
- Email support@dumps4free.com

Topic 2: Exam Pool B
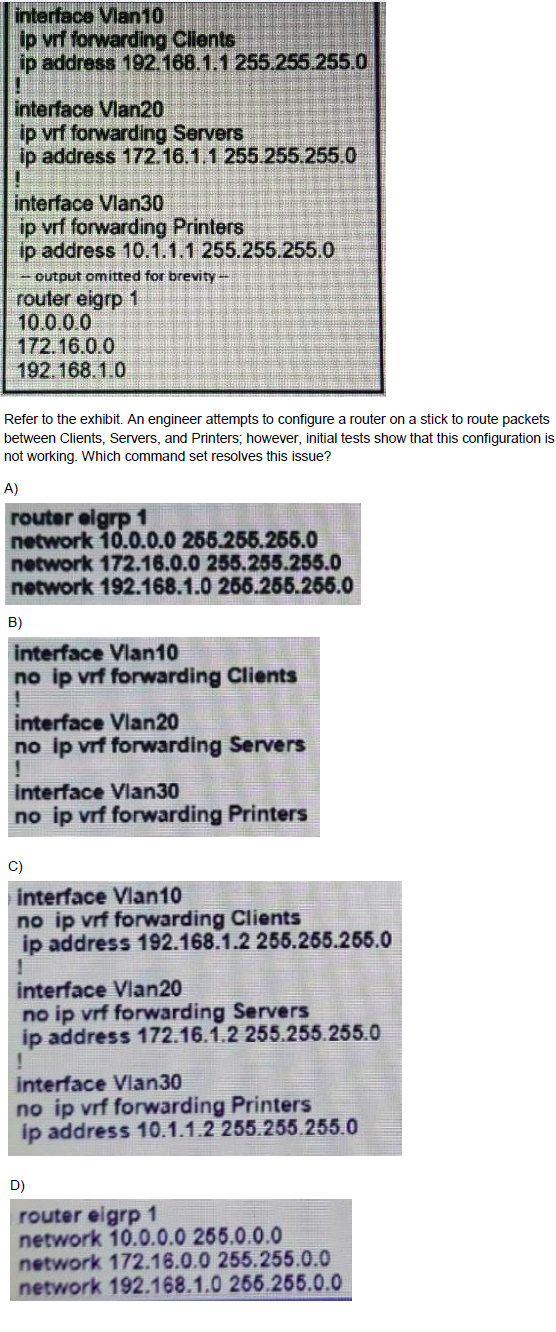
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
We must reconfigure the IP address after assigning or removing an interface to a VRF. Otherwise that interface does not have an IP address.
How cloud deployments differ from on-prem deployments?
A.
Cloud deployments require longer implementation times than on-premises deployments
B.
Cloud deployments are more customizable than on-premises deployments
C.
Cloud deployments require less frequent upgrades than on-premises deployments
D.
Cloud deployments have lower upfront costs than on-premises deployments.
Cloud deployments require less frequent upgrades than on-premises deployments
What does a northbound API accomplish?
A.
programmatic control of abstracted network resources through a centralized controller
B.
access to controlled network resources from a centralized node
C.
communication between SDN controllers and physical switches
D.
controlled access to switches from automated security applications
programmatic control of abstracted network resources through a centralized controller
Refer to the exhibit.
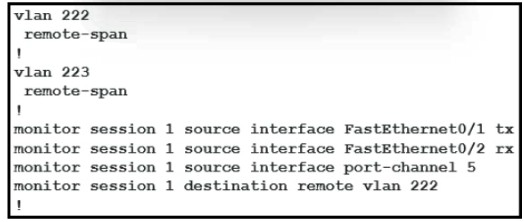
What is the result when a technician adds the monitor session 1 destination remote vlan 223 command1?
A.
The RSPAN VLAN is replaced by VLAN 223.
B.
RSPAN traffic is sent to VLANs 222 and 223
C.
An error is flagged for configuring two destinations.
D.
RSPAN traffic is split between VLANs 222 and 223.
The RSPAN VLAN is replaced by VLAN 223.
How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
A.
Add a timestamp to the request In the API header.
B.
Use a password hash
C.
Add OAuth to the request in the API header
D.
UseHTTPS
Use a password hash
| Page 58 out of 168 Pages |
| Previous |