
- Email support@dumps4free.com

Topic 1: Exam Pool A
A mall provides security services to customers with a shared appliance. The mall wants separation of management on the shared appliance. Which ASA deployment mode meets these needs?
A.
routed mode
B.
transparent mode
C.
multiple context mode
D.
multiple zone mode
multiple context mode
An organization is using Cisco Firepower and Cisco Meraki MX for network security and
needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
A.
Cisco Defense Orchestrator
B.
Cisco Secureworks
C.
Cisco DNA Center
D.
Cisco Configuration Professional
Cisco Defense Orchestrator
Drag and drop the threats from the left onto examples of that threat on the right
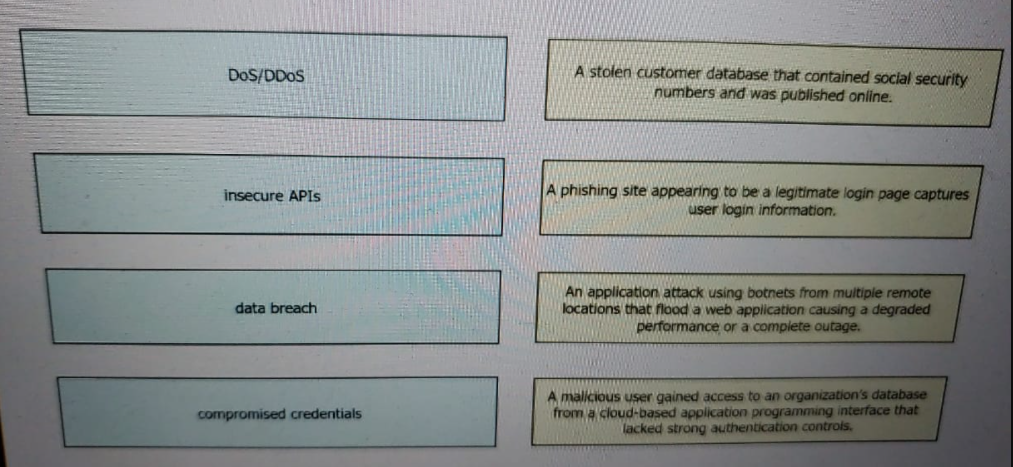
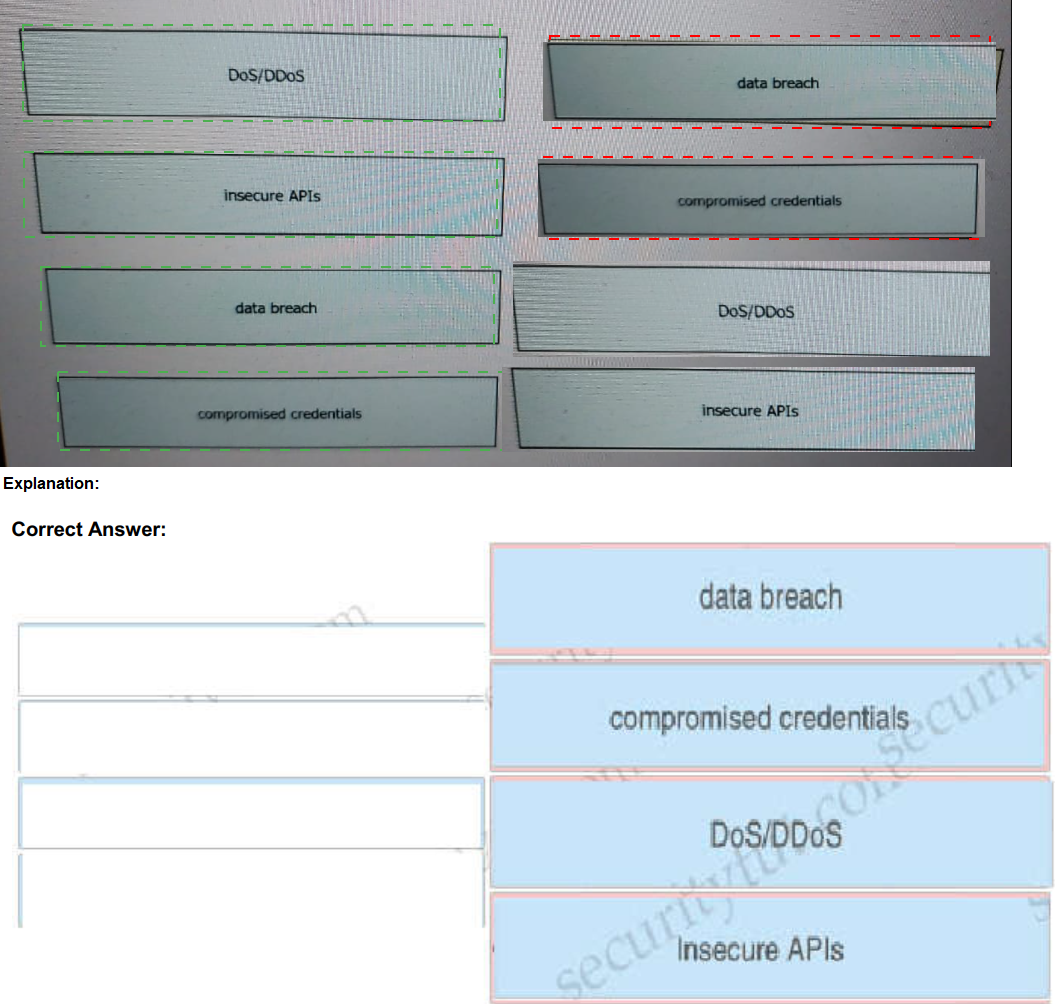
A data breach is the intentional or unintentional release of secure or
private/confidential information to anuntrusted environment.When your credentials have
been compromised, it means someone other than you may be in possession of your
account information, such as your username and/or password.
What is a difference between DMVPN and sVTI?
A.
DMVPN supports tunnel encryption, whereas sVTI does not.
B.
DMVPN supports dynamic tunnel establishment, whereas sVTI does not.
C.
DMVPN supports static tunnel establishment, whereas sVTI does not.
D.
DMVPN provides interoperability with other vendors, whereas sVTI does not.
DMVPN supports dynamic tunnel establishment, whereas sVTI does not.
What is the function of the Context Directory Agent?
A.
maintains users’ group memberships
B.
relays user authentication requests from Web Security Appliance to Active Directory
C.
reads the Active Directory logs to map IP addresses to usernames
D.
accepts user authentication requests on behalf of Web Security Appliance for user
identification
reads the Active Directory logs to map IP addresses to usernames
https://www.cisco.com/c/en/us/td/docs/security/ibf/cda_10/Install_Config_guide/cda10/cda_oveviw.html
| Page 15 out of 126 Pages |
| Previous |