
- Email support@dumps4free.com

Topic 2: Exam Pool B
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior
of users?
A.
file access from a different user
B.
interesting file access
C.
user login suspicious behavior
D.
privilege escalation
user login suspicious behavior
Reference: https://www.cisco.com/c/en/us/products/collateral/data-centeranalytics/
tetration-analytics/whitepaper-c11-740380.html
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline posture node?
A.
RADIUS Change of Authorization
B.
device tracking
C.
DHCP snooping
D.
VLAN hopping
RADIUS Change of Authorization
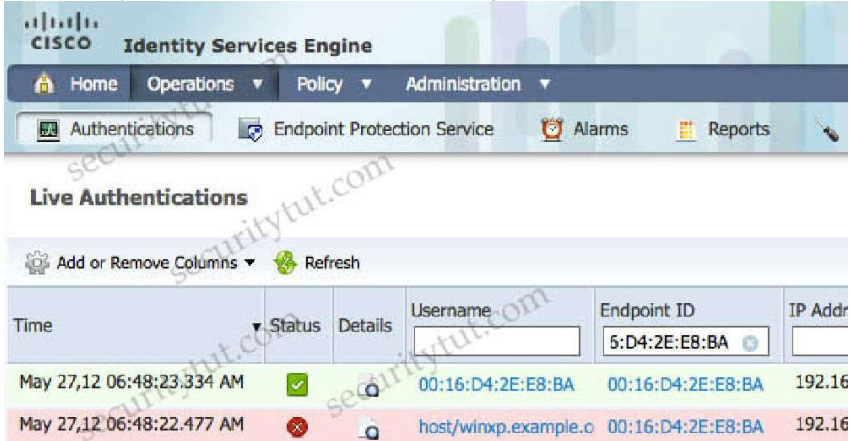
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is
failing
authentication and is unable to access the network. Where should the administrator begin
troubleshooting to verify the authentication details?
A.
Adaptive Network Control Policy List
B.
Context Visibility
C.
Accounting Reports
D.
RADIUS Live Logs
RADIUS Live Logs
How To Troubleshoot ISE Failed Authentications &
AuthorizationsCheck the ISE Live LogsLogin to the primary ISE Policy Administration Node
(PAN).Go to Operations > RADIUS > Live Logs(Optional) If the event is not present in the
RADIUS Live Logs, go to Operations > Reports > Reports >Endpoints and Users >
RADIUS AuthenticationsCheck for Any Failed Authentication Attempts in the Log
An engineer notices traffic interruption on the network. Upon further investigation, it is
learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined
threshold, to
address this issue?
A.
Bridge Protocol Data Unit guard
B.
embedded event monitoring
C.
storm control
D.
access control lists
storm control
Storm control prevents traffic on a LAN from being
disrupted by a broadcast, multicast, or unicast storm on one of the physical interfaces. A
LAN storm occurs when packets flood the LAN, creating excessive traffic and degrading
network performance. Errors in the protocol-stack implementation, mistakes in network
configurations, or users issuing a denial-of-service attack can cause a storm.By using the “
storm-control broadcast level [falling-threshold]” we can limit the broadcast traffic on the
switch.
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
A.
put
B.
options
C.
gets
D.
push
E.
connect
put
gets
The ASA REST API gives you programmatic access to
managing individual ASAs through a Representational State Transfer (REST) API. The API allows external clients to perform CRUD (Create, Read, Update, Delete) operations on ASA resources; it is based on the HTTPS protocol and REST methodology.All API requests are sent over HTTPS to the ASA, and a response is returned.Request StructureAvailable request methods are:GET – Retrieves data from the specified object.PUT – Adds the supplied information to the specified object; returns a 404 Resource Not Found error if the object does not exist.POST – Creates the object with the supplied
information.DELETE – Deletes the specified object
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
| Page 13 out of 126 Pages |
| Previous |