
- Email support@dumps4free.com

Topic 1: Exam Pool A
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
A.
phishing
B.
brute force
C.
man-in-the-middle
D.
DDOS
E.
teardrop
brute force
man-in-the-middle
Drag and drop the steps from the left into the correct order on the right to enable
AppDynamics to monitor an EC2 instance in Amazon Web Services

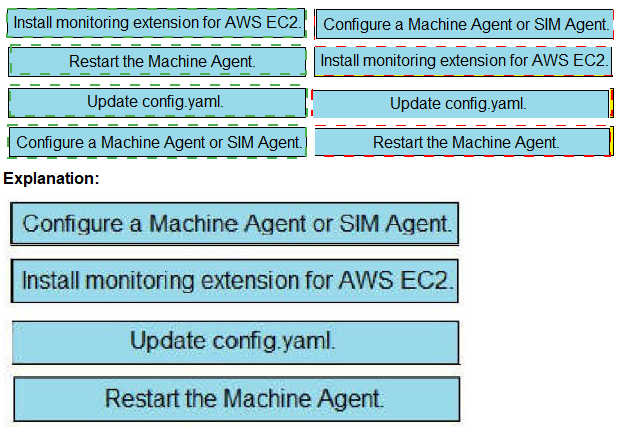
Graphical user interface, text, application, email
Description automatically generated
Refer to the exhibit.
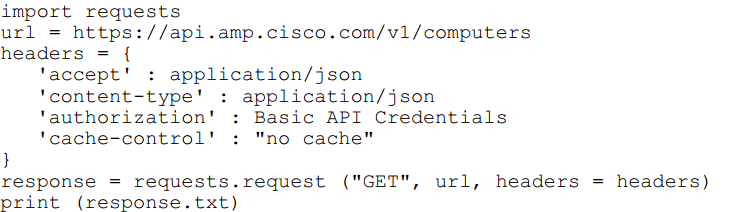
What will happen when this Python script is run?
A.
The compromised computers and malware trajectories will be received from Cisco AMP
B.
The list of computers and their current vulnerabilities will be received from Cisco AMP
C.
The compromised computers and what compromised them will be received from Cisco
AMP
D.
The list of computers, policies, and connector statuses will be received from Cisco AMP
The list of computers, policies, and connector statuses will be received from Cisco AMP
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A.
Port Bounce
B.
CoA Terminate
C.
CoA Reauth
D.
CoA Session Query
CoA Reauth
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity platform. What should be used to meet these requirements?
A.
Cisco Umbrella
B.
Cisco Cloud Email Security
C.
Cisco NGFW
D.
Cisco Cloudlock
Cisco Cloudlock
| Page 19 out of 126 Pages |
| Previous |