
- Email support@dumps4free.com

Topic 2: Exam Pool B
What is required for a virtual machine to run?
A.
a Type 1 hypervisor and a host operating system
B.
a hypervisor and physical server hardware
C.
only a Type 1 hypervisor
D.
only a Type 2 hypervisor
a hypervisor and physical server hardware
Which outcome is achieved with this Python code?

A.
connects to a Cisco device using SSH and exports the routing table information
B.
displays the output of the show command in a formatted way
C.
connects to a Cisco device using SSH and exports the BGP table for the prefix
D.
connects to a Cisco device using Telnet and exports the routing table information
connects to a Cisco device using SSH and exports the BGP table for the prefix
Refer to the exhibit.
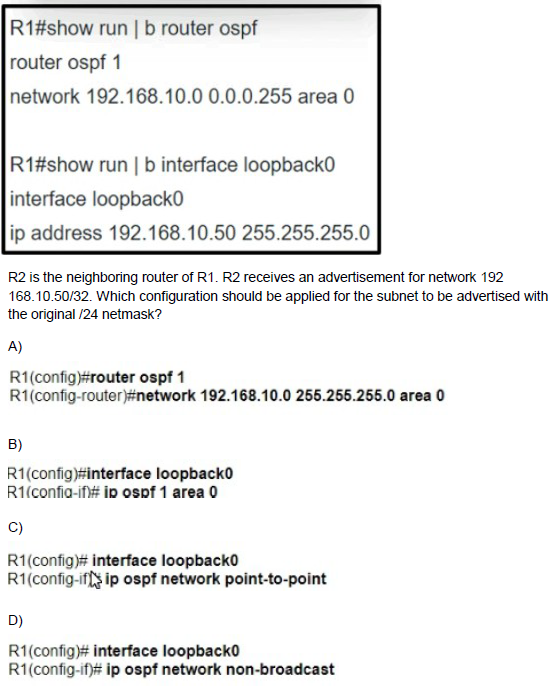
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
Which threat defence mechanism, when deployed at the network perimeter, protects against zero-day attacks?
A.
intrusion prevention
B.
stateful inspection
C.
sandbox
D.
SSL decryption
sandbox
Reference: https://www.cisco.com/c/en/us/products/collateral/security/ampappliances/datasheet-c78-733182.html“File analysis and sandboxing: Secure Malware Analytics’ highly secure environment helps you execute, analyze, and test malware behavior to discover previously unknown ZERO-DAY threats. The integration of Secure Malware Analytics’ sandboxing technology into Malware Defense results in more dynamic analysis checked against a larger set of behavioral indicators. “
Refer to the exhibit.
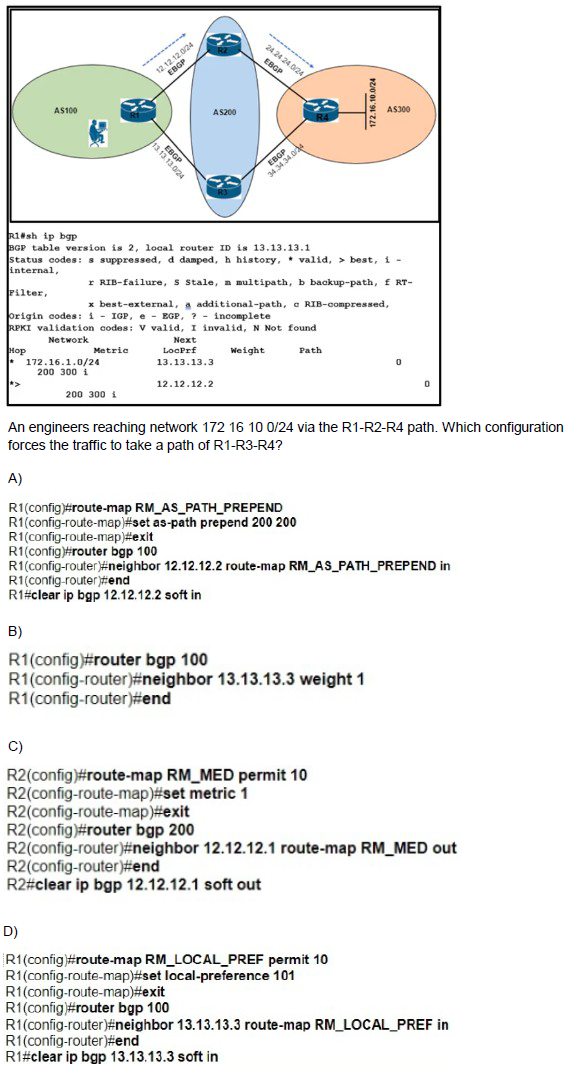
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
| Page 55 out of 168 Pages |
| Previous |