
- Email support@dumps4free.com

Topic 2: Exam Pool B
Due to a traffic storm on the network, two interfaces were error-disabled, and both
interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service?
(Choose two)
A.
Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports
after the pre
configured interval.
B.
Use EEM to have the ports return to service automatically in less than 300 seconds
C.
Enter the shutdown and no shutdown commands on the interfaces
D.
Enable the snmp-server enable traps command and wait 300 seconds
E.
Ensure that interfaces are configured with the error-disable detection and recovery
feature
Enter the shutdown and no shutdown commands on the interfaces
Ensure that interfaces are configured with the error-disable detection and recovery
feature
You can also bring up the port by using these
commands:+ The “shutdown” interface configuration command followed by the “no
shutdown” interface configurationcommand restarts the disabled port.+ The “errdisable
recovery cause …” global configuration command enables the timer to automatically
recover error-disabled state, and the “errdisable recovery interval interval” global
configuration command specifies the time to recover error-disabled state.
When planning a VPN deployment, for which reason does an engineer opt for an
active/active FlexVPN
configuration as opposed to DMVPN?
A.
Multiple routers or VRFs are required
B.
Traffic is distributed statically by default
C.
Floating static routes are required
D.
HSRP is used for faliover
Traffic is distributed statically by default
What is a characteristic of Firepower NGIPS inline deployment mode?
A.
ASA with Firepower module cannot be deployed.
B.
It cannot take actions such as blocking traffic.
C.
It is out-of-band from traffic.
D.
It must have inline interface pairs configured
It must have inline interface pairs configured
Which term describes when the Cisco Firepower downloads threat intelligence updates
from Cisco Talos?
A.
consumption
B.
sharing
C.
analysis
D.
authoring
consumption
we will showcase Cisco Threat Intelligence
Director (CTID) an exciting feature on Cisco’s FirepowerManagement Center (FMC)
product offering that automates the operationalization of threat intelligence. TID has the
ability to consume threat intelligence via STIX over TAXII and allows uploads/downloads of
STIX and simple blacklists. Reference: https://blogs.cisco.com/developer/automate-threatintelligence-
using-cisco-threat-intelligencedirector
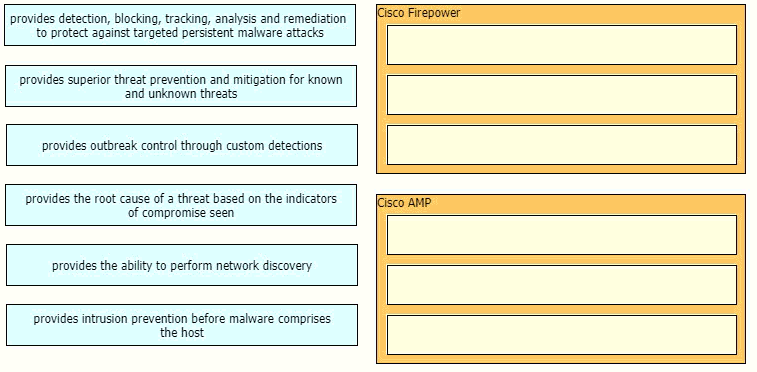
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the
appropriate category on the right.

Application
Description automatically generated with low confidence
ExplanationThe Firepower System uses network discovery and identity policies to collect
host, application, and user data for traffic on your network. You can use certain types of
discovery and identity data to build a comprehensive map of your network assets, perform
forensic analysis, behavioral profiling, access control, and mitigate and respond to the
vulnerabilities and exploits to which your organization is susceptible.The Cisco Advanced
Malware Protection (AMP) solution enables you to detect and block malware, continuously
analyze for malware, and get retrospective alerts. AMP for Networks delivers networkbased
advanced malware protection that goes beyond point-in-time detection to protect
your organization across the entire attack continuum – before, during, and after an attack.
Designed for Cisco Firepower® network threat appliances, AMP for Networks detects,
blocks, tracks, and contains malware threats across multiple threat vectors within a single
system. It also provides the visibility and control necessary to protect your organization
against highly sophisticated, targeted, zero-day, and persistent advanced malware threats.
| Page 32 out of 126 Pages |
| Previous |