
- Email support@dumps4free.com

Topic 2: Exam Pool B
What is the function of SDN southbound API protocols?
A.
to allow for the dynamic configuration of control plane applications
B.
to enable the controller to make changes
C.
to enable the controller to use REST
D.
to allow for the static configuration of control plane applications
to enable the controller to make changes
https://www.ciscopress.com/articles/article.asp?p=3004581&seqNum=2
Note: Southbound APIs helps us communicate with data plane (not control plane)
applications
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
A.
Application Control
B.
Security Category Blocking
C.
Content Category Blocking
D.
File Analysis
Security Category Blocking
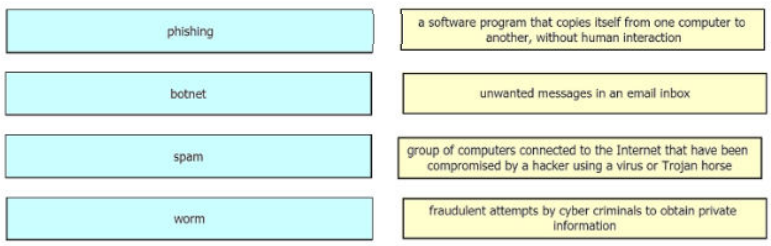
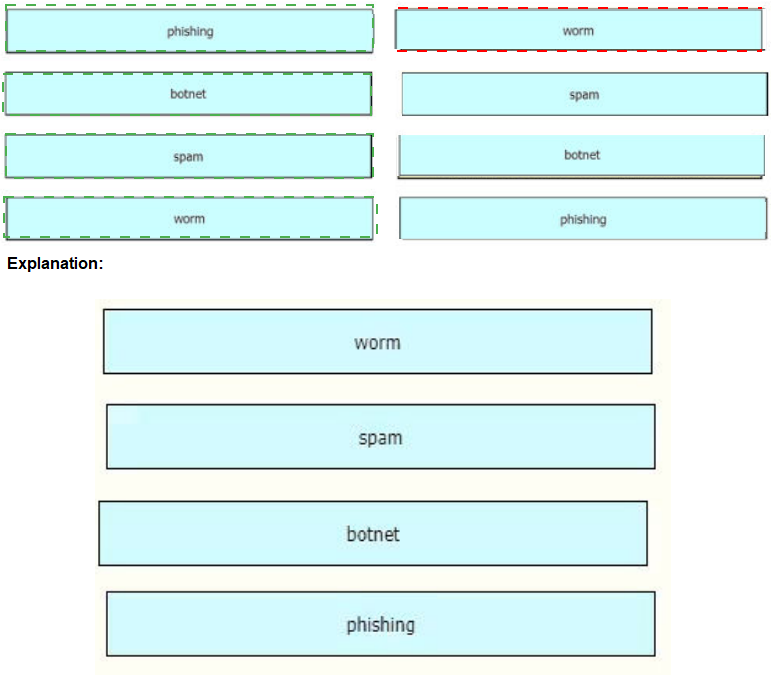
Drag and drop the common security threats from the left onto the definitions on the right.
Refer to the exhibit.
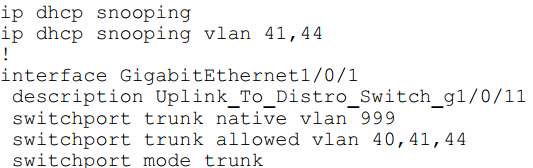
An organization is using DHCP Snooping within their network. A user on VLAN 41 on a
new switch is
complaining that an IP address is not being obtained. Which command should be
configured on the switch
interface in order to provide the user with network connectivity?
A.
ip dhcp snooping verify mac-address
B.
ip dhcp snooping limit 41
C.
ip dhcp snooping vlan 41
D.
ip dhcp snooping trust
ip dhcp snooping trust
ExplanationExplanationTo understand DHCP snooping we need to learn
about DHCP spoofing attack first.
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from
clients and answers them with fake DHCP Response before the authorized DHCP
Response comes to the clients. The fake DHCP Response often gives its IP address as the
client default gateway -> all the traffic sent from the client will go through the attacker
computer, the attacker becomes a “man-in-the-middle”.The attacker can have some ways
to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than
the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so
that it can’t send the DHCP Response.DHCP snooping can prevent DHCP spoofing
attacks. DHCP snooping is a Cisco Catalyst feature thatdetermines which switch ports can
respond to DHCP requests. Ports are identified as trusted and untrusted.
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all
types of DHCP
messages. All other ports on the switch are untrusted and can send only DHCP requests. If
a DHCP response is seen on an untrusted port, the port is shut down.
The port connected to a DHCP server should be configured as trusted port with the “ip dhcp snooping trust” command. Other ports connecting to hosts are untrusted ports by
default.
In this question, we need to configure the uplink to “trust” (under interface Gi1/0/1).
What is a characteristic of Cisco ASA Netflow v9 Secure Event Logging?
A.
It tracks flow-create, flow-teardown, and flow-denied events.
B.
It provides stateless IP flow tracking that exports all records of a specific flow.
C.
It tracks the flow continuously and provides updates every 10 seconds.
D.
Its events match all traffic classes in parallel.
It tracks flow-create, flow-teardown, and flow-denied events.
| Page 9 out of 126 Pages |
| Previous |