validation
B.
trim whitespace
C.
limit text areas to 255 characters
D.
string escaping of user free text and data entry
E.
only use dropdown, checkbox, and radio button fields
input validation
string escaping of user free text and data entry
What are two principles according to the build, release, run principle of the twelve-factor
app methodology?
(Choose two.)
A.
Code changes are able to be made at runtime.
B.
Separation between the build, release, and run phases.
C.
Releases should have a unique identifier.
D.
Existing releases are able to be mutated after creation.
E.
Release stage is responsible for compilation of assets and binaries
Separation between the build, release, and run phases.
Releases should have a unique identifier.
Reference: https://www.bmc.com/blogs/twelve-factor-app/
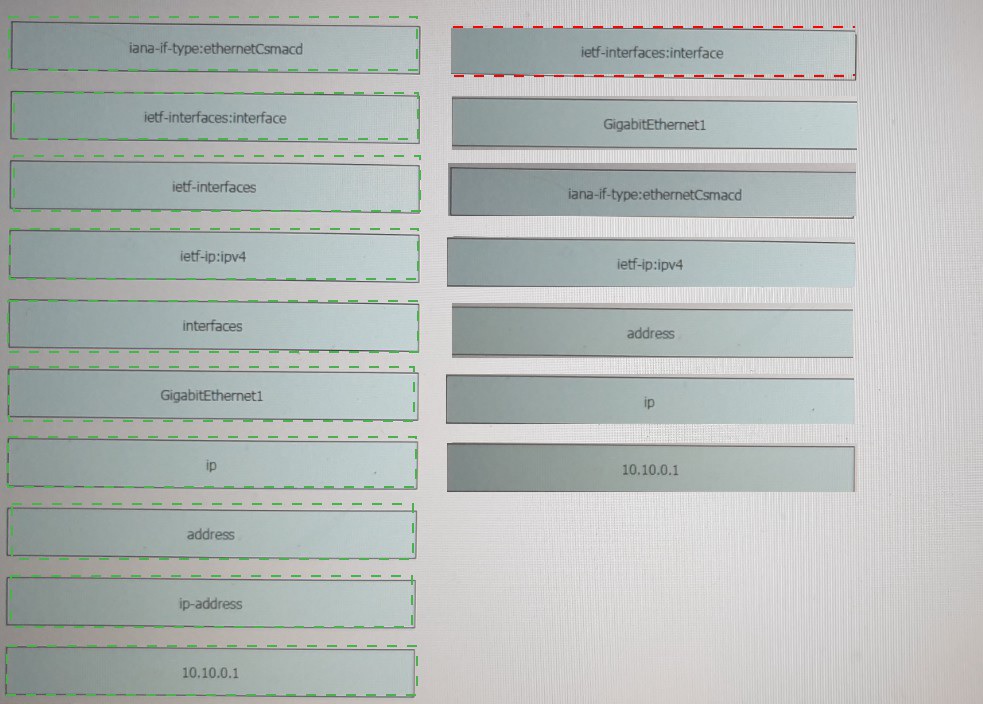
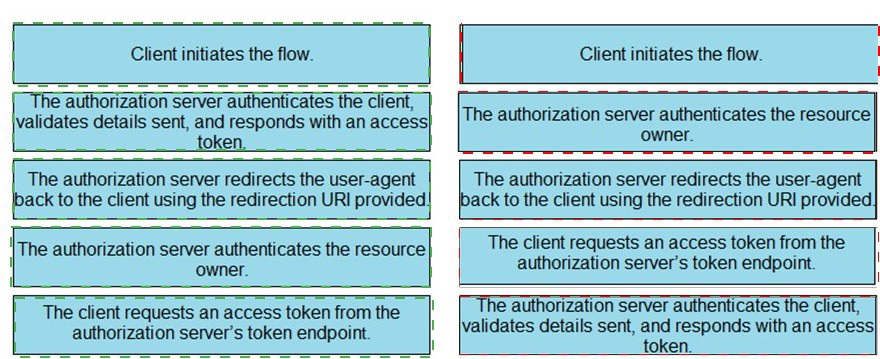
Refer to the exhibit.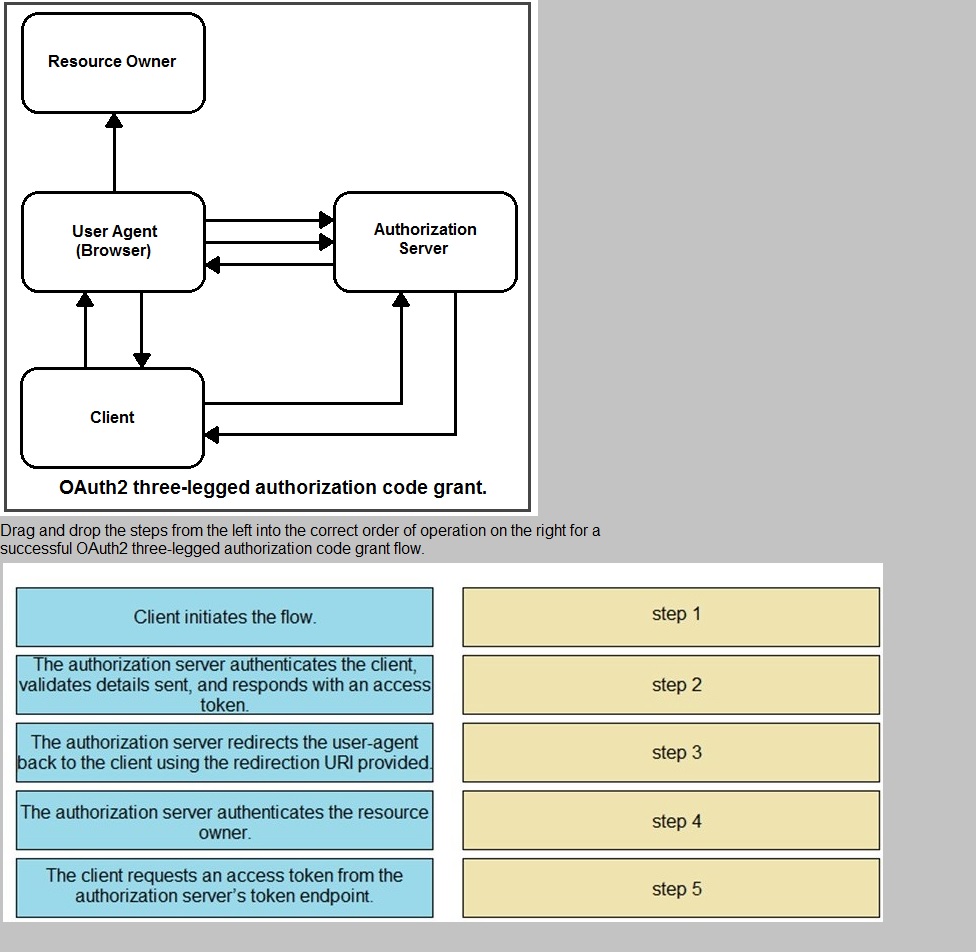
| Page 12 out of 34 Pages |
| Previous |