
- Email support@dumps4free.com

Topic 2: Exam Pool B
What is one primary REST security design principle?
A.
fail-safe defaults
B.
password hash
C.
adding a timestamp in requests
D.
OAuth
fail-safe defaults
Reference: https://yurisubach.com/2017/04/04/restful-api-security-principles/“Fail-safe defaultsAccess to any resource (like API endpoint) should be denied by default. Access granted only in case of specific permission.
What is the structure of a JSON web token?
A.
three parts separated by dots: header payload, and signature
B.
header and payload
C.
three parts separated by dots: version header and signature
D.
payload and signature
three parts separated by dots: header payload, and signature
Explanation: JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
JSON Web Tokens are composed of three parts, separated by a dot (.): Header, Payload, Signature. Therefore, a JWT typically looks like the following:
xxxxx.yyyyy.zzzzz
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA. The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically, the user) and additional data. To create the signature part you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
Reference: https://jwt.io/introduction/
Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A.
Utilize DHCP option 17.
B.
Configure WLC IP address on LAN switch.
C.
Utilize DHCP option 43.
D.
Configure an ip helper-address on the router interface
E.
Enable port security on the switch port
Utilize DHCP option 43.
Enable port security on the switch port
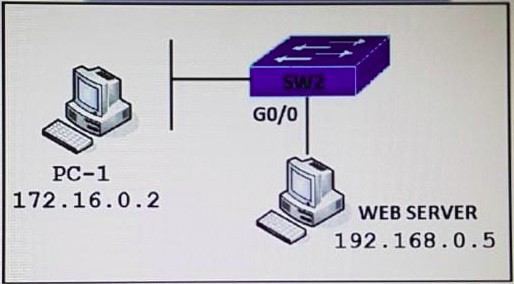
Refer to the exhibit. PC-1 must access the web server on port 8080. To allow this traffic, which statement must be added to an access control list that is applied on SW2 port G0/0 in the inbound direction?
A.
permit host 172.16.0.2 host 192.168.0.5 eq 8080
B.
permit host 192.168.0.5 host 172.16.0.2 eq 8080
C.
permit host 192.168.0.5 eq 8080 host 172.16.0.2
D.
permit host 192.168.0.5 it 8080 host 172.16.0.2
permit host 192.168.0.5 eq 8080 host 172.16.0.2
Explanation: The inbound direction of G0/0 of SW2 only filter traffic from Web Server to PC-1 so the source IP address and port is of the Web Server.
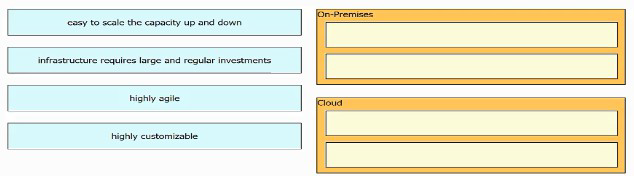
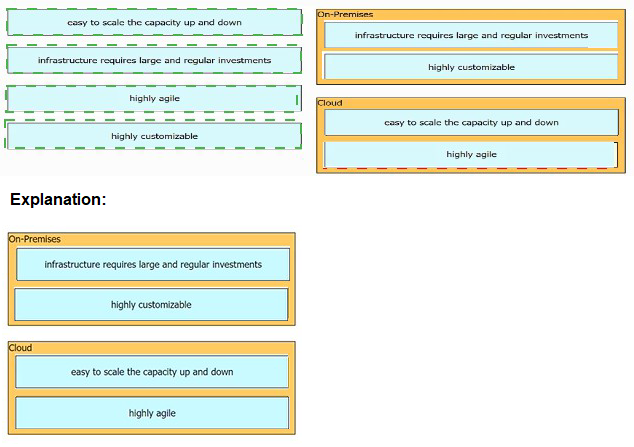
Drag and drop the characteristics from the left onto the infrastructure deployment models they describe on the right.
| Page 50 out of 168 Pages |
| Previous |