
- Email support@dumps4free.com

Topic 1: Exam Pool A
Refer to the exhibit.
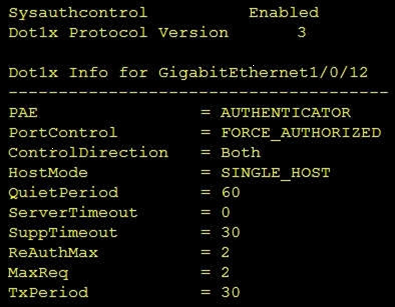
Which command was used to display this output?
A.
show dot1x all
B.
show dot1x
C.
show dot1x all summary
D.
show dot1x interface gi1/0/12
show dot1x all
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for
analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files
which need analysis?
A.
AMP calculates the SHA-256 fingerprint, caches it, and periodically attempts the upload
B.
The file is queued for upload when connectivity is restored
C.
The file upload is abandoned
D.
The ESA immediately makes another attempt to upload the file
The file upload is abandoned
https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118796-technoteesa-00.htmlIn this question, it stated “the network is congested”
(not the file analysis server was overloaded) so theappliance will not try to upload the file again.
A user has a device in the network that is receiving too many connection requests from
multiple machines.
Which type of attack is the device undergoing?
A.
phishing
B.
slowloris
C.
pharming
D.
SYN flood
SYN flood
Which license is required for Cisco Security Intelligence to work on the Cisco Next
Generation Intrusion Prevention System?
A.
control
B.
malware
C.
URL filtering
D.
protect
protect
What is the Cisco API-based broker that helps reduce compromises, application risks, and
data breaches in an environment that is not on-premise?
A.
Cisco Cloudlock
B.
Cisco Umbrella
C.
Cisco AMP
D.
Cisco App Dynamics
Cisco Cloudlock
Cisco Cloudlock is a cloud-native cloud access
security broker (CASB) that helps you move to the cloud safely.It protects your cloud users,
data, and apps. Cisco Cloudlock provides visibility and compliance checks,protects data
against misuse and exfiltration, and provides threat protections against malware like
ransomware.
| Page 30 out of 126 Pages |
| Previous |