
- Email support@dumps4free.com

Topic 2: Exam Pool B
What is a functional difference between a Cisco ASA and a Cisco IOS router with Zonebased
policy firewall?
A.
The Cisco ASA denies all traffic by default whereas the Cisco IOS router with Zone-
Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces
B.
The Cisco IOS router with Zone-Based Policy Firewall can be configured for high
availability, whereas the Cisco ASA cannot
C.
The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default,
whereas the Cisco ASA starts out by allowing all traffic until rules are added
D.
The Cisco ASA can be configured for high availability whereas the Cisco IOS router with
Zone-Based Policy Firewall cannot
The Cisco ASA denies all traffic by default whereas the Cisco IOS router with Zone-
Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces
An organization has noticed an increase in malicious content downloads and wants to use
Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web
traffic. Which action will accomplish this task?
A.
Set content settings to High
B.
Configure the intelligent proxy
C.
Use destination block lists
D.
Configure application block lists
Configure the intelligent proxy
How is ICMP used an exfiltration technique?
A.
by flooding the destination host with unreachable packets
B.
by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address
C.
by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host
D.
by overwhelming a targeted host with ICMP echo-request packets
by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host
Refer to the exhibit.
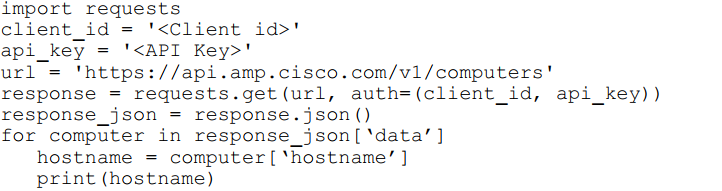
What will happen when the Python script is executed?
A.
The hostname will be translated to an IP address and printed
B.
The hostname will be printed for the client in the client ID field
C.
The script will pull all computer hostnames and print them
D.
The script will translate the IP address to FODN and print it
The script will pull all computer hostnames and print them
After a recent breach, an organization determined that phishing was used to gain initial
access to the network before regaining persistence. The information gained from the
phishing attack was a result of users visiting known malicious websites. What must be
done in order to prevent this from happening in the future?
A.
Modify an access policy
B.
Modify identification profiles
C.
Modify outbound malware scanning policies
D.
Modify web proxy settings
Modify web proxy settings
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmcconfig-
guidev60/Access_Control_Rules__URL_Filtering.html
| Page 14 out of 126 Pages |
| Previous |