
- Email support@dumps4free.com

Topic 1: Exam Pool A
Which protocol does REST API rely on to secure the communication channel?
A.
TCP
B.
HTTPS
C.
SSH
D.
HTTP
HTTPS
Explanation: The REST API accepts and returns HTTP (not enabled by default) or HTTPS messages that contain JavaScript Object Notation (JSON) or Extensible Markup Language (XML) documents. You can use any programming language to generate the messages and the JSON or XML documents that contain the API methods or Managed Object (MO) descriptions.
Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/sw/2-
x/rest_cfg/2_1_x/b_Cisco_APIC_REST_API_Configuration_Guide/b_Cisco_APIC_REST_API_Configuration_Guide_chapter_01.html
Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A.
SHA-512 and SHA-384
B.
MD5 algorithm-128 and SHA-384
C.
SHA-1, SHA-256, and SHA-512
D.
PBKDF2, BCrypt, and SCrypt
PBKDF2, BCrypt, and SCrypt
Explanation: One of the best practices to secure REST APIs is using password hash.
Passwords must always be hashed to protect the system (or minimize the damage) even if it is compromised in some hacking attempts. There are many such hashing algorithms which can prove really effective for password security e.g. PBKDF2, bcrypt and scrypt algorithms.
Other ways to secure REST APIs are: Always use HTTPS, Never expose information on URLs (Usernames, passwords, session tokens, and API keys should not appear in the URL), Adding Timestamp in Request, Using OAuth, Input Parameter Validation.
Reference: https://restfulapi.net/security-essentials/

Refer to the exhibit. What is the effect of this configuration?
A.
When users attempt to connect to vty lines 0 through 4, the device will authenticate them against TACACS+ if local authentication fails
B.
The device will authenticate all users connecting to vty lines 0 through 4 against TACACS+
C.
The device will allow users at 192.168.0.202 to connect to vty lines 0 through 4 using the password ciscotestkey
D.
The device will allow only users at 192.166.0.202 to connect to vty lines 0 through 4
The device will authenticate all users connecting to vty lines 0 through 4 against TACACS+
Refer to the exhibit.
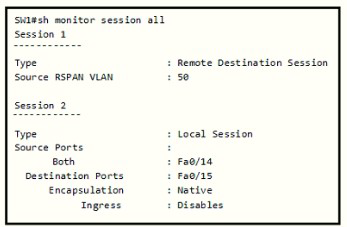
An engineer configures monitoring on SW1 and enters the show command to verify operation. What does the output confirm?
A.
SPAN session 1 monitors activity on VLAN 50 of a remote switch
B.
SPAN session 2 only monitors egress traffic exiting port FastEthernet 0/14.
C.
SPAN session 2 monitors all traffic entering and exiting port FastEthernet 0/15.
D.
RSPAN session 1 is incompletely configured for monitoring
RSPAN session 1 is incompletely configured for monitoring
Explanation: SW1 has been configured with the following commands:
SW1(config)#monitor session 1 source remote vlan 50 SW1(config)#monitor session 2 source interface fa0/14 SW1(config)#monitor session 2 destination interface fa0/15 The session 1 on SW1 was configured for Remote SPAN (RSPAN) while session 2 was configured for local SPAN. For RSPAN we need to configure the destination port to complete the configuration.
Note: In fact we cannot create such a session like session 1 because if we only configure Source RSPAN VLAN 50 (with the command monitor session 1 source remote vlan 50) then we will receive a Type: Remote Source Session (not Remote Destination Session).
Refer to the exhibit.
 Which HTTP JSON response does the python code output give?
Which HTTP JSON response does the python code output give?
A.
NameError: name 'json' is not defined
B.
KeyError 'kickstart_ver_str'
C.
7.61
D.
7.0(3)I7(4)
7.0(3)I7(4)
| Page 27 out of 168 Pages |
| Previous |