
- Email support@dumps4free.com

Topic 1: Exam Pool A
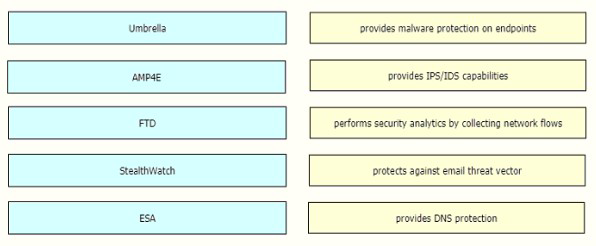
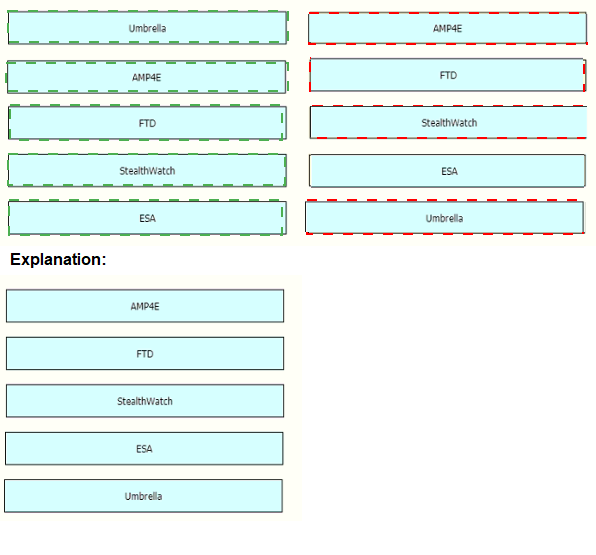
Drag and drop the threat defense solutions from the left onto their descriptions on the right.
An engineer configures HSRP group 37. The configuration does not modify the default virtual MAC address. Which virtual MAC address does the group use?
A.
C0:00:00:25:00:00
B.
00:00:0c:07:ac:37
C.
C0:39:83:25:258:5
D.
00:00:0c:07:ac:25
00:00:0c:07:ac:25
Refer to the exhibit.
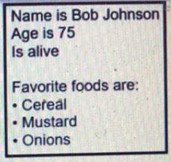
What is the Json syntax that is formed from the data?
A.
{Name: Bob Johnson, Age: 75, Alive: true, Favorite Foods: [Cereal, Mustard, Onions]}
B.
{"Name": "Bob Johnson", "Age": 75, "Alive": true, "Favorite Foods": ["Cereal", "Mustard","Onions"]}
C.
{"˜Name': "˜Bob Johnson', "˜Age': 75, "˜Alive': True, "˜Favorite Foods': "˜Cereal', "˜Mustard', "˜Onions'}
D.
{"Name": "Bob Johnson", "Age": Seventyfive, "Alive": true, "Favorite Foods": ["Cereal","Mustard", "Onions"]}
{"Name": "Bob Johnson", "Age": 75, "Alive": true, "Favorite Foods": ["Cereal", "Mustard","Onions"]}
How does Cisco Trustsec enable more access controls for dynamic networking environments and data centers?
A.
classifies traffic based on advanced application recognition
B.
uses flexible NetFlow
C.
classifies traffic based on the contextual identity of the endpoint rather than its IP address correct
D.
assigns a VLAN to the endpoint
classifies traffic based on the contextual identity of the endpoint rather than its IP address correct
Explanation: The Cisco TrustSec solution simplifies the provisioning and management of network access control through the use of software-defined segmentation to classify network traffic and enforce policies for more flexible access controls. Traffic classification is based on endpoint identity, not IP address, enabling policy change without net-work redesign.
When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
A.
Not all of the controllers in the mobility group are using the same mobility group name.
B.
Not all of the controllers within the mobility group are using the same virtual interface IP address.
C.
All of the controllers within the mobility group are using the same virtual interface IP address.
D.
All of the controllers in the mobility group are using the same mobility group name.
Not all of the controllers within the mobility group are using the same virtual interface IP address.
| Page 31 out of 168 Pages |
| Previous |