
- Email support@dumps4free.com

Topic 1: Exam Pool A
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware?
(Choose two)
A.
Sophos engine
B.
white list
C.
RAT
D.
outbreak filters
E.
DLP
Sophos engine
outbreak filters
Which Cisco platform ensures that machines that connect to organizational networks have
the recommended
antivirus definitions and patches to help prevent an organizational malware outbreak?
A.
Cisco WiSM
B.
Cisco ESA
C.
Cisco ISE
D.
Cisco Prime Infrastructure
Cisco ISE
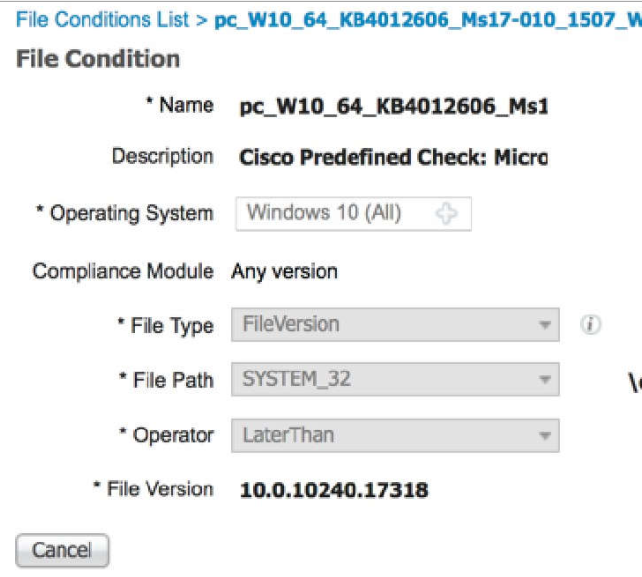
A posture policy is a collection of posture requirements, which
are associated with one or more identity groups, and operating systems. We can configure
ISE to check for the Windows patch at Work Centers > Posture > Posture Elements >
Conditions > File.In this example, we are going to use the predefined file check to ensure
that our Windows 10 clients have the critical security patch installed to prevent the Wanna
Cry malware; and we can also configure ISE to update the client with this patch.
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance?
(Choose two)
A.
configure Active Directory Group Policies to push proxy settings
B.
configure policy-based routing on the network infrastructure
C.
reference a Proxy Auto Config file
D.
configure the proxy IP address in the web-browser settings
E.
use Web Cache Communication Protocol
configure policy-based routing on the network infrastructure
use Web Cache Communication Protocol
What is a benefit of conducting device compliance checks?
A.
It indicates what type of operating system is connecting to the network.
B.
It validates if anti-virus software is installed
C.
It scans endpoints to determine if malicious activity is taking place
D.
It detects email phishing attacks.
It validates if anti-virus software is installed
Which type of algorithm provides the highest level of protection against brute-force attacks?
A.
PFS
B.
HMAC
C.
MD5
D.
SHA
SHA
| Page 17 out of 126 Pages |
| Previous |