
- Email support@dumps4free.com

Topic 2: Exam Pool B
Which method is used to deploy certificates and configure the supplicant on mobile devices
to gain access to
network resources?
A.
BYOD on boarding
B.
Simple Certificate Enrollment Protocol
C.
Client provisioning
D.
MAC authentication bypass
BYOD on boarding
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
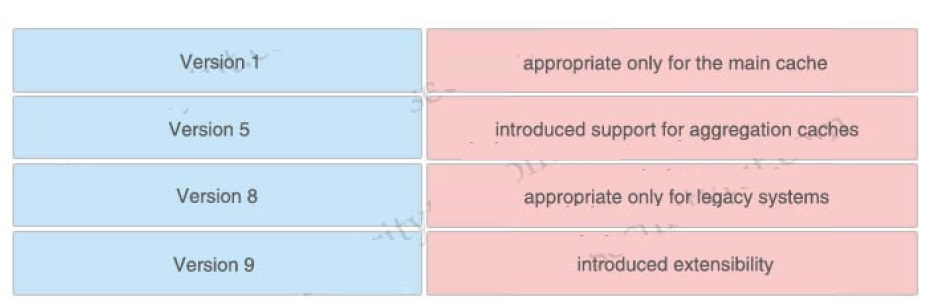
Which two risks is a company vulnerable to if it does not have a well-established patching solution for endpoints? (Choose two)
A.
exploits
B.
ARP spoofing
C.
denial-of-service attacks
D.
malware
E.
eavesdropping
exploits
malware
Malware means “malicious software”, is any software
intentionally designed to cause damage to a computer, server, client, or computer network.
The most popular types of malware includes viruses, ransomware and spyware. Virus
Possibly the most common type of malware, viruses attach their malicious code to clean
code and wait to be run.
Ransomware is malicious software that infects your computer and displays messages
demanding a fee to be paid in order for your system to work again.Spyware is spying
software that can secretly record everything you enter, upload, download, and store on
your computers or mobile devices. Spyware always tries to keep itself hidden.An exploit is
a code that takes advantage of a software vulnerability or security flaw.Exploits and
malware are two risks for endpoints that are not up to date. ARP spoofing and
eavesdropping are attacks against the network while denial-of-service attack is based on
the flooding of IP packets.
Refer to the exhibit.

When configuring a remote access VPN solution terminating on the Cisco ASA, an
administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication
using machine
certificates. Which configuration item must be modified to allow this?
A.
Group Policy
B.
Method
C.
SAML Server
D.
DHCP Servers
Method
In order to use AAA along with an external token
authentication mechanism, set the “Method” as “Both” inthe Authentication.
An engineer is implementing NTP authentication within their network and has configured
both the client and server devices with the command ntp authentication-key 1 md5
Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2,
however it is unable to do so. Which command is required to enable the client to accept the
server’s authentication key?
A.
ntp peer 1.1.1.1 key 1
B.
ntp server 1.1.1.1 key 1
C.
ntp server 1.1.1.2 key 1
D.
ntp peer 1.1.1.2 key 1
ntp server 1.1.1.1 key 1
To configure an NTP enabled router to require
authentication when other devices connect to it, use thefollowing
commands:NTP_Server(config)#ntp authentication-key 2 md5
securitytutNTP_Server(config)#ntp authenticateNTP_Server(config)#ntp trusted-key 2Then
you must configure the same authentication-key on the client
router:NTP_Client(config)#ntp authentication-key 2 md5 securitytutNTP_Client(config)#ntp
authenticateNTP_Client(config)#ntp trusted-key 2NTP_Client(config)#ntp server 10.10.10.1
key 2Note: To configure a Cisco device as a NTP client, use the command ntp server <IP
address>. For example:Router(config)#ntp server 10.10.10.1. This command will instruct
the router to query 10.10.10.1 for the time.
| Page 26 out of 126 Pages |
| Previous |