
- Email support@dumps4free.com

Topic 2: Exam Pool B
Refer to the exhibit.
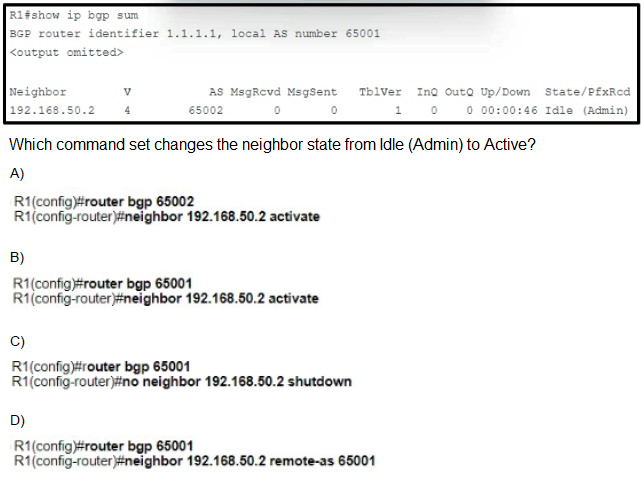
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
How is a data modeling language used?
A.
To enable data lo be easily structured, grouped, validated, and replicated
B.
To represent finite and well-defined network elements that cannot be changed
C.
To model the flows of unstructured data within the infrastructure
D.
To provide human readability to scripting languages
To enable data lo be easily structured, grouped, validated, and replicated
Which feature does Cisco TrustSec use to provide scalable, secure communication throughout a network?
A.
security group tag ACL assigned to each port on a switch
B.
security group tag number assigned to each port on a network
C.
security group tag number assigned to each user on a switch
D.
security group tag ACL assigned to each router on a network
security group tag number assigned to each port on a network
Explanation: Cisco TrustSec uses tags to represent logical group privilege. This tag, called a Security Group Tag (SGT), is used in access policies. The SGT is understood and is used to enforce traffic by Cisco switches, routers and firewalls . Cisco TrustSec is defined in three phases: classification, propagation and enforcement.
