
- Email support@dumps4free.com

Topic 2: Exam Pool B
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from
the left onto the correct definitions on the right.

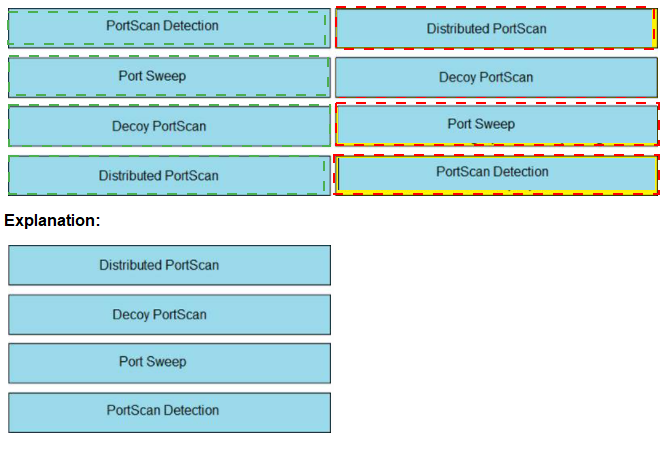
A picture containing table
Description automatically generated
What is a benefit of performing device compliance?
A.
Verification of the latest OS patches
B.
Device classification and authorization
C.
Providing multi-factor authentication
D.
Providing attribute-driven policies
Verification of the latest OS patches
A network engineer is configuring DMVPN and entered the crypto isakmp key
cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
A.
Change isakmp to ikev2 in the command on hostA.
B.
Enter the command with a different password on hostB.
C.
Enter the same command on hostB.
D.
Change the password on hostA to the default password.
Enter the same command on hostB.
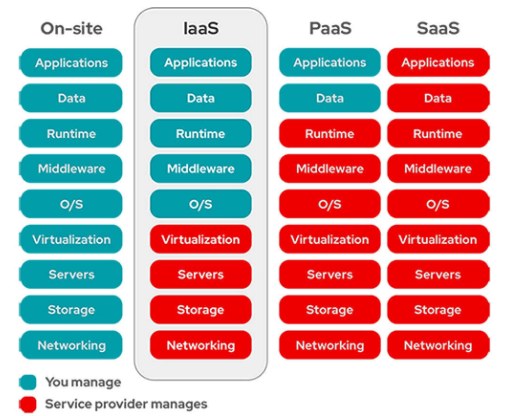
Which two aspects of the cloud PaaS model are managed by the customer but not the
provider? (Choose two)
A.
virtualization
B.
middleware
C.
operating systems
D.
applications
E.
data
applications
data
Customers must manage applications and data in PaaS.
Which type of attack is social engineering?
A.
trojan
B.
phishing
C.
malware
D.
MITM
phishing
Phishing is a form of social engineering. Phishing attacks use
email or malicious web sites to solicit personal,often financial, information. Attackers may send email seemingly from a reputable credit card company orfinancial institution that requests account information, often suggesting that there is a problem.
| Page 22 out of 126 Pages |
| Previous |