
- Email support@dumps4free.com

Topic 1: Exam Pool A
MX record priority increases as the number increases. (True/False.)
A.
True
B.
False
False
Bob, a system administrator at TPNQM SA, concluded one day that a DMZ is not needed if
he properly configures the firewall to allow access just to servers/ports, which can have
direct internet access, and block the access to workstations.
Bob also concluded that DMZ makes sense just when a stateful firewall is available, which
is not the case of TPNQM SA.
In this context, what can you say?
A.
Bob can be right since DMZ does not make sense when combined with stateless
firewalls
B.
Bob is partially right. He does not need to separate networks if he can create rules by
destination IPs, one by one
C.
Bob is totally wrong. DMZ is always relevant when the company has internet servers
and workstations
D.
Bob is partially right. DMZ does not make sense when a stateless firewall is available
Bob is totally wrong. DMZ is always relevant when the company has internet servers
and workstations
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP
instruction for the Intel processor. You figure that the attacker is attempting a buffer
overflow attack.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst what would you conclude about the attack?
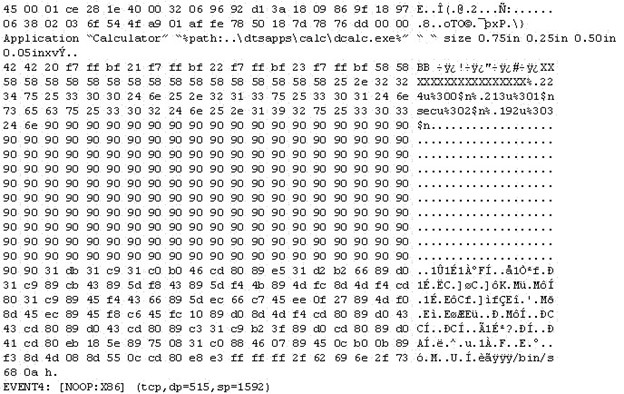
A.
The buffer overflow attack has been neutralized by the IDS
B.
The attacker is creating a directory on the compromised machine
C.
The attacker is attempting a buffer overflow attack and has succeeded
D.
The attacker is attempting an exploit that launches a command-line shell
The attacker is attempting an exploit that launches a command-line shell
If a tester is attempting to ping a target that exists but receives no response or a response
that states the destination is unreachable, ICMP may be disabled and the network may be
using TCP. Which other option could the tester use to get a response from a host using
TCP?
A.
Traceroute
B.
Hping
C.
TCP ping
D.
Broadcast ping
Hping
What is the following command used for?
net use \targetipc$ "" /u:""
A.
Grabbing the etc/passwd file
B.
Grabbing the SAM
C.
Connecting to a Linux computer through Samba
D.
This command is used to connect as a null session
E.
Enumeration of Cisco routers
This command is used to connect as a null session
| Page 25 out of 114 Pages |
| Previous |