When users and devices connect to a network, the network assigns a specific security group. This process is called classification. Classification can be based on the results of the authentication or by associating the SGT with an IP, VLAN, or port-profile (-> Answer 'security group tag ACL assigned to each port on a switch' and answer 'security group tag number assigned to each user on a switch' are not correct as they say “assigned … on a switch” only. Answer 'security group tag ACL assigned to each router on a network' is not correct either as it says “assigned to each router”).
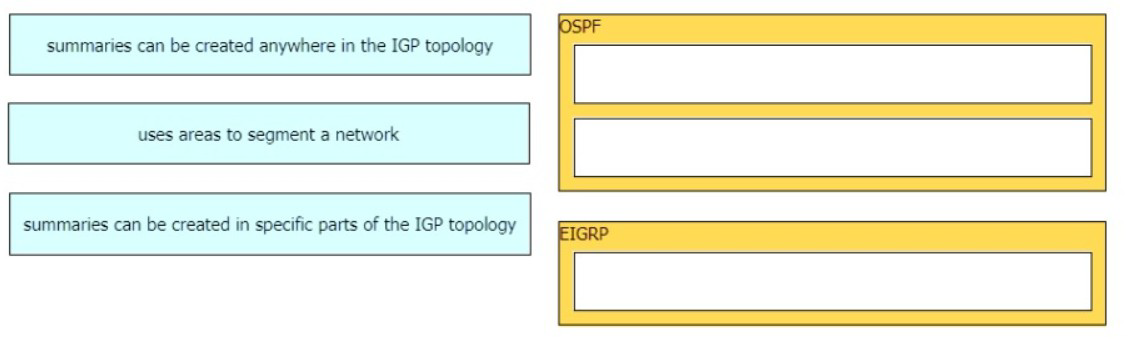
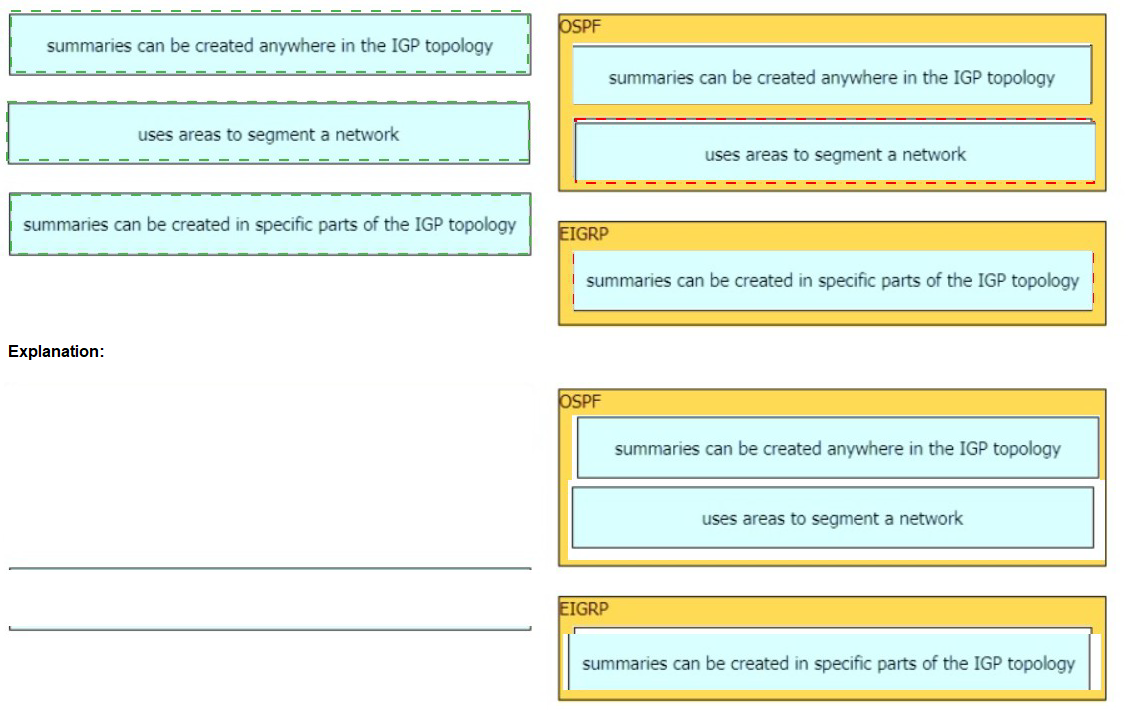
Drag and drop the descriptions from the left onto the routing protocol they describe on the right.
Refer to the exhibit.
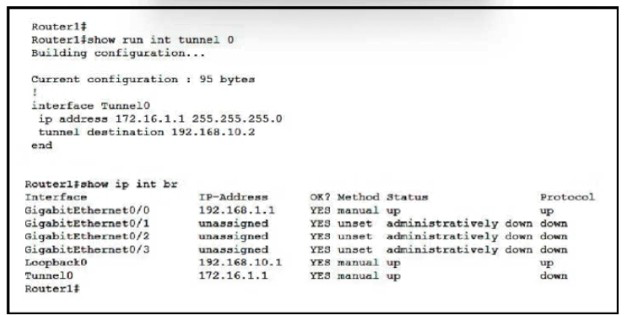
Which command must be applied to Router 1 to bring the GRE tunnel to an up/up state?
A.
Routed (config if funnel mode gre multipoint
B.
Router1(config-if)&tunnel source Loopback0
C.
Router1(config-if)#tunnel source GigabitEthernet0/1
D.
Router1 (config)#interface tunnel0
Router1(config-if)&tunnel source Loopback0
| Page 52 out of 168 Pages |
| Previous |