
- Email support@dumps4free.com

Topic 1: Exam Pool A
Refer to the exhibit.
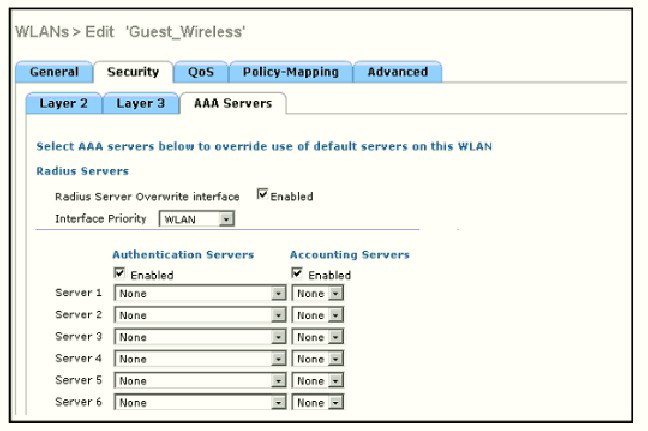
Assuming the WLC's interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
A.
the interface specified on the WLAN configuration
B.
any interface configured on the WLC
C.
the controller management interface
D.
the controller virtual interface
the interface specified on the WLAN configuration
Refer to the Exhibit.
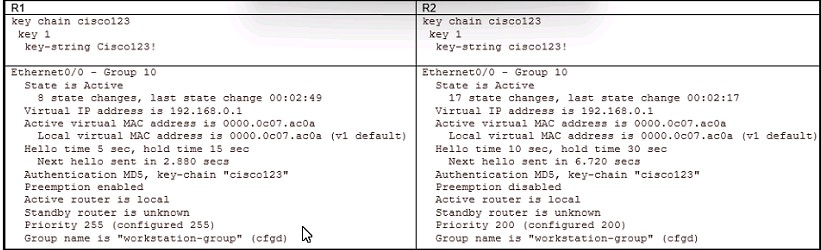
An engineer is installing a new pair of routers in a redundant configuration. When checking on the standby status of each router the engineer notices that the routers are not functioning as expected. Which action will resolve the configuration error?
A.
configure matching hold and delay timers
B.
configure matching key-strings
C.
configure matching priority values
D.
configure unique virtual IP addresses
configure matching key-strings
Explanation:
From the output exhibit, we notice that the key-string of R1 is Cisco123! (letter C is in capital) while that of R2 is cisco123!. This causes a mismatch in the authentication so we have to fix their key-strings. key-string [encryption-type] text-string: Configures the text string for the key. The textstring argument is alphanumeric, case-sensitive, and supports special characters.
Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/6-x/security/configuration/guide/b_Cisco_Nexus_9000_Series_NXOS_Security_Configuration_Guide/b_Cisco_Nexus_9000_Series_NXOS_Security_Configuration_Guide_chapter_01111.pdf
Refer to the exhibit.
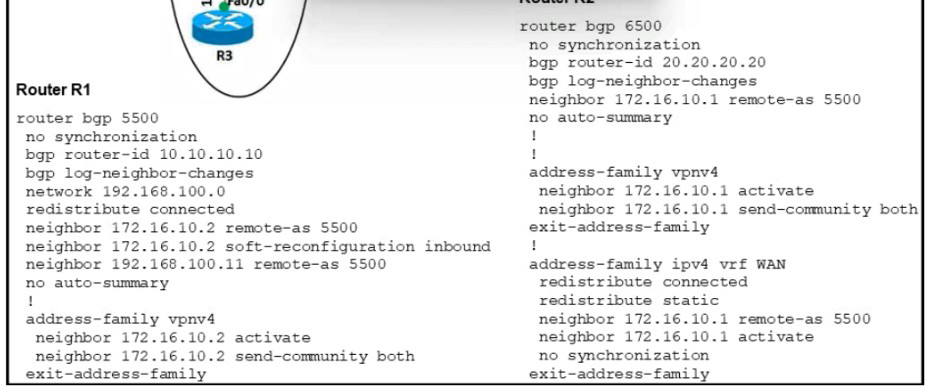
An engineer configures the BGP adjacency between R1 and R2, however, it fails to establish Which action resolves the issue?
A.
Change the network statement on R1 to 172.16 10.0
B.
Change the remote-as number for 192 168.100.11
C.
Enable synchronization on R1 and R2
D.
Change the remote-as number on R1 to 6500.
Change the remote-as number on R1 to 6500.
Which technology uses network traffic telemetry, contextual information, and file reputation to provide insight into cyber threats?
A.
threat defense
B.
security services
C.
security intelligence
D.
segmentation
security intelligence
Which technology is used as the basis for the cisco sd-access data plane?
A.
IPsec
B.
LISP
C.
VXLAN
D.
802.1Q
VXLAN
Explanation: A virtual network identifier (VNI) is a value that identifies a specific virtual network in the data plane.
| Page 39 out of 168 Pages |
| Previous |