
- Email support@dumps4free.com

Topic 1: Exam Pool A
A network administrator discovers several unknown files in the root directory of his Linux
FTP server. One of the files is a tarball, two are shell script files, and the third is a binary
file is named "nc." The FTP server's access logs show that the anonymous user account
logged in to the server, uploaded the files, and extracted the contents of the tarball and ran
the script using a function provided by the FTP server's software. The “ps” command
shows that the “nc” file is running as process, and the netstat command shows the “nc”
process is listening on a network port.
What kind of vulnerability must be present to make this remote attack possible?
A.
File system permissions
B.
Privilege escalation
C.
Directory traversal
D.
Brute force login
File system permissions
Explanation:
File system permissions
Processes may automatically execute specific binaries as part of their functionality or to
perform other actions. If the permissions on the file system directory containing a target
binary, or permissions on the binary itself, are improperly set, then the target binary may be
overwritten with another binary using user-level permissions and executed by the original
process. If the original process and thread are running under a higher permissions level,
then the replaced binary will also execute under higher-level permissions, which could
include SYSTEM.
Adversaries may use this technique to replace legitimate binaries with malicious ones as a
means of executing code at a higher permissions level. If the executing process is set to
run at a specific time or during a certain event (e.g., system bootup) then this technique
can also be used for persistence.
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.)
A.
200303028
B.
3600
C.
604800
D.
2400
E.
60
F.
4800
2400
Study the following log extract and identify the attack.
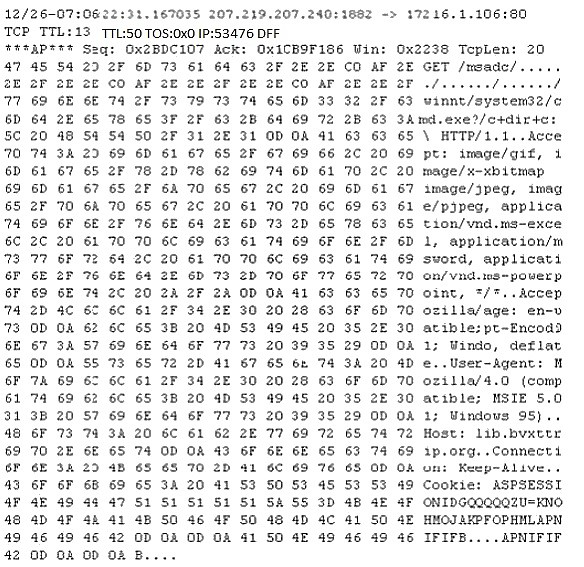
A.
Hexcode Attack
B.
Cross Site Scripting
C.
Multiple Domain Traversal Attack
D.
Unicode Directory Traversal Attack
Unicode Directory Traversal Attack
What tool can crack Windows SMB passwords simply by listening to network traffic?
A.
This is not possible
B.
Netbus
C.
NTFSDOS
D.
L0phtcrack
L0phtcrack
Eve is spending her day scanning the library computers. She notices that Alice is using a
computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate
Alice machine. From the command prompt, she types the following command.

What is Eve trying to do?
A.
Eve is trying to connect as a user with Administrator privileges
B.
Eve is trying to enumerate all users with Administrative privileges
C.
Eve is trying to carry out a password crack for user Administrator
D.
Eve is trying to escalate privilege of the null user to that of Administrator
Eve is trying to carry out a password crack for user Administrator
| Page 22 out of 114 Pages |
| Previous |