
- Email support@dumps4free.com

Topic 1: Exam Pool A
A network administrator has designed a network with two multilayer switches on the distribution layer, which act as default gateways for the end hosts. Which two technologies allow every end host in a VLAN to use both gateways? (Choose two)
A.
GLBP
B.
HSRP
C.
MHSRP
D.
VSS
E.
VRRP
GLBP
MHSRP
How does an on-premises infrastructure compare to a cloud infrastructure?
A.
On-premises can increase compute power faster than cloud
B.
On-premises requires less power and cooling resources than cloud
C.
On-premises offers faster deployment than cloud
D.
On-premises offers lower latency for physically adjacent systems than cloud.
On-premises offers lower latency for physically adjacent systems than cloud.
Refer the exhibit.
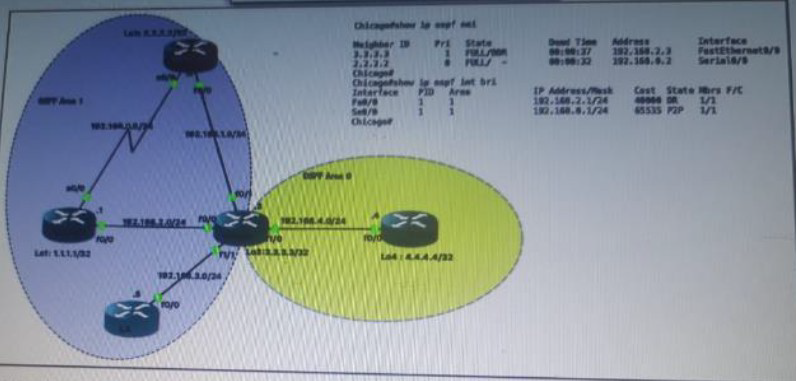
Which router is the designated router on the segment 192.168.0.0/24?
A.
This segment has no designated router because it is a nonbroadcast network type
B.
This segment has no designated router because it is a p2p network type.
C.
Router Chicago because it has a lower router ID
D.
Router NewYork because it has a higher router ID
This segment has no designated router because it is a p2p network type.
Refer to the exhibit.
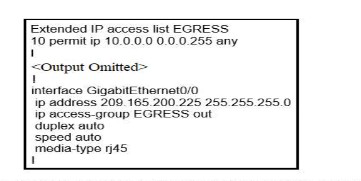
An engineer must block all traffic from a router to its directly connected subnet
209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router However, the router can still ping hosts on the 209.165.200.0/24 subnet. Which explanation of this behavior is true?
A.
Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B.
Only standard access control lists can block traffic from a source IP address.
C.
After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
D.
The access control list must contain an explicit deny to block traffic from the router.
Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.

Refer to the exhibit. An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected. Which action resolves this issue?
A.
Change the access-list destination mask to a wildcard
B.
Change the source network that Is specified in access-list 101.
C.
Change the route-map configuration to VRF_BLUE.
D.
Change the access-list number in the route map
Change the access-list destination mask to a wildcard
| Page 17 out of 168 Pages |
| Previous |